Cybercriminals Exploit Gen Z's Favorite Games in 19M Attacks
Gen Z’s Favorite Games Used as Bait in Cyberattacks
Kaspersky detected over 19 million attempts to download malicious files disguised as popular games from April 1, 2024, to March 31, 2025. Games like Grand Theft Auto, Minecraft, and Call of Duty were frequently exploited. The surge in attacks emphasizes the vulnerability of Gen Z gamers, who are often targeted due to their gaming habits.
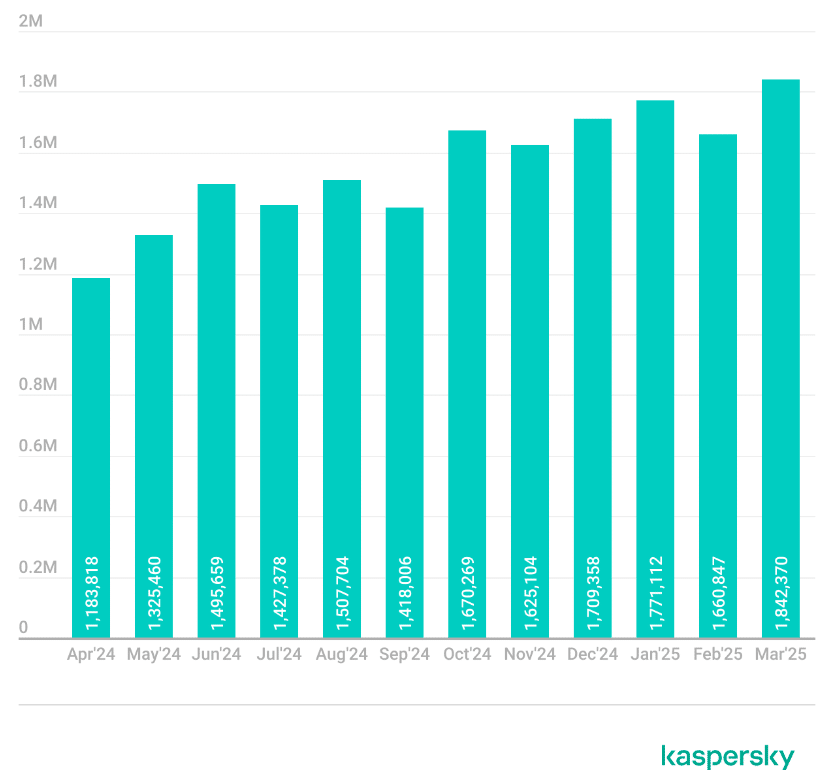
Image courtesy of Kaspersky
Kaspersky's report highlights that over 400,000 users were affected worldwide. The analysis included 20 popular game titles, with March 2025 recording the peak of 1,842,370 attack attempts.
Attack Statistics
The following table summarizes the attack attempts for the most exploited games:
| Title | Number of Attack Attempts |
|---|---|
| Grand Theft Auto | 4,456,499 |
| Minecraft | 4,112,493 |
| Call of Duty | 2,635,330 |
| The Sims | 2,416,443 |
| Roblox | 1,548,929 |
| FIFA | 909,174 |
| Among Us | 766,055 |
| Assassin’s Creed | 584,873 |
| CS: Go | 379,768 |
| Red Dead Redemption | 349,821 |
Despite its age, Grand Theft Auto remains a primary target due to its modding community. The upcoming release of GTA VI in 2026 may increase such attacks as cybercriminals capitalize on the game's popularity. Minecraft follows closely due to its extensive modding ecosystem, attracting users seeking custom content that can often carry malware.
Kaspersky also identified various types of malware linked to these exploits. Downloaders, adware, and Trojans were prevalent, with downloaders accounting for over 17.7 million attempts.
Cybercriminal Tactics
Cybercriminals employ a variety of tactics to exploit the gaming community. Fake giveaways, phishing links, and malicious mods have become common methods for stealing credentials and spreading malware. Kaspersky reported that scammers often impersonate popular games, creating fake websites that promise in-game rewards in exchange for login details.
Image courtesy of Kaspersky
Kaspersky has launched an interactive game called “Case 404” to help educate Gen Z about these threats. The game aims to teach players how to recognize scams and protect their digital identities while engaging in their favorite activities.
Trojans and Malware Campaigns
A sophisticated malware campaign has been identified where cybercriminals use trojanized versions of popular games. These compromised installers were distributed through torrent trackers and targeted users in various countries. Popular games like BeamNG.drive and Garry's Mod were weaponized to deliver XMRig cryptominers.
Image courtesy of Blogger
Attackers used Inno Setup to create trojanized installers that bypass security measures by employing anti-debugging techniques and encrypting malicious payloads. These strategies ensure the malware remains hidden until it can execute, often leading to theft of sensitive data and unauthorized access to gaming accounts.
Recommendations for Gamers
To combat these threats, Kaspersky recommends several safety measures:
- Download games, mods, and tools only from official sources.
- Be wary of giveaways that seem too good to be true.
- Use strong, unique passwords and enable two-factor authentication on gaming accounts.
- Employ a reliable security solution to detect malicious files.
For gamers, the rise of cyber threats highlights the importance of cybersecurity awareness. Engaging with platforms that offer legitimate services and maintaining updated security solutions can help mitigate risks associated with these attacks.
Explore more about how you can protect your gaming experience at Gopher Security. Engage with us to enhance your digital security.




