2025 Verizon Data Breach Report Highlights Cyber Threats in Europe
2025 Data Breach Investigations Report Highlights
The 2025 Data Breach Investigations Report (DBIR) from Verizon provides critical insights into the shifting threat landscape of cybersecurity. A notable statistic shows that breaches linked to third-party involvement have doubled compared to last year, highlighting vulnerabilities exploited by cybercriminals. To secure your organization, it’s essential to understand these evolving threats.
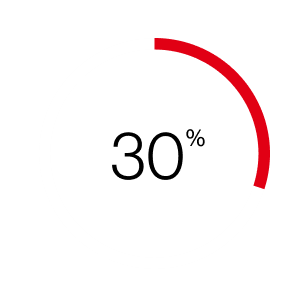
Image courtesy of Verizon
The report indicates a significant rise in attackers exploiting vulnerabilities for unauthorized access, a crucial area for businesses to monitor. Additionally, organizations have only fully remediated a fraction of perimeter-device vulnerabilities, underscoring the need for consistent security measures.
Explore more on the 2025 DBIR findings through the complete report and the executive summary.
Key Statistics and Trends
The DBIR outlines several alarming trends:
- Ransomware is present in a growing number of breaches, with almost 50% of analyzed incidents showing its involvement.
- Cybercriminals increasingly employ system intrusions and social engineering tactics, emphasizing the importance of employee training.
- Small and Medium Businesses (SMBs) are disproportionately targeted, facing attacks nearly four times more than larger organizations.

Image courtesy of Verizon
For a visual representation of key data points, view the 2025 DBIR infographic.
Cybersecurity Insights from KnowBe4
The 2025 KnowBe4 Report emphasizes the vulnerability of Europe’s manufacturing sector, which is increasingly targeted due to its expanded digital footprint. Ransomware remains a primary concern, with manufacturing being the most targeted industry for the fourth consecutive year. The report highlights a staggering 89.2% increase in confirmed data breaches from 2023 to 2024.

Image courtesy of KnowBe4
Key findings include:
- Ransomware accounted for 47% of all manufacturing breaches, indicating a persistent threat.
- Social engineering attacks are responsible for 22% of breaches, demonstrating the critical need for enhanced security awareness training.
For further details, download the full report, "Securing Manufacturing's Digital Future," here.
Recommendations for Enhanced Security
To mitigate risks, organizations should implement several strategies:
- Regularly update software to close security gaps.
- Educate employees on recognizing phishing attempts and other threats.
- Employ multifactor authentication (MFA) to safeguard sensitive access points.
Verizon's DBIR provides a roadmap for addressing these vulnerabilities, aligning with frameworks such as the Center for Internet Security Critical Security Controls.
Organizations can further explore cybersecurity strategies by watching the recent webinar series featuring industry experts discussing emerging threats and innovative defense strategies.
For more robust security solutions, consider leveraging the expertise of Gopher Security, where we specialize in comprehensive risk management and cybersecurity solutions tailored to your organization's needs.




