FBI Seizes RAMP Ransomware Forum in Major Cybercrime Crackdown

TL;DR
FBI Seizes RAMP Cybercrime Forum
The FBI has seized control of the RAMP cybercrime forum, a platform known for facilitating ransomware operations. The seizure was a collaborative effort involving the FBI, the US Attorney’s Office for the Southern District of Florida, and the US Justice Department’s Computer Crime and Intellectual Property Section (CCIPS).
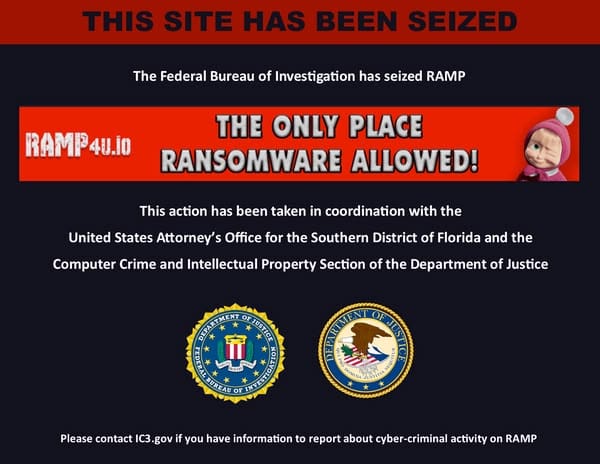
The forum's dark web and regular website domains now display a notice indicating the takeover by law enforcement. The seizure banner includes a winking Masha from the Russian children's TV series "Masha and the Bear," seemingly taunting the forum's operators. RAMP's nameservers now point to ns1.fbi.seized.gov and ns2.fbi.seized.gov, confirming the seizure.
RAMP's Rise and Fall
RAMP (Russian Anonymous MarketPlace) emerged in mid-2021, quickly gaining popularity after major Russian-language hacking forums banned ransomware-related content. This followed increased scrutiny after the Colonial Pipeline attack by the DarkSide gang.
RAMP became a hub for:
- Recruiting ransomware affiliates
- Selling compromised business network credentials by initial access brokers
- Trading stolen data and tools
Infamous ransomware groups like ALPHV/BlackCat, Qilin, DragonForce, and RansomHub used RAMP to promote their activities. The forum boasted over 14,000 users, requiring either proof of activity on other hacking forums or a $500 fee for membership. According to Rapid7, in the summer of 2024, RAMP had revenues of around $250,000.
Key Personnel and Impact
One of RAMP's key figures, Mikhail Matveev (also known as "Orange", "Wazawaka", and "BorisElcin"), was placed on the FBI's most wanted list and arrested in Russia in 2024.
Following the seizure, another alleged operator, "Stallman," acknowledged the takedown on another hacking forum, stating, "This event destroyed years of my work to create the most free forum in the world... This is the risk we all take." Stallman's post indicates that cybercriminal activities will likely continue through other channels.
This takedown represents a significant disruption to cybercriminal infrastructure, forcing threat actors to adapt and potentially exposing them to new security risks. Authorities may now have access to user data, including email and IP addresses, which could lead to further arrests.
Forum Details and Aftermath
RAMP was founded in 2012 and rebranded in 2021. It served Russian, Chinese, and English speakers, offering discussion groups, cyberattack tutorials, and a marketplace for malware and services. The platform had strict vetting processes, including a $500 fee for anonymous participation.
The seizure notice encourages individuals to submit tips through the FBI’s IC3 portal. DNS records confirm that the RAMP domain servers now belong to the FBI.
RAMP's Origins and Key Players
The RAMP cybercrime forum emerged in July 2021 after popular Russian-speaking forums like Exploit and XSS prohibited ransomware promotion due to increased law enforcement pressure following the Colonial Pipeline attack.
RAMP was launched by "Orange" (Mikhail Matveev), previously an administrator for the Babuk ransomware operation. Matveev confirmed his role in creating RAMP in an interview with Recorded Future. In 2023, Matveev was indicted by the U.S. Department of Justice for his involvement in ransomware operations like Babuk, LockBit, and Hive.
Enhance Your Organization's Security Posture with Gopher Security
The RAMP forum takedown highlights the ongoing need for robust cybersecurity measures. As threat actors adapt, organizations must enhance their defenses with advanced security solutions. Gopher Security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture. Our platform converges networking and security across devices, apps, and environments—from endpoints and private networks to cloud, remote access, and containers—using peer-to-peer encrypted tunnels and quantum-resistant cryptography.
Explore our services or contact us to learn how Gopher Security can protect your organization from evolving cyber threats.