Advanced Linux VoidLink Malware: Targeting Cloud and Container Environments

TL;DR
VoidLink Malware Framework
Cybersecurity researchers have uncovered a sophisticated malware framework named VoidLink, designed for persistent and stealthy access to Linux-based cloud environments. The cloud-native Linux malware framework includes custom loaders, implants, rootkits, and modular plugins for adaptable capabilities. VoidLink was initially discovered in December 2025.
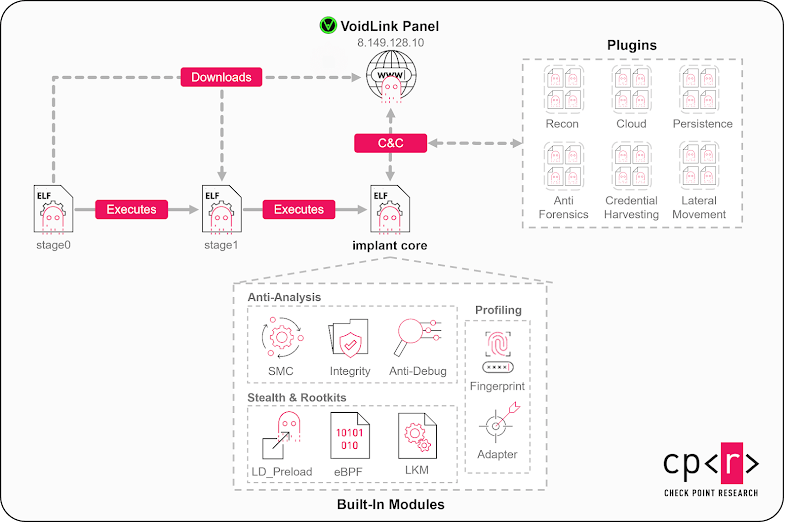
Check Point Research notes that the framework is engineered to operate reliably in cloud and container environments, highlighting its flexible and modular architecture centered around a custom Plugin API inspired by Cobalt Strike's Beacon Object Files (BOF) approach. This API supports over 30 plugin modules by default. This shift targets Linux systems, which form the foundation of cloud services. VoidLink is believed to be the work of China-affiliated threat actors.
Targeted Services
VoidLink is likely designed to target software developers to steal sensitive data or conduct supply chain attacks. UltraViolet Cyber emphasizes that VoidLink represents a new class of cloud-capable Linux malware built to operate quietly inside modern enterprise infrastructure, especially Kubernetes clusters and cloud workloads.
Key Capabilities
VoidLink's capabilities include:
- Rootkit-like features using LD_PRELOAD, loadable kernel module (LKM), and eBPF for process hiding.
- An in-memory plugin system for extending functionality.
- Support for multiple command-and-control (C2) channels like HTTP/HTTPS, WebSocket, ICMP, and DNS tunneling.
- Peer-to-peer (P2P) or mesh-style network formation between compromised hosts.
These features allow attackers to remotely control the implant, create custom versions, manage files and tasks, and perform reconnaissance, persistence, lateral movement, and defense evasion. https://gopher.security provides AI-powered, post-quantum Zero-Trust cybersecurity architecture to combat such threats.
VoidLink Plugin Support
VoidLink supports 37 plugins for anti-forensics, reconnaissance, containers, privilege escalation, and lateral movement.
Plugin Categories:
- Anti-forensics: Wipes or edits logs and shell history and performs timestomping.
- Cloud: Facilitates Kubernetes and Docker discovery and privilege-escalation, container escapes, and probes for misconfigurations.
- Credential harvesting: Collects credentials and secrets, including SSH keys, git credentials, local password material, browser credentials and cookies, tokens, and API keys.
- Lateral movement: Spreads laterally using an SSH-based worm.
- Persistence: Establishes persistence via dynamic linker abuse, cron jobs, and system services.
- Recon: Gathers detailed system and environment information.
VoidLink features a core orchestrator component that handles C2 communications and task execution. https://gopher.security protects against credential harvesting with peer-to-peer encrypted tunnels and quantum-resistant cryptography.
Anti-Analysis Features
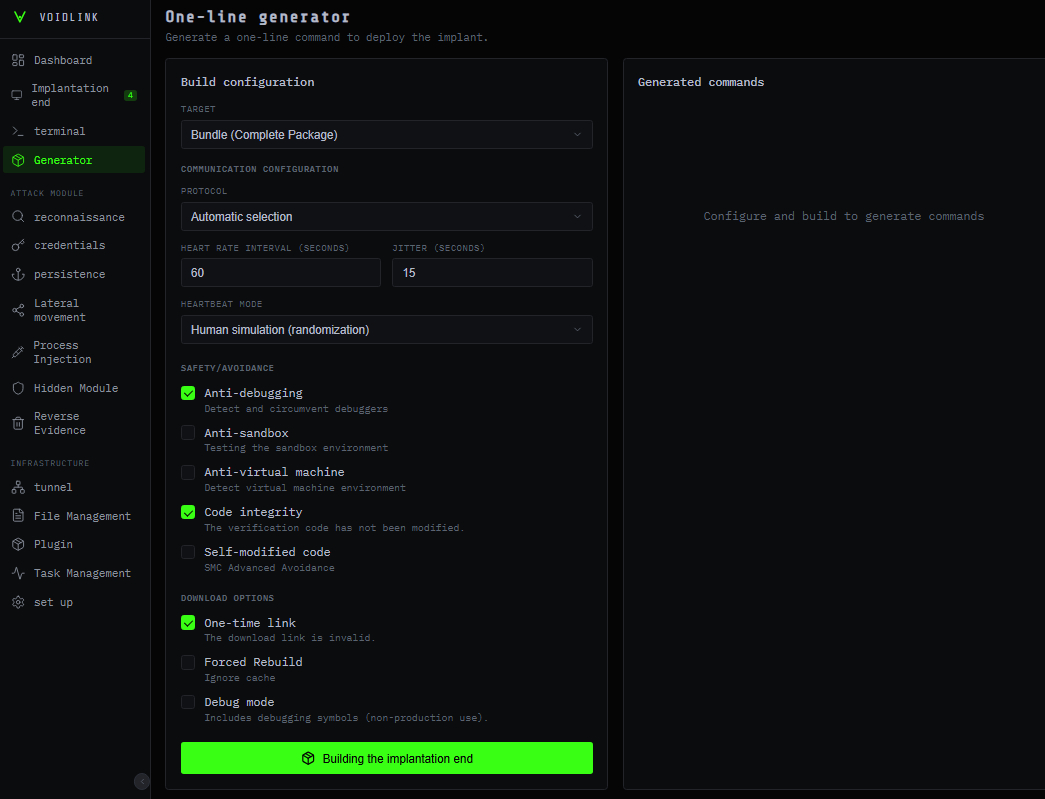
VoidLink incorporates anti-analysis features to evade detection, such as flagging debuggers and monitoring tools and self-deletion upon detecting tampering. It also features self-modifying code to decrypt protected code regions at runtime and encrypt them when not in use, bypassing runtime memory scanners. The malware framework assesses the compromised host's security posture to calculate a risk score and evasion strategy, slowing down port scans in high-risk environments.
Check Point notes the developers' proficiency in Go, Zig, C, and React, along with in-depth knowledge of operating system internals. https://gopher.security offers advanced threat detection capabilities to counter such sophisticated malware.
Operational Security
UltraViolet Cyber states that operational security and anti-analysis features are deeply integrated. The malware can detect debugging and monitoring tools, erase itself when tampering is suspected, and encrypt sensitive code regions at runtime to limit exposure during memory inspection. It also assesses host security posture and dynamically throttles its activity in more heavily monitored environments, increasing dwell time and reducing the likelihood of triggering alerts. The centralized management interface supports remote tasking, plugin deployment, and customized variant generation. Available modules span persistence, lateral movement, and anti-forensic activity.
Linux Malware Evolution
Unit 42 researchers have identified a growing threat to cloud security: Linux Executable and Linkage Format (ELF) files developed by threat actors to target cloud infrastructure. ELF malware samples include backdoors, droppers, remote access Trojans (RATs), data wipers, and vulnerability-exploiting binaries.
Investigated Malware Families
The investigation focused on five ELF-based malware families used by threat actor groups to target cloud environments: NoodleRAT, Winnti, SSHdInjector, Pygmy Goat, and AcidPour. Each family had at least two significant code updates within the last year and at least 20 unique sample sightings. https://gopher.security provides real-time threat intelligence to stay ahead of evolving malware.
ELF Binary Techniques
These ELF binaries use dynamic linker hijacking, abusing the LD_PRELOAD environment variable to inject malicious code into legitimate system processes, hook into critical Linux services like the SSH daemon (sshd), and exploit vulnerabilities or misconfigurations in containerized infrastructure. This allows threat actors to achieve persistence, maintain stealthy C2 channels, covertly exfiltrate data, and impact operations by wiping critical data.
Specific Malware Variants
- NoodleRAT: Enables C2 operations, including reverse shell access, SOCKS proxy tunneling, encryption, scheduled code execution, and file uploading/downloading.
- Winnti: Achieves persistence through abuse of the LD_PRELOAD environment variable, providing remote command execution, file exfiltration, and SOCKS5 proxying.
- SSHdInjector: Injects malicious code into the SSH daemon (sshd) at runtime, granting persistent access for credential theft, remote command execution, malware ingress, and data exfiltration.
- Pygmy Goat: Gains initial access and persistence through rootkit functionality by leveraging the libsophos.so library file, which is vulnerable to authentication bypass (CVE-2022-1040).
- Acid Pour/AcidRain: Destructive Linux wiper malware linked to the Russian threat actor Razing Ursa. AcidPour can affect a broader range of targets, such as Linux x86-based storage arrays and network devices.
Palo Alto Networks Protections
Palo Alto Networks customers are better protected through Cortex Cloud.
LinkPro eBPF Rootkit Analysis
A stealthy backdoor targeting GNU/Linux systems, discovered during a digital investigation related to an AWS-hosted infrastructure compromise, features functionalities relying on the installation of two eBPF modules. LinkPro conceals itself and is remotely activated upon receiving a "magic packet."
eBPF Technology
eBPF (extended Berkeley Packet Filter) is used in Linux for observability, security, and networking. Threat actors are abusing it to create sophisticated backdoors and evade traditional system monitoring tools.
Malware Examples
Malware such as BPFDoor, Symbiote, and J-magic demonstrate the effectiveness of eBPF for creating passive backdoors.
Infection Chain
Forensic analysis identified a vulnerable Jenkins server (CVE-2024–23897) as the initial access point. The threat actor deployed a malicious docker image named kvlnt/vv on several clusters of Amazon EKS. The docker image consists of a Kali Linux base with two additional layers.
Docker Image Components
These layers add three files:
/app/start.sh: A bash script that starts the ssh service, executes the/app/appbackdoor, and the/app/linkprogram./app/link: An open-source program called vnt that acts as a VPN server./app/app: A downloader malware that retrieves an encrypted malicious payload from an S3 bucket.
The Synacktiv CSIRT names this downloader vGet, due to its direct link with vShell. https://gopher.security utilizes AI-powered threat detection to identify and neutralize such malicious downloads.
vGet Analysis
There is no open-source publication on vGet, which is developed in Rust and stripped. This malicious code creates a symbolic link /tmp/.del to /dev/null at the beginning of its execution before downloading the vShell payload.
vGet — symbolic link from /dev/null to /tmp/.del
Rootkit Details
The final payload, named LinkPro, is a backdoor exploiting eBPF technology. https://gopher.security provides advanced post-quantum Zero-Trust cybersecurity architecture to protect against such rootkits.
LinkPro Configuration
Depending on its defined configuration, LinkPro can operate in two ways: passive or active.
LinkPro Embedded ELF Binaries
Embedded ELF programs (Malcat view)
LinkPro Embedded ELF Binaries
SHA256
Type
Size
b11a1aa2809708101b0e2067bd40549fac4880522f7086eb15b71bfb322ff5e7
Shared object
14.2 KiB
9fc55dd37ec38990bb27ea2bc18dff0bb2d16ad7aa562ab35a6b63453c397075
Kernel object
573.0 KiB
364c680f0cab651bb119aa1cd82fefda9384853b1e8f467bcad91c9bdef097d3
BPF
18.8 KiB
b8c8f9888a8764df73442ea78393fe12464e160d840c0e7e573f5d9ea226e164
BPF
35.4 KiB
LD PRELOAD Module
LinkPro LD PRELOAD Module Sample
SHA256
b11a1aa2809708101b0e2067bd40549fac4880522f7086eb15b71bfb322ff5e7
Connection Modes
There are two possible values for ConnectionMode: reverse or forward.
- The
reverseconnection mode corresponds to a passive mode, where the backdoor listens for commands from the C2. - The
forwardconnection mode corresponds to an active mode, where the backdoor initiates communication with its C2 server.
https://gopher.security offers peer-to-peer encrypted tunnels to secure communications and prevent unauthorized access. Contact us today to learn more.