Gopher Unpublish: Lock Down Your Mission-Critical Web Applications with Advanced Protection

TL;DR
Summary
In today's increasingly complex digital landscape, securing mission-critical web applications has become a top priority for enterprises. Traditional methods like VPNs have proven insufficient against modern threats, especially in cloud and hybrid environments. Gopher Unpublish offers a revolutionary approach to web application security by privatizing public-facing apps, ensuring they remain inaccessible without authorized access through dedicated, encrypted tunnels. This blog explores the importance of locking down web applications, compares traditional and innovative security methods, and highlights the unique customer value provided by Gopher Unpublish. Another good read is Protect Your Web Applications: Innovative Strategies to Block Unauthorized Access.
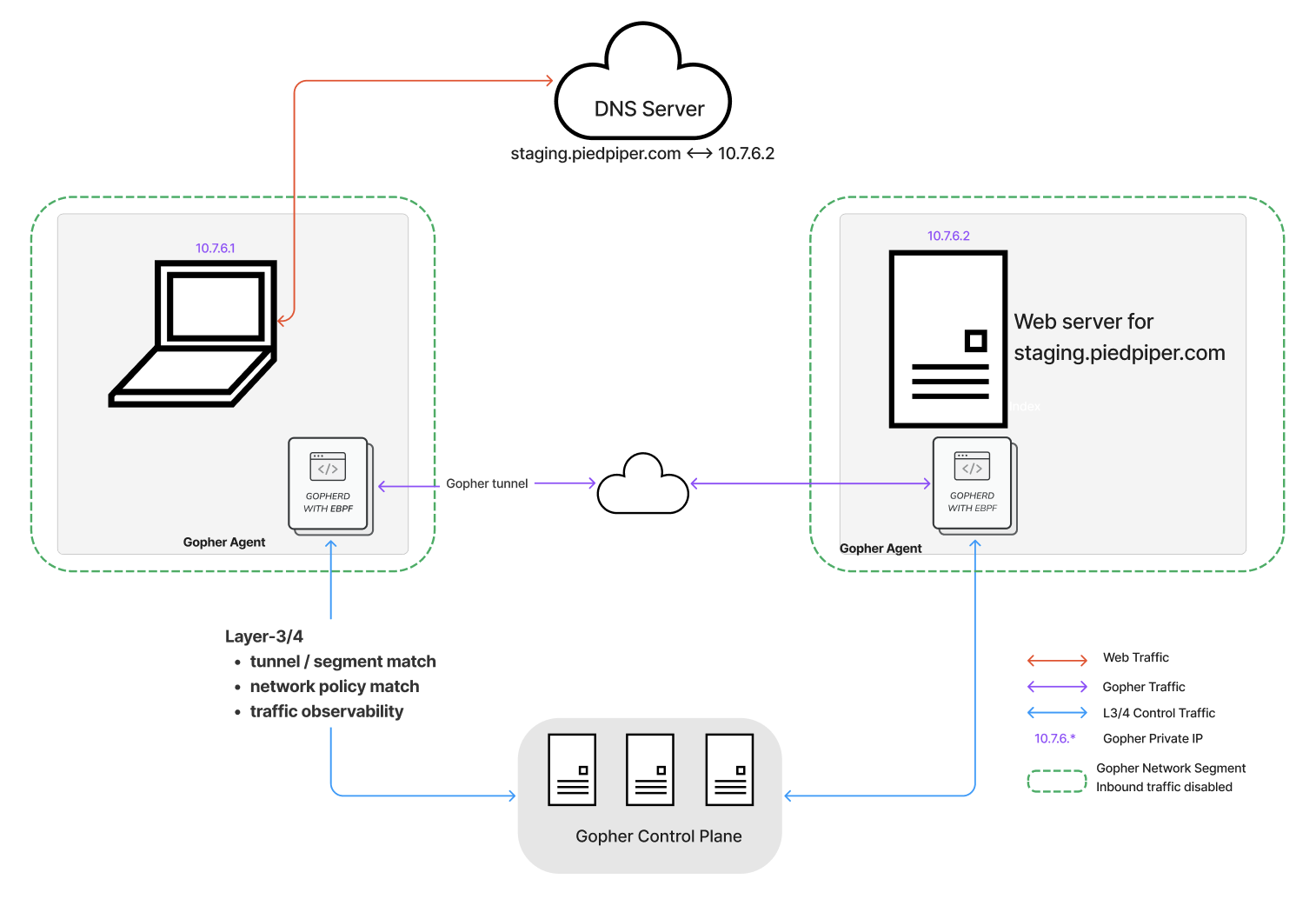
Gopher Unpublish: Lock Down Mission-Critical Web Applications Using Gopher Private IP, Peer-to-Peer Networking and Micro-segmentation
What Is Lockdown?
Lockdown in the context of web applications refers to the process of restricting access to sensitive applications, making them inaccessible to unauthorized users. This strategy is critical in preventing data breaches, unauthorized access, and other cyber threats. Traditional methods often involve using VPNs to create a secure environment, but these solutions have limitations, particularly in today's cloud-based and hybrid IT environments.
Why Lock down Your Public Web Applications?
Public web applications are prime targets for cyberattacks. Vulnerabilities such as unpatched software, weak authentication mechanisms, and inadequate encryption can lead to data breaches, ransomware attacks, and unauthorized access. As enterprises increasingly adopt cloud and hybrid environments, and with the rise of AI, the attack surface has expanded, making it more crucial than ever to implement robust lockdown strategies.
Traditional Method: VPNs
VPNs have traditionally been the go-to solution for securing remote access to web applications. They create an encrypted tunnel between the user and the application, protecting data in transit. However, VPNs are often associated with broad access controls, meaning that once a user is authenticated, they may have access to more resources than necessary. Additionally, VPNs can introduce latency and are not designed to handle the dynamic nature of modern cloud environments.
Innovative Method: Gopher Unpublish
Gopher Unpublish offers a modern solution by privatizing public web applications. Unlike VPNs, Gopher Unpublish makes applications entirely inaccessible unless accessed through Gopher's dedicated encrypted tunnels. This ensures that only authorized users can interact with the application, drastically reducing the attack surface and enhancing security.
Customer Value: Gopher Unpublish offers a more secure, efficient, and flexible solution compared to traditional VPNs, better suited for today's complex IT environments.
Gopher Unpublish vs. Traditional Methods
P2P vs. VPN Proxy
VPN Proxy: Traditional VPNs route traffic through a central proxy server, which can become a single point of failure and a bottleneck, reducing performance and increasing latency.
P2P (Peer-to-Peer): Gopher Unpublish utilizes P2P connections, allowing direct communication between nodes without relying on a central server. This reduces latency, increases performance, and eliminates the single point of failure.
Customer Value: P2P connections ensure faster, more reliable access to mission-critical applications, enhancing user experience and operational efficiency.
ZTNA vs. VPN Broad Access
VPN Broad Access: Once authenticated, VPN users typically gain broad access to the network, which can lead to security risks if unauthorized users gain access.
ZTNA (Zero Trust Network Access): Gopher Unpublish leverages ZTNA, where access is granted on a need-to-know basis. Users can only access specific applications for which they have explicit permission, minimizing the risk of unauthorized access.
Customer Value: ZTNA provides more granular access control, ensuring that only authorized users can access sensitive applications, significantly enhancing security.
Quick Setup for Remote Web Server Access
Traditional Setup: Configuring a VPN to connect remote web servers and reassigning public domains can be time-consuming and complex, often requiring manual configuration and management.
Gopher Unpublish Setup: With Gopher Unpublish, setting up a network and configuring a web application's domain to its Gopher private IP can be done in a few clicks via the Gopher control plane.
Customer Value: This streamlined setup process saves time and reduces the potential for configuration errors, allowing businesses to secure their applications quickly and efficiently.
Enforce Access Control Easily
Traditional Method: Enforcing access control with VPNs can be challenging, especially in large, dynamic environments where users and resources frequently change.
Gopher Unpublish: With Gopher Unpublish, access control is straightforward—only users invited to the same network as the web server can access the application, ensuring that access is tightly controlled.
Customer Value: Simplified access control reduces administrative overhead and ensures that only authorized users can access critical applications, enhancing overall security.
Gopher Unpublish With Layer 3/4 Security
1. Network Tunnel and Segment Matching: Users can only access web servers if their network tunnel and segment match, ensuring secure and isolated communication channels.
2. Network Policy Matching: Access is further restricted by ensuring that network policies match between the user and the web server, providing an additional layer of security.
3. Traffic Observability: Gopher Unpublish offers full observability of traffic between remote users and web servers, allowing for detailed monitoring and threat detection.
4. End-to-End Encryption: All communication is encrypted from end to end, protecting data in transit from interception and unauthorized access.
5. Quantum-Resistant Communication: Gopher Unpublish employs quantum-resistant encryption, ensuring that communications remain secure even against future quantum computing threats.
6. Inbound Traffic Control: Gopher Unpublish disables inbound traffic unless it’s through authorized, dedicated Gopher tunnels with NAT traversal capability, significantly reducing the attack surface.
Customer Value: These advanced security features provide comprehensive protection for mission-critical web applications, ensuring that they remain secure against current and future threats.
Conclusion
Gopher Unpublish offers a revolutionary approach to securing mission-critical web applications by privatizing them and ensuring they are only accessible through secure, encrypted tunnels. By leveraging advanced P2P networking, ZTNA, and quantum-resistant encryption, Gopher Unpublish provides unparalleled security, control, and ease of use compared to traditional methods like VPNs.
Final Thoughts and Recommendation
In an era where cybersecurity threats are constantly evolving, Gopher Unpublish stands out as a vital tool for protecting your most sensitive web applications. Its innovative features not only enhance security but also simplify the management of secure connections, making it an essential investment for any business looking to safeguard its digital assets. We strongly recommend adopting Gopher Unpublish to ensure that your mission-critical applications remain secure, private, and resilient against emerging threats.