Gopher Hybrid: Simplify Your Cloud and On-premises Connection With P2P & Mesh Networking

TL;DR
- Gopher Hybrid empowers enterprises with seamless, on-demand P2P connectivity for your VPC across cloud and on-premises environments, offering unparalleled flexibility, security, and scalability through innovative peer-to-peer and mesh networking.
Summary
In today’s rapidly evolving technological landscape, connecting cloud and on-premises environments is crucial for enterprise flexibility, security, and scalability. Traditional methods like VPC peering and site-to-site VPNs are cumbersome and inflexible, limiting businesses' ability to respond to changing needs. Gopher Hybrid introduces a revolutionary approach, leveraging peer-to-peer (P2P) and mesh networking to create seamless, on-demand connections across cloud and hybrid environments. This blog explores the benefits of Gopher Hybrid, highlighting its innovative features and the significant customer value it delivers. Another good read is Universal Connectivity: Hybrid Multi-Cloud Mesh Networks with Zero Trust Security.
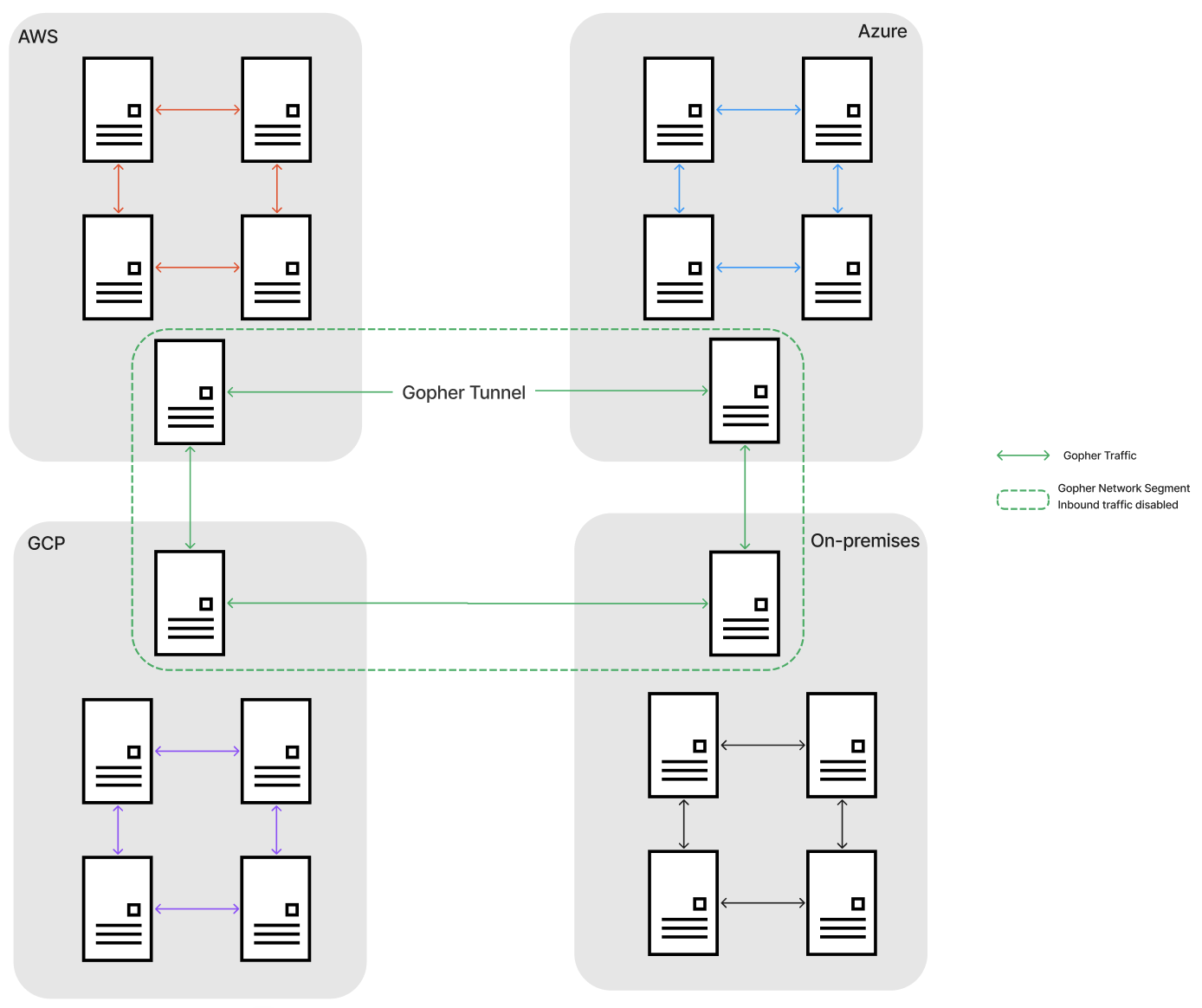
Gopher Hybrid: P2P & Mesh Connect Hybrid & Multi-Cloud, Powered by Gopher Quantum-safe Micro-segmentation
What Are Hybrid and Cloud Environments?
Hybrid environments combine on-premises infrastructure with cloud services, allowing businesses to enjoy the benefits of both. This setup provides flexibility, cost efficiency, and scalability. Common examples include a company using its data center for critical workloads while leveraging public clouds like AWS or Azure for additional capacity, or a multi-cloud strategy where different cloud providers are used for specific tasks to optimize performance and cost.
Traditional Methods: VPC Peering and Site-to-Site VPNs
VPC Peering: In traditional setups, VPC peering connects two Virtual Private Clouds (VPCs) directly within the same cloud provider. This method allows data to flow between VPCs but requires manual setup and is limited by the static nature of the connections.
Site-to-Site VPNs: Site-to-site VPNs create a secure tunnel between on-premises networks and cloud environments. However, they are often complex to configure, involve significant overhead, and can introduce latency and bandwidth limitations due to the centralization of traffic through VPN gateways.
Customer Value: While these traditional methods have been effective in the past, they lack the flexibility and efficiency required by modern enterprises, particularly those operating in dynamic cloud and hybrid environments.
Gopher Hybrid: On-Demand P2P and Mesh Connectivity
1. On-Demand Connectivity: Human, On-Premises, and Multi-Cloud
Traditional Method: Establishing connections between on-premises infrastructure, cloud environments, and multiple clouds usually requires manual configuration and maintenance of static links, which can be time-consuming and prone to errors.
Gopher Hybrid: Gopher Hybrid enables on-demand connectivity between human users, on-premises systems, and multiple cloud environments with a few clicks. This seamless integration removes the friction associated with traditional setups, providing hassle-free and frictionless connectivity.
Customer Value: Businesses can quickly adapt to changing needs without being bogged down by the complexities of traditional networking, resulting in more agile and responsive IT operations.
2. No VPC Peering and Site-to-Site VPNs Required
Traditional Method: VPC peering and site-to-site VPNs require complex configurations and ongoing management, often leading to significant IT overhead and potential bottlenecks in data flow.
Gopher Hybrid: By eliminating the need for VPC peering and site-to-site VPNs, Gopher Hybrid simplifies network management. Leveraging Gopher P2P, the solution provides all the benefits of peer-to-peer connectivity, such as reduced latency, enhanced security, and unlimited bandwidth, without the limitations of traditional methods.
Customer Value: This innovation reduces the cost and complexity of maintaining network connections, freeing up resources for other strategic initiatives.
3. Peer-to-Peer Connections Instead of VPN and Proxying Traffic
Traditional Method: VPNs and proxying traffic introduce latency and bandwidth limitations due to their centralized nature, often leading to degraded performance.
Gopher Hybrid: Gopher Hybrid uses peer-to-peer connections, allowing direct communication between nodes. This approach bypasses the limitations of VPNs and proxies, offering low latency, high performance, and enhanced security.
Customer Value: Direct P2P connections improve application performance and user experience, enabling businesses to operate more efficiently.
4. Mesh Connections Instead of Point-to-Point Links
Traditional Method: Point-to-point links are prone to failure and require manual reconfiguration if the network topology changes, making them inflexible and difficult to scale.
Gopher Hybrid: With Gopher Hybrid, mesh networking is employed, allowing dynamic and resilient connections between nodes. The network automatically reroutes traffic if a node fails, ensuring continuous connectivity.
Customer Value: Mesh networking provides greater reliability and scalability, reducing downtime and improving the overall robustness of the network.
5. Quick Setup with Gopher Control Plane
Traditional Method: Setting up network connections traditionally involves complex configurations and manual interventions, leading to longer deployment times.
Gopher Hybrid: Gopher Hybrid simplifies the process by allowing connections to be established quickly and easily through the Gopher control plane. A few clicks are all it takes to set up secure, efficient network links.
Customer Value: This quick setup capability accelerates deployment times, enabling businesses to respond faster to new opportunities and challenges.
6. Enforced Access Control
Traditional Method: Access control in traditional networks is often broad and difficult to enforce consistently, leading to potential security vulnerabilities.
Gopher Hybrid: Gopher Hybrid enforces strict access control by ensuring that communication between nodes is only possible if they hold mutually agreed-upon keys. Corporate admins centrally manage these keys, ensuring compliance with security policies.
Customer Value: Enhanced security and compliance reduce the risk of unauthorized access, protecting sensitive data and systems.
7. End-to-End Encryption
Traditional Method: Many traditional networks do not offer true end-to-end encryption, leaving data vulnerable as it traverses the network.
Gopher Hybrid: Gopher Hybrid provides end-to-end encryption for all communications. Each node generates a key pair, and communication is encrypted with the private key and decrypted with the public key of the corresponding node.
Customer Value: This encryption ensures that data remains secure throughout its journey, meeting regulatory requirements and building trust with customers and partners.
8. Quantum-Resistant Communication
Traditional Method: Traditional encryption methods are increasingly vulnerable to quantum computing attacks, which could compromise data security in the near future.
Gopher Hybrid: Gopher Hybrid employs a two-phase handshake protocol, using quantum-resistant algorithms to ensure that even in a post-quantum world, your communications remain secure. The protocol is based on the Noise Protocol, combined with the Crystal-Kyber protocol for key encapsulation.
Customer Value: Future-proofing your network with quantum-resistant encryption ensures long-term security, safeguarding your business against emerging threats.
Conclusion
Gopher Hybrid represents a significant leap forward for enterprises seeking to connect their cloud and on-premises environments seamlessly and securely. By leveraging the power of peer-to-peer and mesh networking, Gopher Hybrid offers unparalleled flexibility, scalability, and security compared to traditional methods like VPC peering and site-to-site VPNs.
Final Thoughts and Recommendation
In an age where agility and security are paramount, Gopher Hybrid stands out as a leading solution for dynamic network management. Its innovative features, from on-demand connectivity to quantum-resistant encryption, provide enterprises with the tools they need to stay competitive and secure. We highly recommend Gopher Hybrid as a strategic investment in your network infrastructure, ensuring that your business is well-equipped to face the challenges of today and tomorrow.





