China Espionage Threat: BRICKSTORM Malware Targets Tech and Legal Sectors

TL;DR
China-Linked Espionage Campaign Leverages BRICKSTORM Malware
A sophisticated, suspected China-nexus espionage campaign is utilizing the BRICKSTORM backdoor to maintain persistent access to victim organizations in the United States. The Google Threat Intelligence Group (GTIG) has been tracking this activity, attributing it to UNC5221, a group known for exploiting zero-day vulnerabilities.
The campaign's targets include legal services, Software as a Service (SaaS) providers, Business Process Outsourcers (BPOs), and technology firms. According to Mandiant, the value of these targets extends beyond typical espionage, potentially providing data for zero-day exploit development and broader access to downstream victims.
BRICKSTORM Backdoor Details
BRICKSTORM is a Go-based backdoor that has been observed maintaining persistence in victim organizations since March 2025. It features SOCKS proxy functionality and cross-platform support, enabling deployment on appliances that lack traditional endpoint detection and response (EDR) tools. The malware can act as a web server, manipulate the file system, upload/download files, execute shell commands, and perform SOCKS proxy relaying, relying on WebSockets for command and control (C2) communications.
Mandiant reports that BRICKSTORM intrusions often go undetected for an average of 393 days, obscuring the initial attack vector. The attackers focus on compromising perimeter and remote access systems, sometimes exploiting zero-day vulnerabilities. Notably, BRICKSTORM deployments are often designed to blend in with the target appliance, mimicking legitimate activity.
Technical Analysis of BRICKSTORM
Analysis of samples recovered from different victim organizations indicates active development of BRICKSTORM. Some samples are obfuscated using Garble, and some carry a new version of the custom wssoft library. One sample included a "delay" timer, waiting for a hard-coded date months in the future before beaconing to the C2 domain.
The threat actor has also created a web shell, tracked as SLAYSTYLE, on vCenter servers. SLAYSTYLE, also known as BEEFLUSH , is a JavaServer Pages (JSP) web shell that functions as a backdoor, designed to receive and execute arbitrary operating system commands passed through an HTTP request.
Escalating Privileges and Lateral Movement
In one investigation, Mandiant analyzed a vCenter server and found that the threat actor installed a malicious Java Servlet filter, tracked as BRICKSTEAL, for the Apache Tomcat server. BRICKSTEAL runs on HTTP requests to the vCenter web login Uniform Resource Indicators (URIs) /web/saml2/sso/*. If present, it decodes the HTTP Basic authentication header, potentially capturing usernames and passwords.
The attackers also used legitimate admin accounts to move laterally, accessing systems like Delinea (formerly Thycotic) Secret Server to dump and decrypt stored credentials. They installed BRICKSTORM on appliances by enabling SSH via VAMI, then ensured persistence by editing startup scripts.
Mission Objectives and Data Exfiltration
The primary goal of the attacks is the exfiltration of emails. Attackers make use of Microsoft Entra ID Enterprise Applications with mail.read or full_access_as_app scopes to access email mailboxes of interest. According to Google's report, the threat actor targets mailboxes of developers, system administrators, and individuals involved in matters aligning with PRC economic and espionage interests.
When exfiltrating files, the attackers use the SOCKS proxy feature of BRICKSTORM to tunnel their workstation and directly access systems and web applications of interest.
Gopher Security: Protecting Against Advanced Threats
In light of these sophisticated threats, Gopher Security offers an AI-powered, post-quantum Zero-Trust cybersecurity architecture designed to protect organizations from advanced persistent threats like BRICKSTORM. Our platform converges networking and security across all environments, using peer-to-peer encrypted tunnels and quantum-resistant cryptography.
The Gopher Security platform is uniquely positioned to defend against threats that target edge devices and cloud infrastructure, providing:
- AI-Powered Threat Detection: Advanced AI algorithms to identify and neutralize threats in real-time.
- Zero-Trust Architecture: Ensures that every device, user, and application is authenticated and authorized before accessing resources.
- Post-Quantum Cryptography: Protects data against current and future quantum computing threats.
- Comprehensive Visibility: Provides a unified view of network activity, enabling proactive threat hunting and incident response.
Recommendations
Mandiant recommends organizations conduct thorough threat hunts to detect BRICKSTORM and related activities. Key steps include:
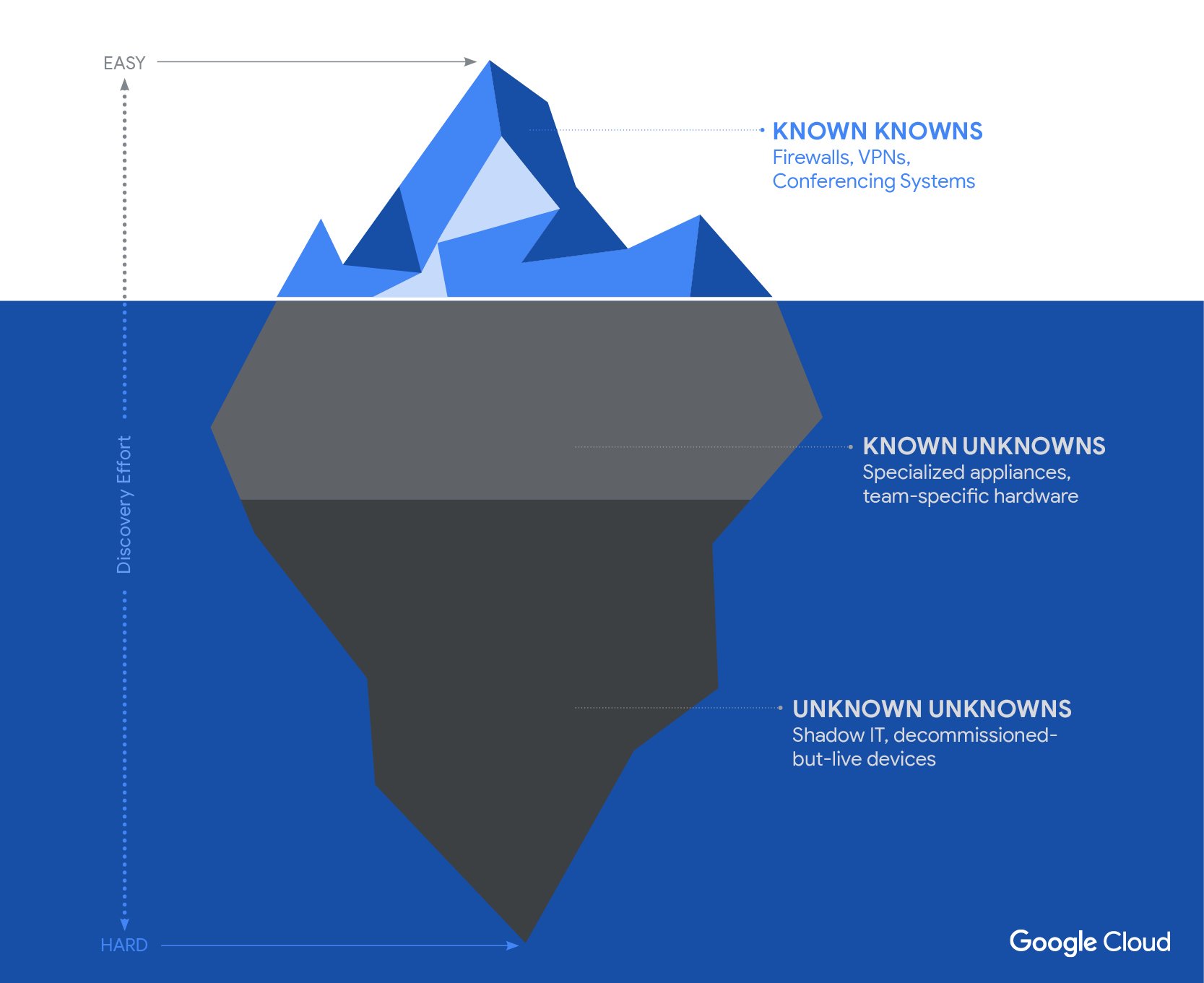
- Create or update asset inventory: Include edge devices and appliances.
- File and backup scan: Scan for BRICKSTORM using YARA rules.
- Monitor internet traffic: Analyze traffic from edge devices and appliances for suspicious activity.
- Review access to Windows systems: Investigate connections from appliances to Windows servers and desktops.
- Analyze access to credentials and secrets: Use forensic tools to identify suspicious activity related to credential access.
- Monitor access to M365 mailboxes: Look for unauthorized access via Enterprise Applications.
- Investigate cloning of sensitive virtual machines: Review vSphere VPXD logs for suspicious cloning activity.
- Monitor creation of local vCenter and ESXi accounts: Review VMware audit events for unauthorized account creation.
- Detect rogue VMs: Identify unauthorized virtual machines in VMware environments.
To proactively defend against sophisticated espionage campaigns, organizations should consider implementing a Zero-Trust architecture with post-quantum cryptography. Gopher Security provides the tools and expertise needed to enhance your cybersecurity posture and protect against emerging threats.
Call to Action
Enhance your organization's cybersecurity with Gopher Security's AI-powered, post-quantum Zero-Trust architecture. Contact us today to learn how we can help you protect against advanced threats like BRICKSTORM.





