Cyberattack Surge: 500% Increase in Palo Alto Scanning Activity
TL;DR
Coordinated Cyberattack Campaign
GreyNoise has detected a coordinated cyberattack campaign targeting Cisco, Fortinet, and Palo Alto Networks devices. The campaign involves escalating scanning activity that may indicate upcoming vulnerability disclosures.
Scanning Activity on Palo Alto Networks
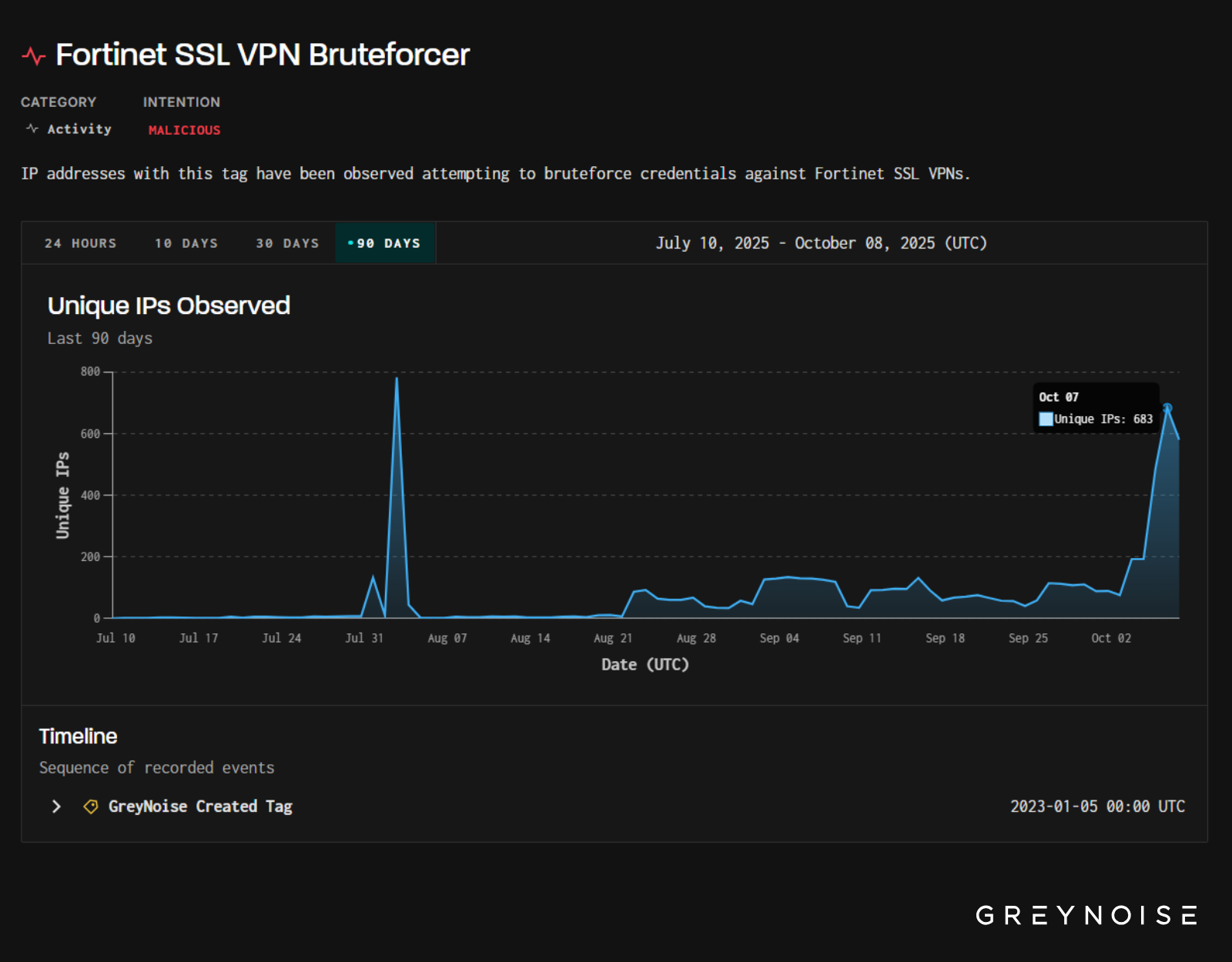
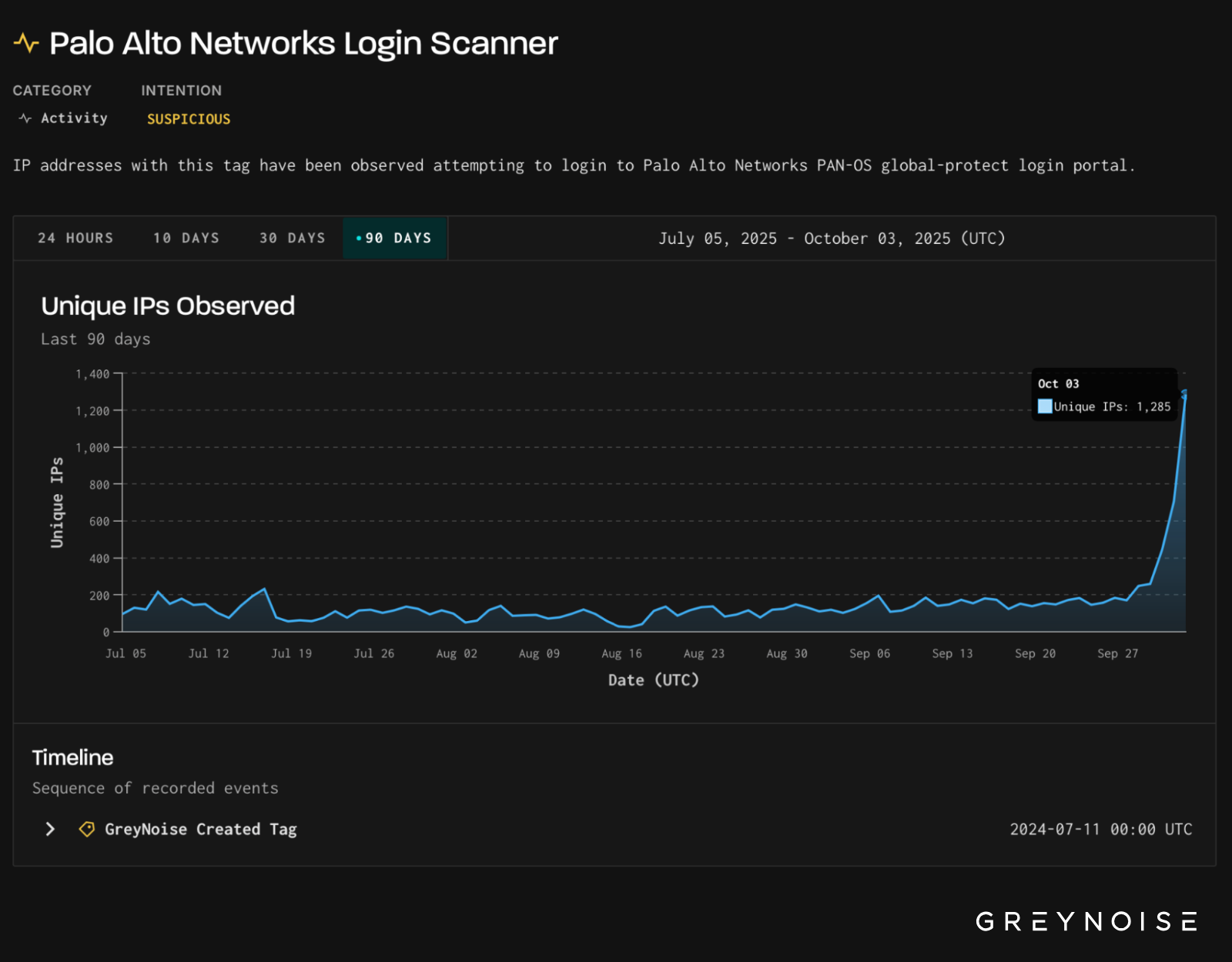
GreyNoise observed a spike in scanning activity targeting Palo Alto Networks login portals, with a nearly 500% increase in IP addresses scanning on October 3, 2025. This was the highest level recorded in the last three months. The traffic was described as targeted and structured. As many as 1,300 unique IP addresses participated, a jump from around 200 before. 93% were classified as suspicious and 7% as malicious.

Image courtesy of The Hacker News
Most IP addresses geolocated to the U.S., with smaller clusters in the U.K., the Netherlands, Canada, and Russia. According to GreyNoise, the "Palo Alto surge shares characteristics with Cisco ASA scanning occurring in the past 48 hours". Both cases exhibited regional clustering and fingerprinting overlap in the tooling used, with a dominant TLS fingerprint tied to infrastructure in the Netherlands.
Palo Alto Networks stated, "We have investigated the reported scanning activity and found no evidence of a compromise...Palo Alto Networks is protected by our own Cortex XSIAM platform".
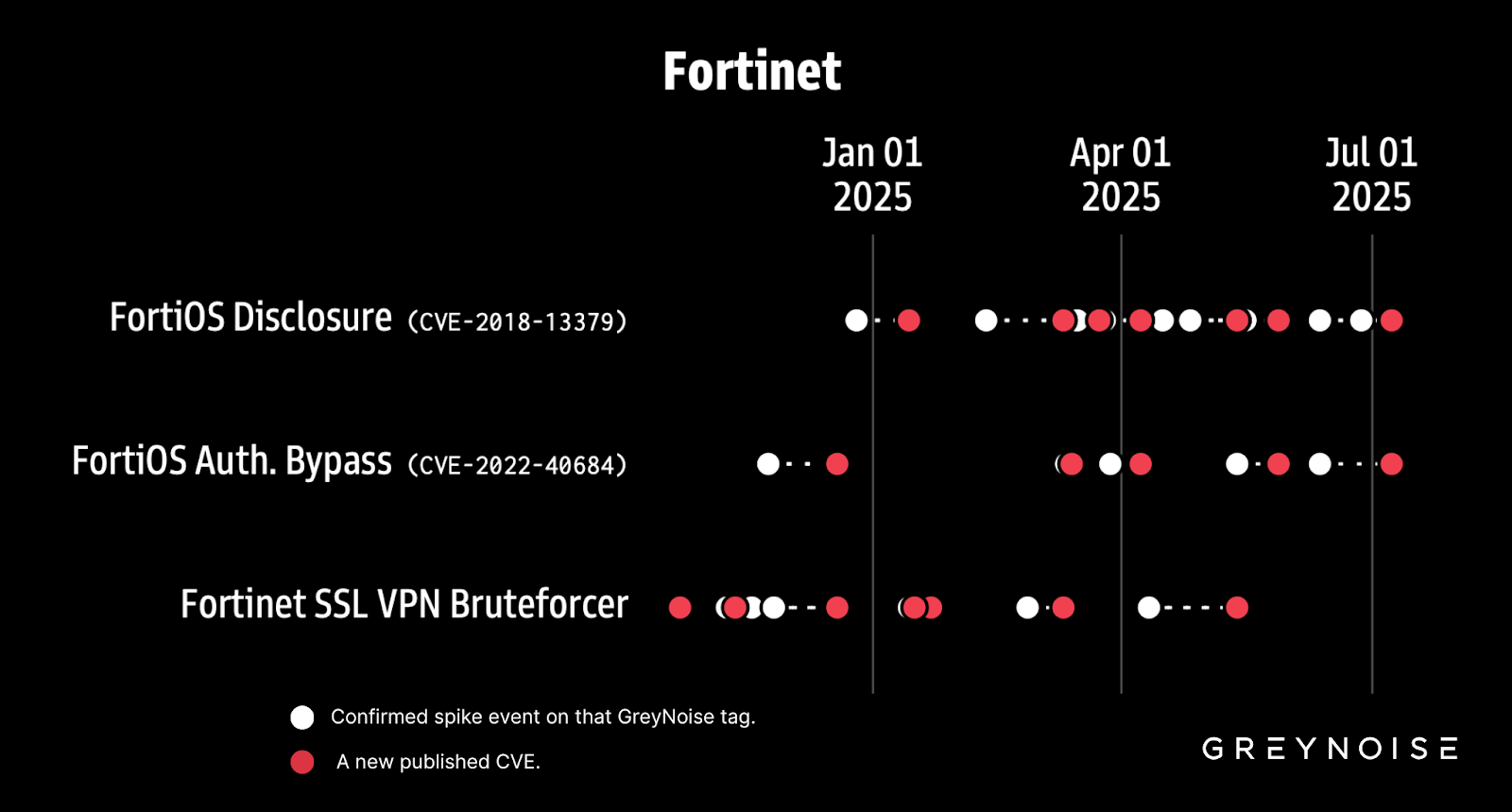
GreyNoise's Early Warning Signals report in July 2025 noted that surges in malicious scanning, brute-forcing, or exploit attempts are often followed by the disclosure of a new CVE affecting the same technology within six weeks.
In April 2025, GreyNoise reported similar suspicious login scanning activity targeting Palo Alto Networks PAN-OS GlobalProtect gateways.
Update on Palo Alto Networks Scans
On October 7, 2025, GreyNoise detected a further spike in scanning against Palo Alto Networks PAN-OS GlobalProtect login portals, originating from over 2,200 unique IP addresses. There was also a sharp increase in the number of ASNs involved, suggesting an increase in the number of threat actors involved. The pace of login attempts suggests activity driven by a threat actor iterating through a large dataset of credentials.
According to GreyNoise, elevated scanning activity targeting Cisco and Palo Alto Networks firewalls, along with brute-force attack attempts aimed at Fortinet SSL VPNs, originate from IPs on the same subnets, specifically from ASNs 3xK Tech GmbH (AS200373) and tzulo, Inc. (AS11878). They assess that the three campaigns are "at least partially" driven by the same threat actor due to shared TCP fingerprints, recurring subnets, and a coordinated surge in activity.
Correlated Campaigns
GreyNoise identified links between recent campaigns targeting:
- Cisco ASA scanning
- Elevated login attempts against Palo Alto login portals
- Spike in brute force attempts against Fortinet SSL VPNs
They assess with high confidence that all three campaigns are at least partially driven by the same threat actor(s), evidenced by shared TCP fingerprints, recurring subnets, and elevated activity at similar times.
All three campaigns heavily rely on the same subnets:
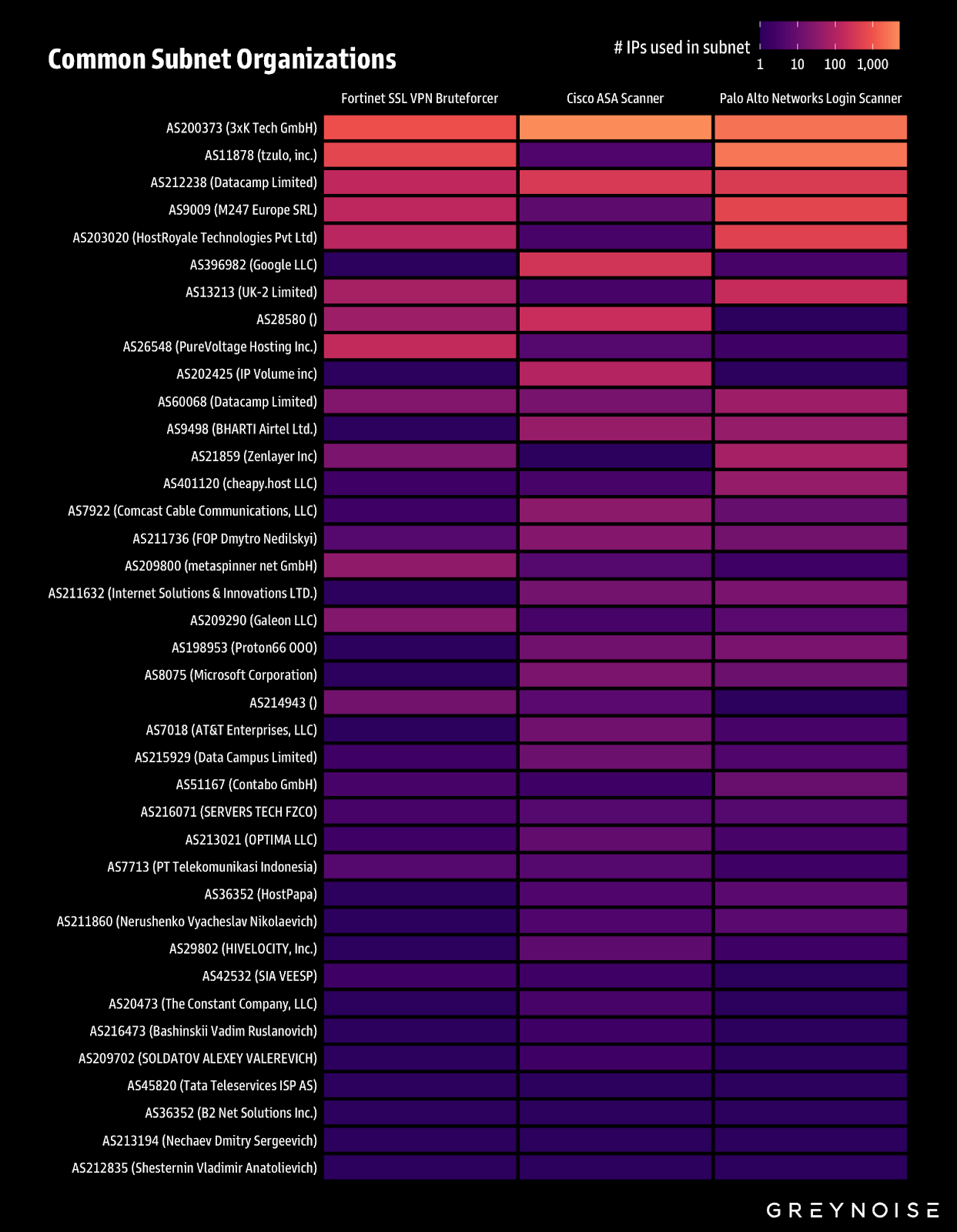
GreyNoise recommends using GreyNoise Block to block threat IPs from all relevant GreyNoise tags (ASA Scanner, Fortinet VPN Bruteforcer, Palo Scanner) and the ASNs AS200373 (3xK Tech GmbH) and AS11878 (tzulo, Inc.).
Fortinet Brute Force Attempts
GreyNoise research identified a correlation: spikes in Fortinet VPN brute force attempts are typically followed by Fortinet VPN vulnerabilities disclosures within six weeks.
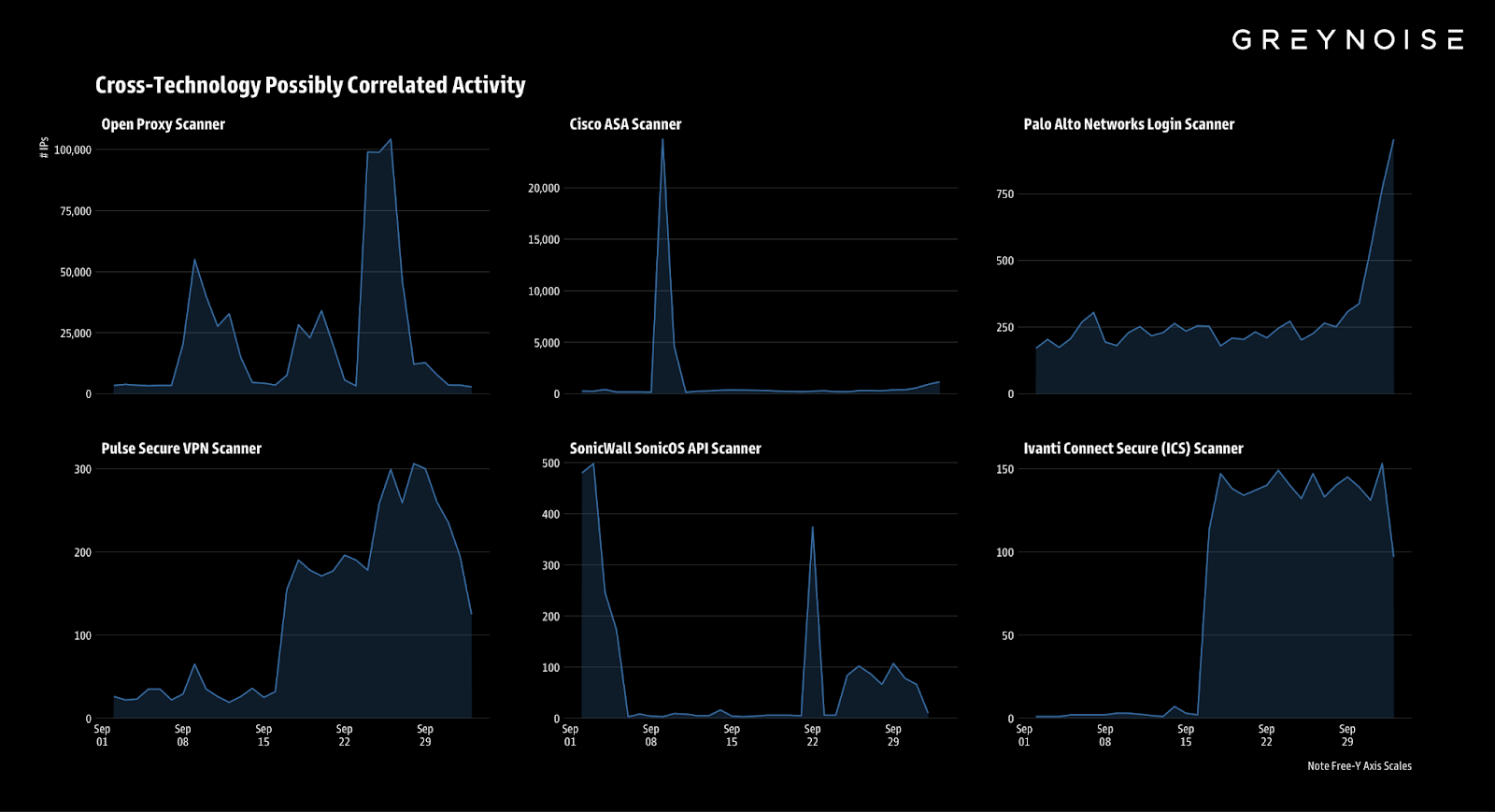
Scanning Surge Details
On October 3, 2025, GreyNoise observed a ~500% increase in IPs scanning Palo Alto Networks login portals, the highest level recorded in the past 90 days.
Key Findings:
- Volume: ~1,300 unique IPs triggered GreyNoise’s Palo Alto Networks Login Scanner tag on 3 October.
- Classification: 93% of IPs were classified as suspicious and 7% as malicious.
- Source infrastructure: 91% of IPs geolocated to the United States, with smaller clusters in the U.K., Netherlands, Canada, and Russia.
- Targeted profiles: Nearly all activity was directed at GreyNoise’s emulated Palo Alto profiles (Palo Alto GlobalProtect, Palo Alto PAN-OS).
- Destination focus: Distinct scanning clusters were observed in the past 48 hours.
Related Activity:
The Palo Alto surge shares characteristics with Cisco ASA scanning, with a dominant TCP fingerprint tied to infrastructure in the Netherlands.
Concurrent surges across remote access services were also identified.
Cisco ASA Zero-Day Exploitation
Cisco reported that a sophisticated state-sponsored threat actor is actively exploiting multiple zero-day vulnerabilities in [Cisco Adaptive Security Appliance (ASA)](https





