Critical RCE Vulnerabilities in React and Next.js Expose Millions

TL;DR
Critical RCE Vulnerabilities Impact React and Next.js
React and Next.js are facing critical unauthenticated Remote Code Execution (RCE) vulnerabilities, identified as CVE-2025-55182 and CVE-2025-66478. Immediate patching is crucial to mitigate these risks.
Technical Breakdown of the Vulnerabilities
The core issue lies within the React Server Components (RSC) "Flight" protocol. CVE-2025-55182 affects the react-server package, while CVE-2025-66478 impacts Next.js due to its implementation of the RSC "Flight" protocol. The vulnerability is rooted in insecure deserialization, where the server unsafely processes RSC payloads. A malformed payload can allow attacker-controlled data to manipulate server-side execution, leading to the execution of privileged JavaScript code. Exploitation has demonstrated a near 100% success rate via crafted HTTP requests.
The root cause is the server deserializing untrusted input directly into module and export name lookups, without proper verification.
return moduleExports[metadata.name]
The fix involves checking for own properties to prevent access to prototype-level properties:
if (hasOwnProperty.call(moduleExports, metadata.name)) {
return moduleExports[metadata.name];
}
return (undefined: any);
This issue highlights the risks of implicit RPC layers, as opposed to explicit frameworks like gRPC or SOAP that use schemas and service definitions to prevent boundary confusion.
Impacted Products and Versions
The following products and versions are affected:
react-server-dom: Versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0- Next.js: Versions 14.3.0-canary, 15.x, and 16.x (App Router)
Patched releases are available:
react-server-dom: 19.0.1, 19.1.2, and 19.2.1- Next.js: 14.3.0-canary.88, 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7
Other potentially affected frameworks and libraries include:
Recommended Actions for Security Teams
- Upgrade React and Next.js: Apply the hardened versions immediately.
- Check Other RSC Frameworks: If using other RSC-enabled frameworks, check for updates regarding the bundled
react-serverversion.
React Native CLI Vulnerability
A separate critical vulnerability (CVE-2025-11953) has been identified in the @react-native-community/cli package. This flaw allows remote unauthenticated attackers to execute arbitrary OS commands on the machine running the development server.
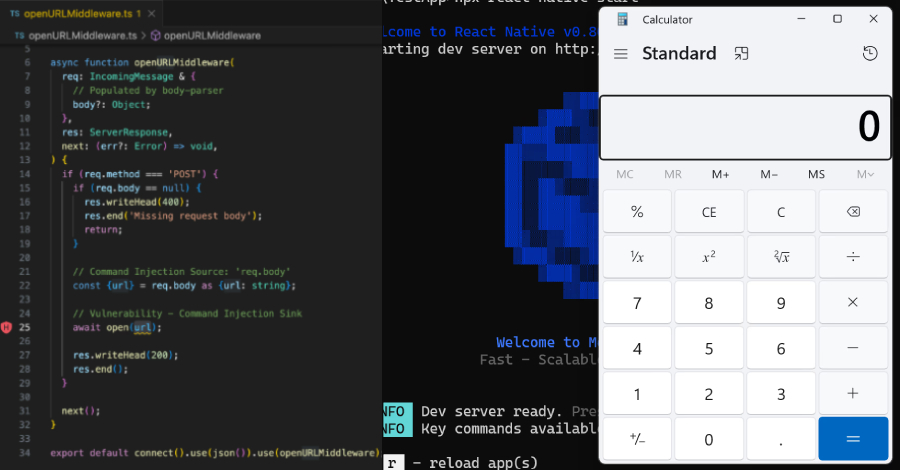
The vulnerability affects versions 4.8.0 through 20.0.0-alpha.2 of the @react-native-community/cli-server-api package. The issue stems from the Metro development server binding to external interfaces by default and exposing an "/open-url" endpoint susceptible to OS command injection.
The server's /open-url endpoint handles POST requests, passing user-input values to the unsafe open() function from the open NPM package, leading to OS command execution.
Mitigation Steps for React Native CLI Vulnerability
- Update the CLI: Upgrade to @react-native-community/cli-server-api version 20.0.0 or later.
- Bind to Localhost: As a temporary mitigation, bind the development server to localhost using the command
npx react-native start –host 127.0.0.1.
Gopher Security: Securing Your Applications with Zero-Trust Architecture
These vulnerabilities highlight the importance of robust security measures in modern application development. At Gopher Security, we specialize in AI-powered, post-quantum Zero-Trust cybersecurity architecture, converging networking and security across all environments. Our platform uses peer-to-peer encrypted tunnels and quantum-resistant cryptography to protect your applications from evolving threats.
To learn more about how Gopher Security can help secure your applications, visit https://gopher.security or contact our team for a consultation.





