Cybersecurity Alert: 94% of Passwords Are Not Unique - Learn Why
Cybersecurity Awareness: Password Habits and Risks
Password Reuse and Risks
A staggering 41% of successful logins across websites protected by Cloudflare involve compromised passwords. Many users recycle passwords across multiple services, which creates significant risk when credentials are leaked. According to a recent study, users will, on average, reuse their password across four different accounts. Even after major breaches, many individuals fail to change their compromised passwords or continue using variations across different services.
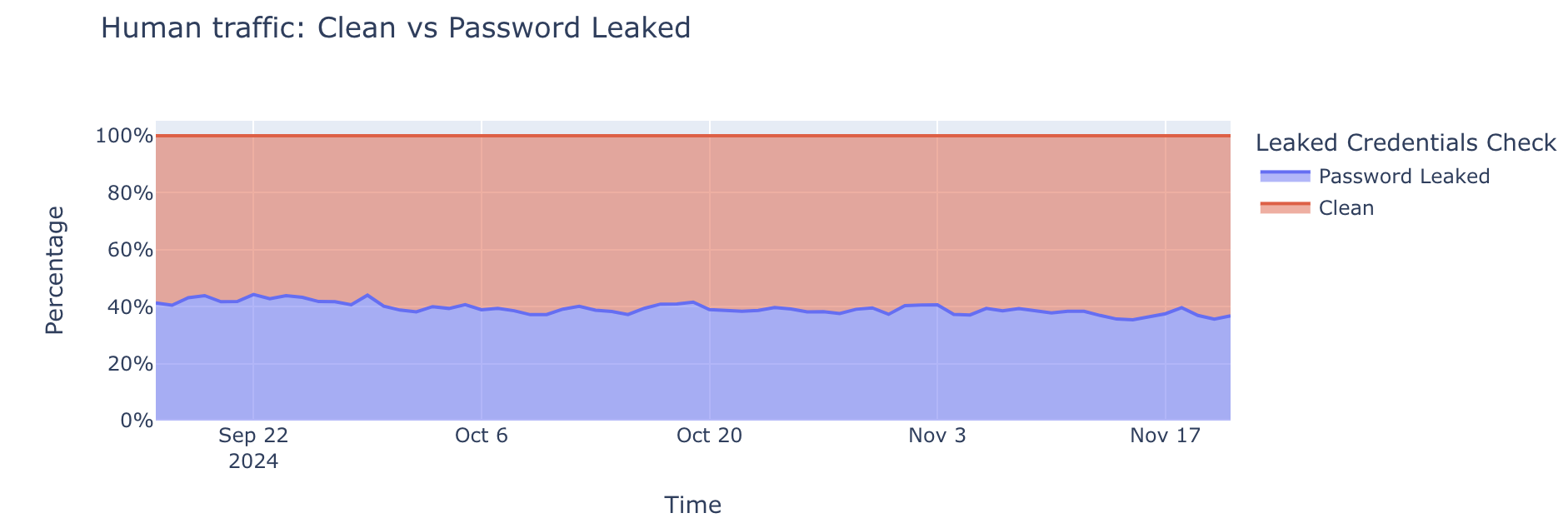
Image courtesy of Cloudflare
Common Password Pitfalls
Research indicates that 94% of leaked passwords are not unique, highlighting a widespread epidemic of weak password reuse. A study by Cybernews analyzed more than 19 billion leaked passwords, revealing that only 6% were unique. Additionally, passwords like "123456," "password," and "admin" remain prevalent. For instance, "1234" was found in approximately 727 million passwords.
Image courtesy of Mashable
According to Neringa Macijauskaitė, an information security researcher at Cybernews, "The ‘default password’ problem remains one of the most persistent and dangerous patterns in leaked credential datasets."
Emotional Manipulation in Scams
Cybersecurity expert Lisa Plaggemier emphasizes that scams often manipulate emotions rather than intellect. Many consumers remain vulnerable because security practices can seem intimidating. The National Cybersecurity Alliance aims to alleviate this fear through educational initiatives, including workbooks and online series like "Kubikle," which has garnered significant attention.
To learn more about avoiding scams, visit Stay Safe Online.
Password Management Techniques
CNET's survey shows that 49% of US adults have risky password habits, including reusing passwords across multiple accounts. Attila Tomaschek, a digital security expert, warns that "reusing the same password across multiple accounts puts users at risk of getting their online accounts compromised through a credential stuffing attack."
To combat these issues, users are advised to:
- Utilize a password manager to create and store strong passwords.
- Enable multi-factor authentication (MFA) wherever possible.
- Regularly update passwords and avoid using personal information.
For more information on managing passwords, check out the recommendations by CNET.
The Impact of Credential Stuffing Attacks
Credential stuffing attacks have become prevalent, with bots driving 95% of login attempts involving leaked passwords. These automated attacks target websites at scale, exploiting the fact that many users reuse passwords. According to Cloudflare, 76% of leaked password login attempts for websites built on WordPress are successful, with a significant number of these logins executed by unauthorized systems.
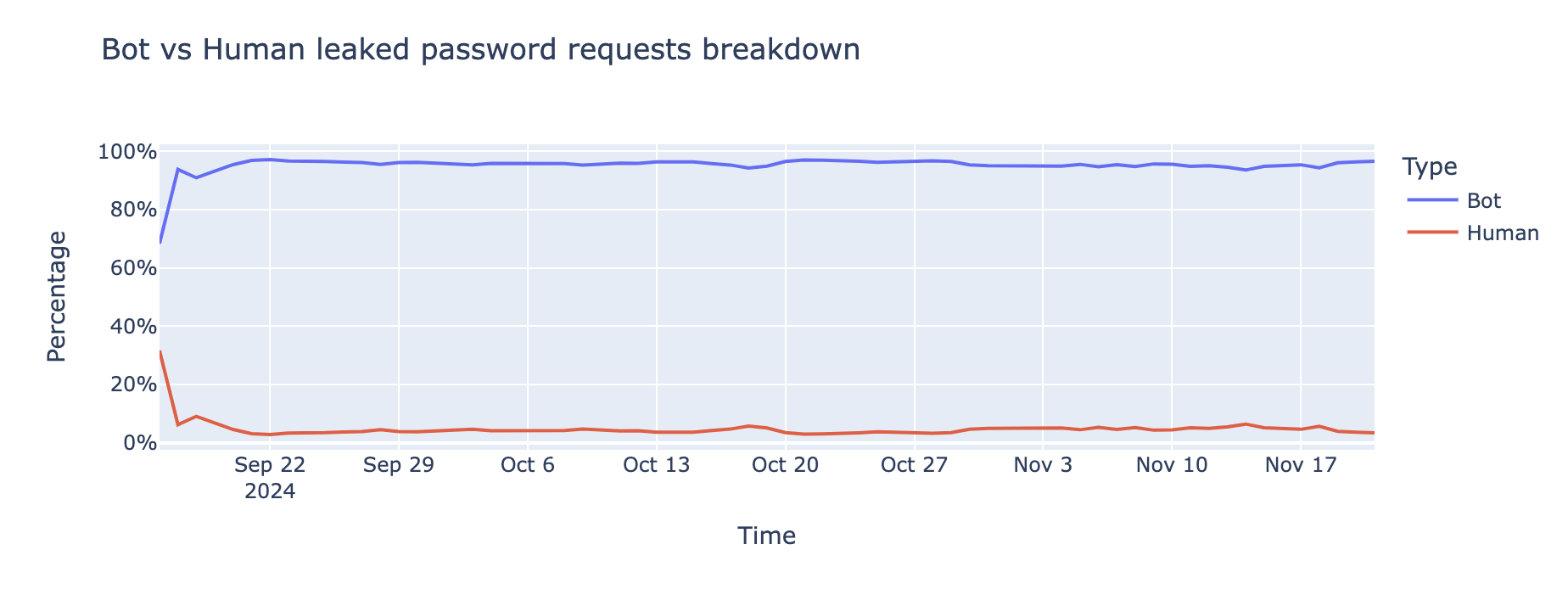
Image courtesy of Cloudflare
To mitigate these risks, organizations should implement features like rate limiting and bot management tools and conduct regular audits of password reuse patterns.
Strong Password Recommendations
To create strong passwords, experts suggest:
- Use passwords that are at least 12 characters long, incorporating a mix of uppercase and lowercase letters, numbers, and special characters.
- Avoid using recognizable words, personal information, or common sequences.
- Regularly monitor for credential leaks and enforce robust password hygiene policies.
For further reading on creating strong passwords, refer to CISA's guidance on strong passwords.
Conclusion
The prevalence of weak, reused passwords across various platforms significantly increases the risk of cyberattacks. By adopting strong password practices and using tools like password managers, individuals and organizations can better protect themselves against unauthorized access and data breaches.





