Apple iOS 26 Update: Critical Font Bug Fix and Security Enhancements
Apple Security Update for CVE-2025-43400
Apple has released critical security updates across various platforms to address the vulnerability identified as CVE-2025-43400. This flaw affects the FontParser component, which is responsible for processing fonts in macOS, iOS, iPadOS, and visionOS. The vulnerability allows attackers to craft malicious font files that may lead to app crashes or memory corruption, posing a risk of arbitrary code execution.

Image courtesy of Malwarebytes
How to Update Your Devices
iPhone and iPad
To check for the latest software version on iOS and iPadOS devices, navigate to Settings > General > Software Update. Enabling Automatic Updates is also recommended.
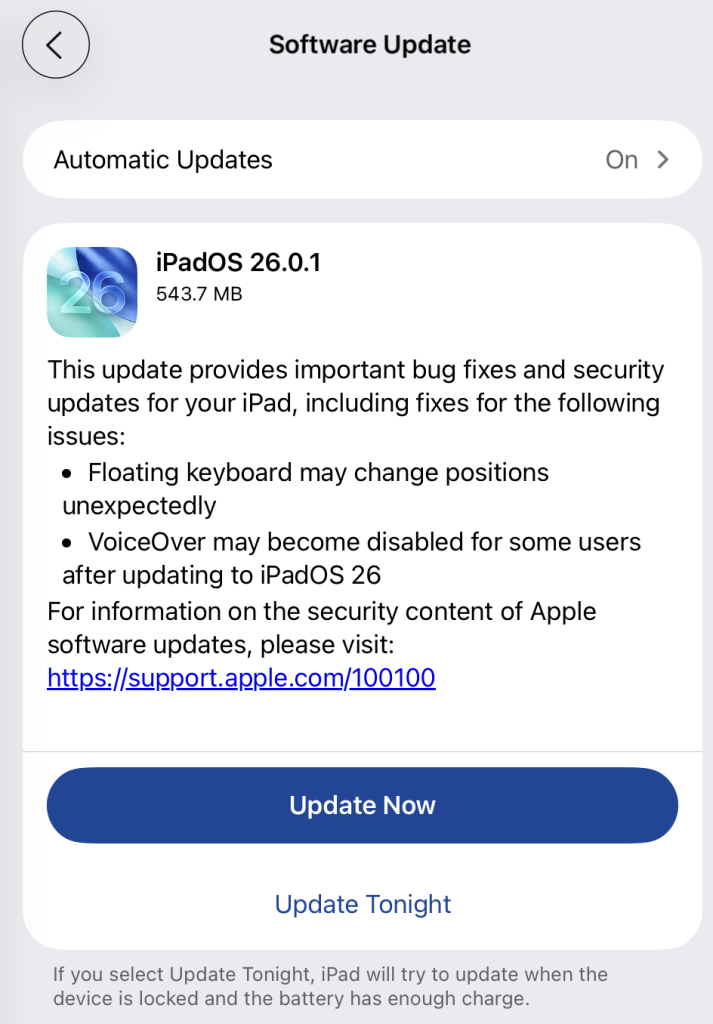
Image courtesy of Malwarebytes
macOS
For macOS users, updating is done via the Software Update feature:
- Click the Apple menu in the upper-left corner.
- Select System Settings (or System Preferences on older versions).
- Click Software Update.
- Follow the on-screen instructions to complete the update.
Before upgrading to macOS Tahoe 26, refer to the instructions.
Apple Watch
- Ensure your iPhone is paired and connected to Wi-Fi.
- Keep the Apple Watch on its charger.
- Open the Watch app on your iPhone and go to General > Software Update.
- Tap Download and Install if an update is available.
Apple TV
- Open the Settings app on Apple TV.
- Go to System > Software Updates and select Update Software.
Technical Details of CVE-2025-43400
CVE-2025-43400 is an out-of-bounds write issue, which can lead to unexpected app termination or memory corruption. This vulnerability allows an attacker to manipulate memory areas that should be inaccessible, potentially enabling remote code execution.
The exploit occurs when a device processes a specially crafted font that corrupts memory. Typically, fonts are safe standard files; however, this vulnerability creates a significant attack vector. Attackers can load malicious fonts via documents or emails, leading to serious security risks.
Expert Insights
According to Sylvain Cortes, vice-president of strategy at Hackuity, "FontParser is the system that interprets font files, so characters can be interpreted across applications, documents, and the web." This highlights the potential reach of the vulnerability. Johannes Ullrich from the SANS Technology Institute noted that while the exploit's ability to allow remote code execution is uncertain, it could lead to ransomware attacks.
Image courtesy of Hoplon InfoSec
In summary, Apple has provided updates addressing CVE-2025-43400 across its devices, including iOS 26.0.1, iPadOS 26.0.1, macOS Tahoe 26.0.1, and visionOS 26.0.1. Users are encouraged to update their devices promptly to mitigate risks associated with this serious vulnerability.






