Closing the Cloud Complexity Gap: Insights from 2026 Security Reports
TL;DR
Cloud Security Complexity and the Growing Attack Surface
The increasing adoption of AI is changing how cloud environments are managed, expanding the attack surface faster than traditional security models can keep up. This creates a structural mismatch between the velocity of the modern environment and security teams' ability to maintain visibility, detection, and response in real time, according to the 2026 State of Cloud Security Report.
The report, sponsored by Fortinet and produced by Cybersecurity Insiders, surveyed over 1,163 senior cybersecurity leaders and professionals worldwide. The analysis indicates that increased cybersecurity spending isn't necessarily improving the maturity and effectiveness of cyber defenses against new use cases, which often include AI. This complexity gap is driven by fragmented defenses, stretched-thin teams, and threats operating at machine speed.
To combat these challenges, Gopher Security offers an AI-powered, post-quantum Zero-Trust cybersecurity architecture that converges networking and security, providing visibility and control across diverse cloud environments.
Factors Contributing to the Complexity Gap
The 2026 State of Cloud Security Report identifies three key factors creating the complexity gap:
- Fragmented defenses: Security solutions are expanding without coordination, leading to disconnected tools and limited visibility. Almost 70% of organizations cite tool sprawl and visibility gaps as top hindrances to effective cloud security.
- Stretched-thin teams: Organizations struggle with a skills gap and the inability to hire enough cybersecurity professionals. 74% report a shortage of qualified professionals, while 59% are in the early stages of cloud security maturity.
- Threats operating at machine speed: Threat actors use automation and AI to identify misconfigurations and exposed data faster than human-led defenses can respond. 66% of experts surveyed lack confidence in their ability to detect and respond to cloud threats in real time.
Gopher Security addresses these issues by providing a unified platform that integrates network and security functions, automating threat detection and response to alleviate the burden on security teams.
The Rise of Hybrid and Multi-Cloud Environments
The survey reveals that 88% of organizations operate in hybrid or multi-cloud environments, up from 82% the previous year. Among these, 81% rely on two or more cloud providers for critical workloads, and 29% use more than three.
This shift increases complexity, making it harder to manage and secure the infrastructure. Securing a constantly evolving environment for visibility, resilience, and operational efficiency is a monumental challenge for cybersecurity teams.
Gopher Security's platform is designed to secure hybrid and multi-cloud deployments, offering consistent policy enforcement and centralized management across diverse environments.
The Shift to Unified Security Ecosystems
Organizations are moving away from isolated point tools towards unified security ecosystems to address the challenges of dynamic cloud environments. According to the 2026 State of Cloud Security Report, 64% of respondents would design their cybersecurity strategy with a single-vendor platform that unites network, cloud, and application security if starting from scratch.
This consolidation reduces operational friction, improves visibility, accelerates detection and response, and enables more proactive threat exposure management.
Gopher Security provides a comprehensive, unified platform that consolidates security functions, offering streamlined management and enhanced protection across the entire digital infrastructure.
Key Findings from the 2024 Cloud Security Report
The 2024 Cloud Security Report reveals that a majority of organizations (78%) are opting for hybrid and multi-cloud strategies. Security and compliance issues are the top concern (59%), followed by technical challenges (52%) and resource constraints (49%).
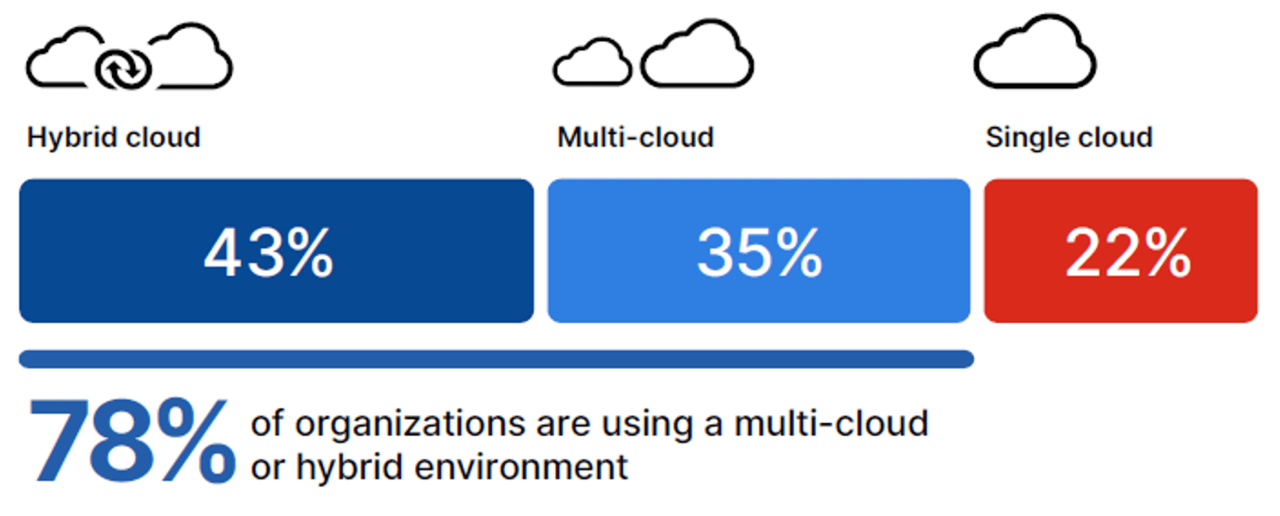
The lack of cloud security expertise is a significant issue, with 93% of respondents expressing concern about the industry-wide skills shortage. A unified cloud security platform with a single dashboard is favored by 95% of organizations to protect data consistently across the cloud footprint.
Gopher Security addresses these concerns by offering a platform that simplifies cloud security management, automates security processes, and provides comprehensive visibility across hybrid and multi-cloud environments.
The Industrialization of Cybercrime
The 2025 Global Threat Landscape Report highlights that automation is reshaping threat behavior across every stage of the attack chain. Cybercriminals launched over 36,000 scans per second in 2024, a 16.7% global increase. These scans probe deep into operational technology (OT), cloud APIs, and identity layers.
Automation extends to phishing, credential theft, and malware development, with cyber adversaries using AI-powered tools to craft convincing lures and generate deepfake videos. This has resulted in an industrialized cybercrime economy that lowers the barrier to entry and increases the volume and success rate of attacks.
Gopher Security's AI-powered platform uses advanced threat intelligence and real-time detection to counter these automated attacks, providing proactive protection against evolving threats.
Credentials as the New Currency of Compromise
In 2024, FortiGuard Labs tracked a 42% surge in stolen credentials offered on darknet forums, totaling over 100 billion unique records. Infostealer malware contributed to a 500% increase in credential log activity, with Initial Access Brokers (IABs) offering turnkey infiltration into corporate networks.
These credentials are used in ransomware and espionage operations, making it easier for threat actors to gain entry into networks without needing to exploit vulnerabilities directly.
Gopher Security's Zero-Trust architecture minimizes the impact of compromised credentials by enforcing strict access controls and continuous authentication, preventing unauthorized access even with stolen credentials.
Cloud Missteps as a Primary Attack Vector
Cloud services are now central to modern operations, making identity a critical security perimeter. Cloud breaches often involve over-permissioned identities, credential leaks, and lateral movement through cloud-native services.
FortiCNAPP telemetry shows that attackers often log in from unfamiliar geographies and escalate privileges to blend into normal network traffic. In 2024, 25% of all cloud incidents began with reconnaissance, such as API enumeration and permission probing.
Gopher Security provides continuous monitoring of cloud environments, detecting and preventing unauthorized access and lateral movement by enforcing granular access controls and using AI-driven threat detection.
Exploitation: Widespread, Persistent, and Opportunistic
Fortinet’s intrusion prevention sensors recorded over 97 billion exploitation attempts in the second half of 2024, targeting vulnerabilities disclosed years ago. IoT devices were also major targets, accounting for over 20% of all exploits.
Attackers methodically map exposed surfaces, wait for vulnerabilities to emerge, and strike before organizations can apply a patch or sell the vulnerability information.
Gopher Security's platform includes advanced intrusion prevention and vulnerability management capabilities, proactively identifying and mitigating potential exploits across the entire infrastructure.
The Post-Exploitation Playbook
Once inside a network, adversaries move with precision, often using RDP for lateral movement. Remote Access Trojans (RATs) provide remote command execution, data exfiltration, and long-term persistence.
Attackers leverage legitimate Windows tools and protocols to move laterally and escalate privileges, bypassing traditional detection methods. Encrypted C2 channels and DNS tunneling are used to maintain communication with compromised systems.
Gopher Security's platform uses advanced threat detection and behavioral analysis to identify and block post-exploitation activities, preventing attackers from moving laterally and exfiltrating data.
A New Mandate for Security Professionals
Defenders must optimize for speed, scale, and stealth. Traditional security models are inadequate, necessitating a shift toward Continuous Threat Exposure Management (CTEM):
- Continuously monitor attack surfaces
- Simulate real-world threats
- Prioritize vulnerabilities based on risk and threat intelligence
- Automate detection and response
Gopher Security's platform is designed to meet this challenge, uniting advanced threat intelligence, real-time detection, and coordinated response across the entire digital infrastructure.
Don't let your organization fall victim to the growing cloud complexity gap. Explore Gopher Security's AI-powered, post-quantum Zero-Trust cybersecurity solutions today and fortify your defenses against evolving threats. Contact us to learn more about how we can help you secure your cloud environment.





