AI-Driven Negotiation Feature for Emerging Ransomware-as-a-Service
GLOBAL GROUP Ransomware-as-a-Service Overview
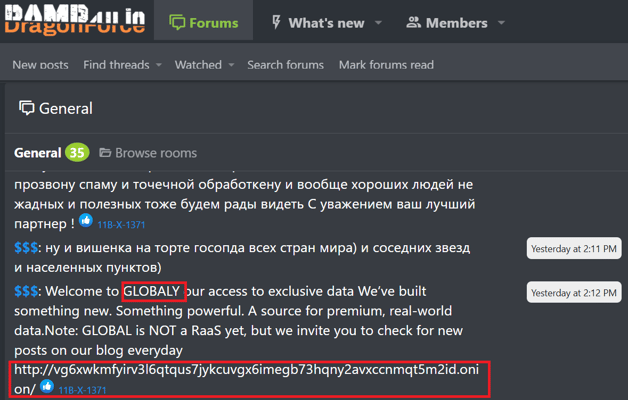
A new Ransomware-as-a-Service (RaaS) operation named GLOBAL GROUP has emerged, leveraging advanced AI-driven negotiation tools to increase pressure on victims. Security researchers from EclecticIQ first identified the group in early June 2025 on the Ramp4u underground forum. The actor known as “$$$” announced a dedicated leak site and a fully operational RaaS platform.

Infrastructure and Operations
GLOBAL GROUP relies heavily on Initial Access Brokers (IABs) to gain footholds in high-value corporate networks. These brokers provide access via compromised VPN appliances, including Fortinet, Palo Alto, and Cisco, as well as webshells for SAP NetWeaver environments. The deployment of customized ransomware payloads is executed rapidly to maximize damage before defenses can respond.
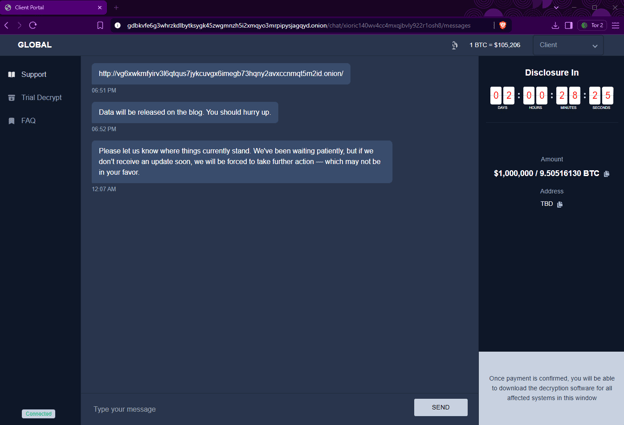
The group's negotiation system employs AI chatbots that guide victims through a scripted extortion dialogue. This system includes multiple language options, allowing non-English-speaking affiliates to communicate effectively with their targets. The AI increases psychological pressure by threatening data leaks if victims hesitate.
Affiliate Model and Revenue Share
Affiliates of GLOBAL GROUP can expect a revenue share of 80 to 85 percent from ransom payments. This model is designed to attract experienced cybercriminals from competing RaaS operations. The affiliate dashboard enables users to create cross-platform payloads and automate domain-wide deployments using SMB and malicious Windows services.
The new platform offers an advanced Command and Control (C2) capability, allowing affiliates to customize their ransomware deployment extensively. The incorporation of AI negotiation tools signifies a significant advancement in the RaaS market, facilitating a competitive "service economy" for cybercrime.

Recent Activity and Targeted Sectors
Since its emergence, GLOBAL GROUP has claimed responsibility for multiple ransomware incidents across various sectors, predominantly targeting healthcare providers in the U.S. and Australia, as well as industrial firms in the U.K. and Brazil. Analysts have tracked victims’ data being exposed on its dedicated leak site, which is hosted on the Tor network.
According to EclecticIQ, some ransom demands have reached over one million U.S. dollars, with victims often given a tight deadline to respond. This highlights the group's strategy of targeting high-value ransoms and executing rapid extortion tactics.
AI-Driven Negotiation Features
The AI-driven negotiation interface allows for dynamic adjustments and increases pressure on victims. The chatbots can adapt their strategy based on the victim's responses, creating a more personalized experience that enhances the likelihood of payment. This represents a shift toward more sophisticated extortion methods in the cybercriminal landscape.
In addition to its negotiation capabilities, the GLOBAL GROUP platform provides a mobile control panel, enabling affiliates to manage their operations remotely.

Security Implications and Recommendations
The emergence of GLOBAL GROUP indicates a growing trend in RaaS operations utilizing AI and advanced negotiation tactics to optimize their extortion efforts. Organizations are advised to enhance their cybersecurity measures, including adopting a Zero-Trust architecture, implementing robust patch management, and ensuring frequent backups of sensitive data.
For ongoing updates on the evolving tactics of ransomware groups like GLOBAL GROUP, it is crucial for security teams to stay informed and adjust their defensive strategies accordingly.