Gopher Email: Defend Against Email Compromise with Advanced Lockdown Security

TL;DR
- Gopher Email delivers advanced security for email communications by integrating micro-segmentation, Zero Trust principles, and quantum-resistant encryption. This innovative solution ensures bulletproof protection against phishing, malware, and unauthorized access, safeguarding business operations in an evolving threat landscape.
Summary
Email communication is one of the most targeted avenues for phishing attacks, ransomware, and credential compromises. Traditional email security measures are often insufficient to handle these sophisticated threats, especially with the rise of remote work, hybrid environments, and cloud adoption. Gopher Email offers an innovative solution to lock down email communication, leveraging micro-segmentation, Zero Trust security, and quantum-resistant encryption to bulletproof against phishing attacks. This blog explores how Gopher Email outperforms traditional email security solutions, ensuring that your email network is protected against insider and outsider threats. Another good read is Enhance Email Security: Best Practices to Prevent Phishing and Credential Compromise.
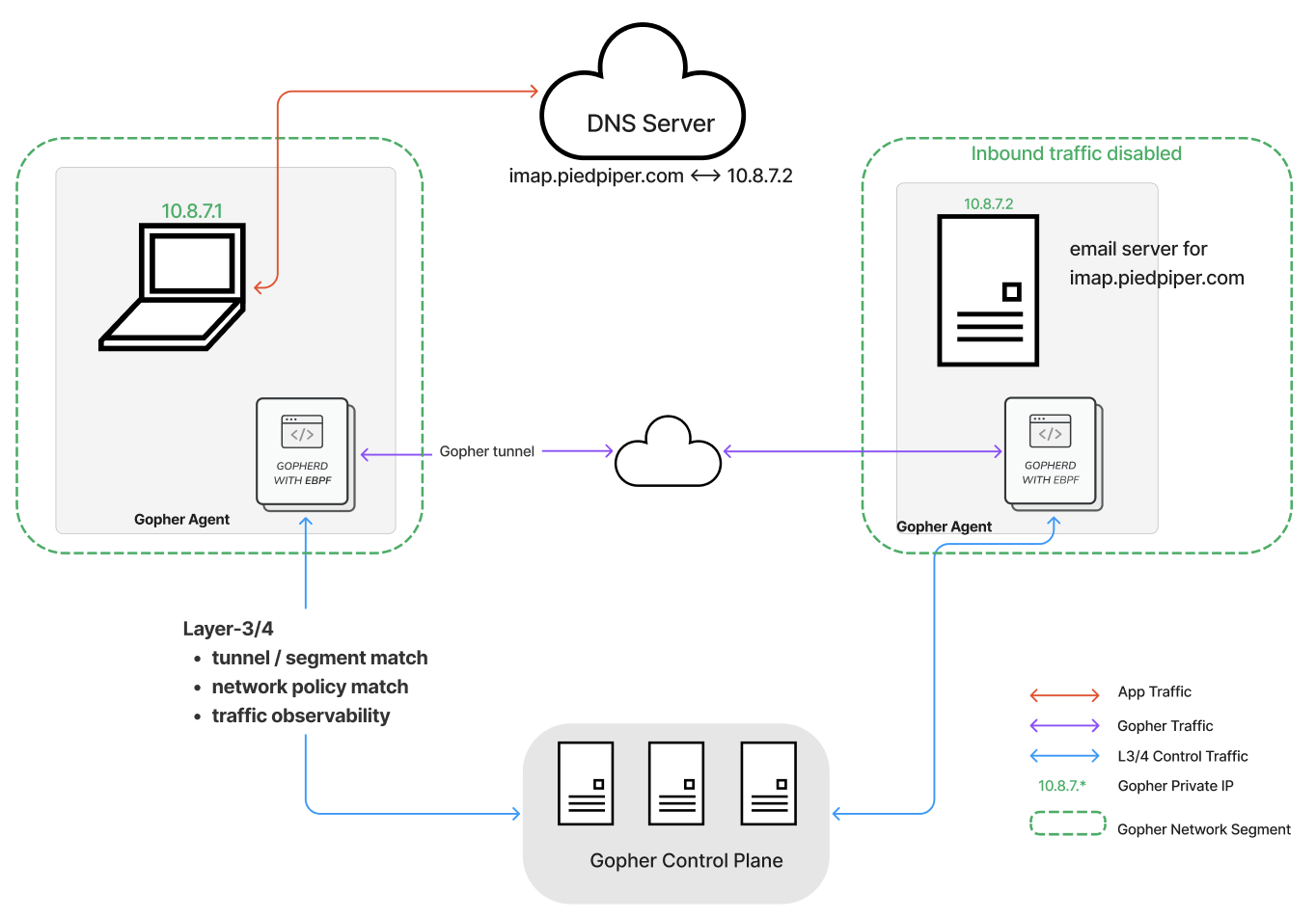
Gopher Email: Lock Down Email Server To Defend Against Credential Compromise, Powered by Gopher Private IP and Quantum-safe Micro-segmentation
What is Email Security?
Email security refers to the methods and techniques used to protect email communication from unauthorized access, interception, and other security threats like phishing, malware, and ransomware. It encompasses various strategies, including encryption, authentication, and access controls, aimed at securing both the sending and receiving of email messages.
Why Do You Need Secure Email?
In today's landscape, secure email is critical because emails are often the first line of attack for cybercriminals. Phishing attacks, ransomware, and stolen credentials commonly originate through email. With the rise of remote work and cloud adoption, traditional email security models have become inadequate in safeguarding against these evolving threats.
Email Security Challenges:
Phishing Attacks: Fraudulent emails designed to steal sensitive information or install malicious software.
Ransomware: Malicious emails with attachments that encrypt data, holding it hostage for ransom.
Compromised Credentials: Emails with links to fake login pages that trick users into disclosing passwords.
Remote Work & Hybrid Environments: The expansion of remote access increases the risk of unauthorized email access.
Traditional Approach to Email Security
The traditional way of securing email typically involves:
Public IPs: Email servers are connected to the public internet, making them more vulnerable to attack.
Basic Firewalls: Designed to block unauthorized access but not sophisticated phishing or malware attacks.
Antivirus & Spam Filters: Detect and block known malware and suspicious emails, but are ineffective against zero-day threats.
User Training: Relying on educating users to recognize phishing attempts, which is often not enough to stop advanced attacks.
Gopher Email: Innovative Email Security Approach vs. Traditional Approaches
1/ Use Gopher Private IP vs. Public IP
Traditional Email Security:
In traditional systems, email servers often use public IP addresses for email reception and transmission, making them accessible and vulnerable to external threats.
Gopher Email:
Gopher Email secures email servers by using Gopher private IPs. These private IPs are exclusive to the Gopher network and not exposed to the public internet, significantly reducing the risk of attacks. This approach ensures email communication is insulated from external threats.
Customer Value:
By using Gopher private IPs, your email servers are shielded from external access, preventing unauthorized entities from exploiting your communication channels.
2/ Micro-Segmentation for Email Servers
Traditional Email Security:
Typically, email servers are integrated within a larger network and can interact with various applications, increasing the potential for security breaches from lateral movement.
Gopher Email:
Gopher Email uses micro-segmentation to isolate email servers in their own network segment. Only email-specific traffic is allowed, while other applications are restricted from accessing these servers unless they are part of the same segment.
Customer Value:
Micro-segmentation ensures that email servers remain secure by isolating them from other applications, minimizing attack surfaces and preventing lateral movement of threats.
3/ Invite-Only Email Network Access
Traditional Email Security:
Anyone with the correct credentials can access email servers, but these credentials can easily be phished or compromised, leading to unauthorized access.
Gopher Email:
With Gopher Email, only individuals who have been explicitly invited to the email network can access email servers. Unauthorized users are automatically blocked, even if they obtain login credentials.
Customer Value:
Gopher Email eliminates unauthorized access by ensuring only authorized, invited users can access your email network.
4/ Role/Group-Based Access Control
Traditional Email Security:
In traditional email systems, role-based access is limited, and employees may be given access beyond what is necessary, leading to potential misuse or exposure of sensitive data.
Gopher Email:
Gopher Email allows administrators to define and enforce role or group-based access control. This means only specific users or groups can access certain email servers, reducing unnecessary access and maintaining strict control.
Customer Value:
By implementing role/group-based access control, Gopher Email ensures employees have access only to the emails and resources they need, reducing the risk of internal threats and data breaches.
5/ Attribute-Based Access Control for Dynamic Requirements
Traditional Email Security:
Traditional systems lack dynamic controls for access, offering rigid security policies that do not accommodate temporary or conditional access needs.
Gopher Email:
Gopher Email supports attribute-based access control (ABAC), allowing email administrators to define access based on various conditions such as time-bound access for contractors, location, device type, or identity match.
Customer Value:
With ABAC, businesses can ensure that access is granted only under specific conditions, offering flexibility while maintaining security.
6/ Context-Aware Endpoints Authentication
Traditional Email Security:
Basic username-password authentication methods are prone to phishing and are often the weakest point in traditional email security.
Gopher Email:
Gopher Email enforces context-aware authentication, verifying the user’s identity based on contextual factors like IP address, device fingerprint, and location. Even if credentials are compromised, unauthorized access is blocked.
Customer Value:
Context-aware authentication protects your email system from unauthorized access by ensuring that only trusted and verified devices can connect.
7/ Quantum-Resistant End-to-End Encryption
Traditional Email Security:
Traditional email systems typically use SSL/TLS encryption. While effective, it’s still vulnerable to certain types of attacks, including advanced man-in-the-middle scenarios.
Gopher Email:
Gopher Email provides quantum-resistant end-to-end encryption, ensuring email communication is protected against even the most advanced threats, including future quantum-based attacks.
Customer Value:
With quantum-resistant encryption, Gopher Email future-proofs your email security, ensuring your communications remain secure from modern and future attacks.
8/ Built-In Zero Trust and SASE Capabilities
Traditional Email Security:
Traditional email systems rely on perimeter-based security models, assuming trust within the network and providing minimal protection from insider threats.
Gopher Email:
Gopher Email incorporates built-in Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) capabilities, ensuring continuous verification of users and devices, as well as strict policy enforcement.
Customer Value:
By adopting a zero-trust approach, Gopher Email minimizes both insider and outsider threats, ensuring that every access request is scrutinized and validated.
9/ Disable Inbound Traffic to Email Network
Traditional Email Security:
In traditional setups, email servers accept inbound traffic from the public internet, which exposes them to brute-force attacks, malware, and unauthorized access.
Gopher Email:
Gopher Email disables all inbound traffic to the email network, protecting email servers from external threats. Only secure Gopher tunnels can transmit email traffic, ensuring a locked-down communication environment.
Customer Value:
Disabling inbound traffic provides bulletproof protection for email servers, significantly reducing the risk of phishing attacks, malware, and unauthorized access.
Inheriting Gopher’s Out-of-the-Box Security
Gopher Email leverages Gopher’s out-of-the-box security features, providing advanced protection from Layer-3/4, offering a unique set of benefits that surpass traditional email security solutions. Below are the key security features and how they translate into customer value.
Enforcing Tunnel Match at Layer-3/4
Customer Value: Ensure that only legitimate and secure tunnels are established, reducing the risk of unauthorized access and data breaches.
Gopher Email enforces tunnel matches at both Layer-3 (network layer) and Layer-4 (transport layer), ensuring that all data passing through is tightly controlled and validated. Legacy email solutions, which often lack this level of control, leave traffic vulnerable to unauthorized access.
Enforcing Policy Match at Layer-3/4
Customer Value: Maintain strict compliance with organizational policies, ensuring that all network traffic adheres to predefined security rules.
With Gopher Email, policy matches are enforced at both Layer-3 and Layer-4. This ensures that all email communication is governed by company-defined security policies. Traditional email security approaches often fail to enforce policies at multiple layers, leading to security gaps.
Enforcing Network Segment Match at Layer-3/4
Customer Value: Protect against lateral data breaches by ensuring that network segments are isolated and secure.
Gopher Email uses micro-segmentation at Layer-3/4, isolating each network segment, including email servers, from other parts of the infrastructure. This isolation prevents any potential breach from spreading across the network, unlike legacy email solutions, which do not offer this level of segmentation.
Traffic Observability at Layer-3/4
Customer Value: Gain complete visibility into network traffic to detect anomalies, optimize performance, and ensure compliance.
Gopher Email provides traffic observability at Layer-3/4, enabling organizations to monitor all email-related traffic in real-time and detect suspicious activity. This contrasts with legacy email systems that often have limited visibility, making it difficult to detect intrusions or data leaks.
Quantum-Resistant End-to-End Encryption
Customer Value: Future-proof your network security by protecting against emerging quantum computing threats, ensuring data integrity and confidentiality.
Gopher Email offers quantum-resistant encryption to safeguard all email communications from man-in-the-middle attacks. Unlike traditional encryption methods, this advanced level of protection ensures that your communications remain secure even against future threats posed by quantum computing.
Pluggable Framework to Extend Data Plane
Customer Value: Adapt to evolving security needs by extending email security capabilities without replacing the entire system.
Gopher Email’s pluggable framework allows organizations to extend and upgrade the system as needed. It ensures that the security features evolve with your business needs, unlike legacy systems that are often rigid and difficult to upgrade.
Disabling Inbound Traffic to Prevent External Threats
Customer Value: Protect the network by restricting inbound traffic and allowing only authorized connections, reducing exposure to external threats.
Gopher Email can disable inbound traffic entirely, allowing only Gopher tunnels with NAT traversal to communicate. This feature significantly reduces exposure to external threats, offering far more protection than legacy email systems that leave ports open to attack.
Conclusion
Gopher Email offers a robust, innovative solution for securing email communications. With features like private IPs, micro-segmentation, zero-trust security, and quantum-resistant encryption, Gopher Email provides the tools needed to protect against the ever-evolving landscape of cyber threats. Whether your business is operating in the cloud, a hybrid environment, or across multiple test and production environments, Gopher Email simplifies security while ensuring bulletproof protection.
Final Thoughts and Recommendation
Email communication is a critical aspect of every business, but it’s also a primary target for cyberattacks. Gopher Email offers a secure, future-proof solution that helps businesses lock down their email communications against phishing, malware, and unauthorized access. By adopting Gopher Email, businesses can safeguard sensitive information, streamline operations, and ensure compliance with the latest security standards. We highly recommend Gopher Email for businesses looking to secure their email communications in a complex, evolving threat landscape.





