Databricks Unveils Data Intelligence Platform for Cybersecurity
Databricks Announces Data Intelligence for Cybersecurity
Databricks launched Data Intelligence for Cybersecurity to help organizations defend against modern and AI-driven threats with enhanced accuracy, governance, and flexibility. This platform integrates with existing security stacks, centralizing data and leveraging an open partner ecosystem to detect risks earlier, understand attack contexts, and respond swiftly.

Key Features and Benefits
- AI Agents for Security: Agent Bricks enables security teams to build and deploy AI agents rapidly, enhancing precision in handling threats.
- User-Friendly Insights: The platform provides intuitive dashboards and AI-powered natural language search capabilities, making security insights accessible to both technical and non-technical users.
- Unified Data Foundation: Databricks' Lakehouse architecture consolidates enterprise data across systems for comprehensive visibility, overcoming limitations of legacy SIEM tools.
Omar Khawaja, VP of Security and Field CISO at Databricks, stated, "With Data Intelligence for Cybersecurity, Databricks is making data and AI every organization’s strongest defense strategy."
Customer Transformations
Several leading organizations have reported significant improvements using the Data Intelligence platform:
- Arctic Wolf processes over 8 trillion security events weekly, enhancing their AI-driven security capabilities.
- Barracuda Networks achieved a 75% reduction in daily processing costs and real-time alerting in under 5 minutes.
- Palo Alto Networks accelerated AI-powered threat detection by 3x, reducing operational costs.
- SAP Enterprise Cloud Services improved its threat processing speed and reduced engineering time by 80%.
Partner Ecosystem
Databricks has introduced partner integrations with various providers, including Abnormal AI, Accenture Federal, ActiveFence, and others, to enhance its cybersecurity offerings.
For more information, visit the Databricks blog and explore the Data Intelligence for Cybersecurity solutions and resources pages.
Databricks and BigID Collaboration
BigID, a leader in data security and privacy, announced its role as a launch partner for Databricks' Data Intelligence Platform for Cybersecurity. This partnership aims to provide data intelligence and governance for sensitive data, enhancing security operations.

Key Takeaways from the Collaboration
- Continuous Visibility: BigID’s data security posture management (DSPM) offers organizations ongoing visibility into sensitive and AI data across the Databricks Lakehouse.
- AI Trust and Compliance: The integration enforces AI TRiSM guardrails within Databricks’ Unity Catalog, enhancing compliance and control over AI data pipelines.
- Strengthened Security Posture: Organizations can classify, cleanse, and control data to reduce risks while ensuring high-quality training sets for AI.
Ian Williamson, SVP of Alliances at BigID, commented, “By bringing DSPM into the Databricks Lakehouse, BigID gives organizations continuous visibility into sensitive data and the ability to build high-quality, compliant training sets.”
Databricks and DataBahn Partnership
Databricks' Data Intelligence Platform for Cybersecurity, in collaboration with DataBahn, aims to redefine cybersecurity by transforming chaotic telemetry into actionable insights. This partnership facilitates the transition from reactive log management to proactive security intelligence.
Transforming Data Overload into Intelligence
The cybersecurity industry faces challenges due to excessive data ingestion, leading to inefficiencies. Databricks provides the scalability needed to deal with vast amounts of telemetry, while DataBahn enhances data collection and enrichment processes.
Key Features of the Partnership
- AI-Powered Data Pipeline: DataBahn automates the ingestion and processing of security telemetry, ensuring high-quality data flows to Databricks.
- Natural Language Processing: Security analysts can query data in natural language, receiving contextual answers immediately.
- Optimized Security Workflows: By leveraging AI, organizations can filter out low-value data, enrich it automatically, and accelerate time to insight.
This partnership emphasizes a shift toward a more intelligent approach to data management in cybersecurity, allowing enterprises to gain confidence and speed in their security operations.
For further details, refer to the DataBahn blog on headless cyber architecture.
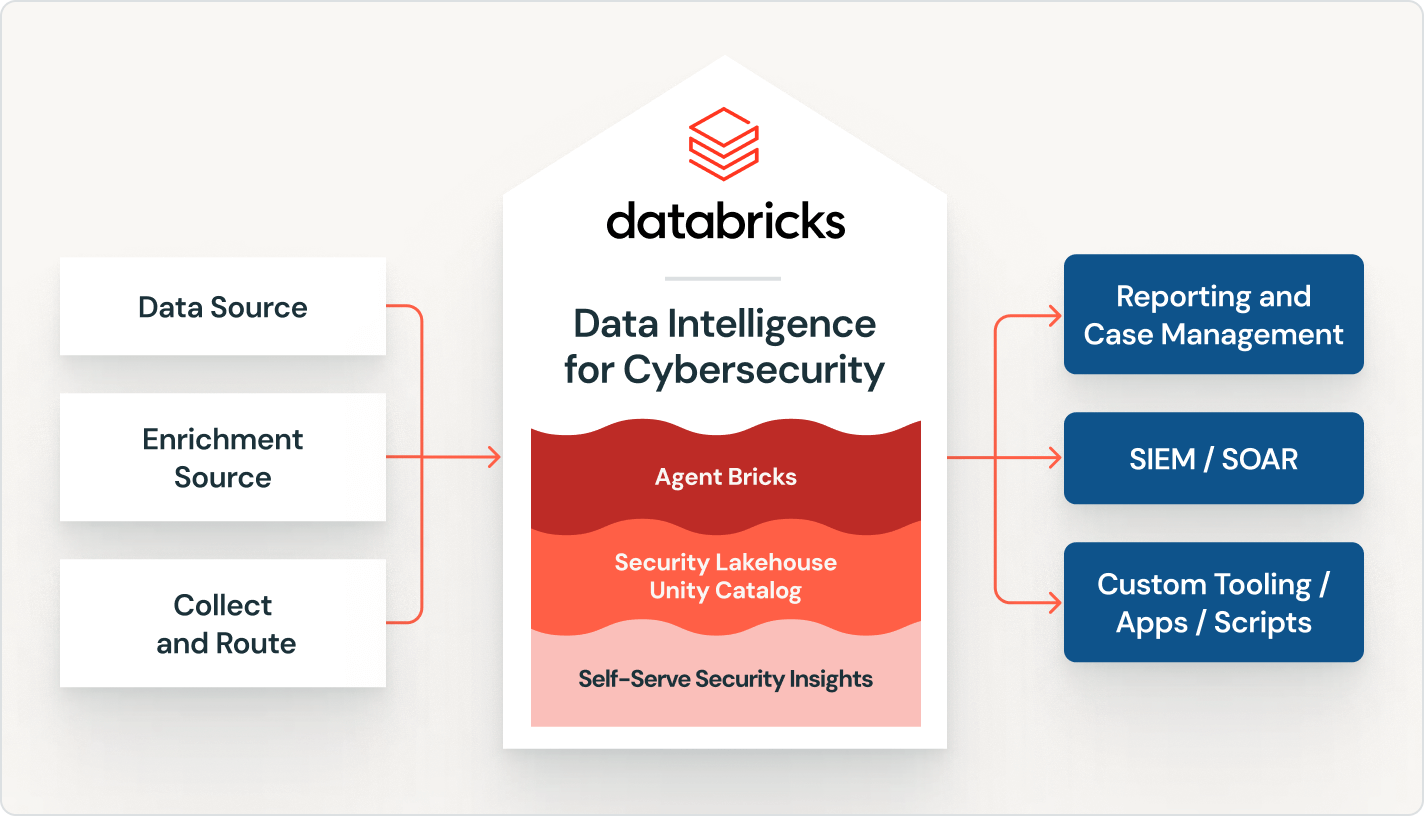
Data Intelligence for Cybersecurity Platform Features
The Data Intelligence for Cybersecurity platform provides a comprehensive solution for unifying enterprise data and democratizing security analytics. Here are the key functionalities:
Unified Security Lakehouse
Databricks offers a security lakehouse that centralizes security, IT, and business data, optimizing performance and cost without vendor lock-in.
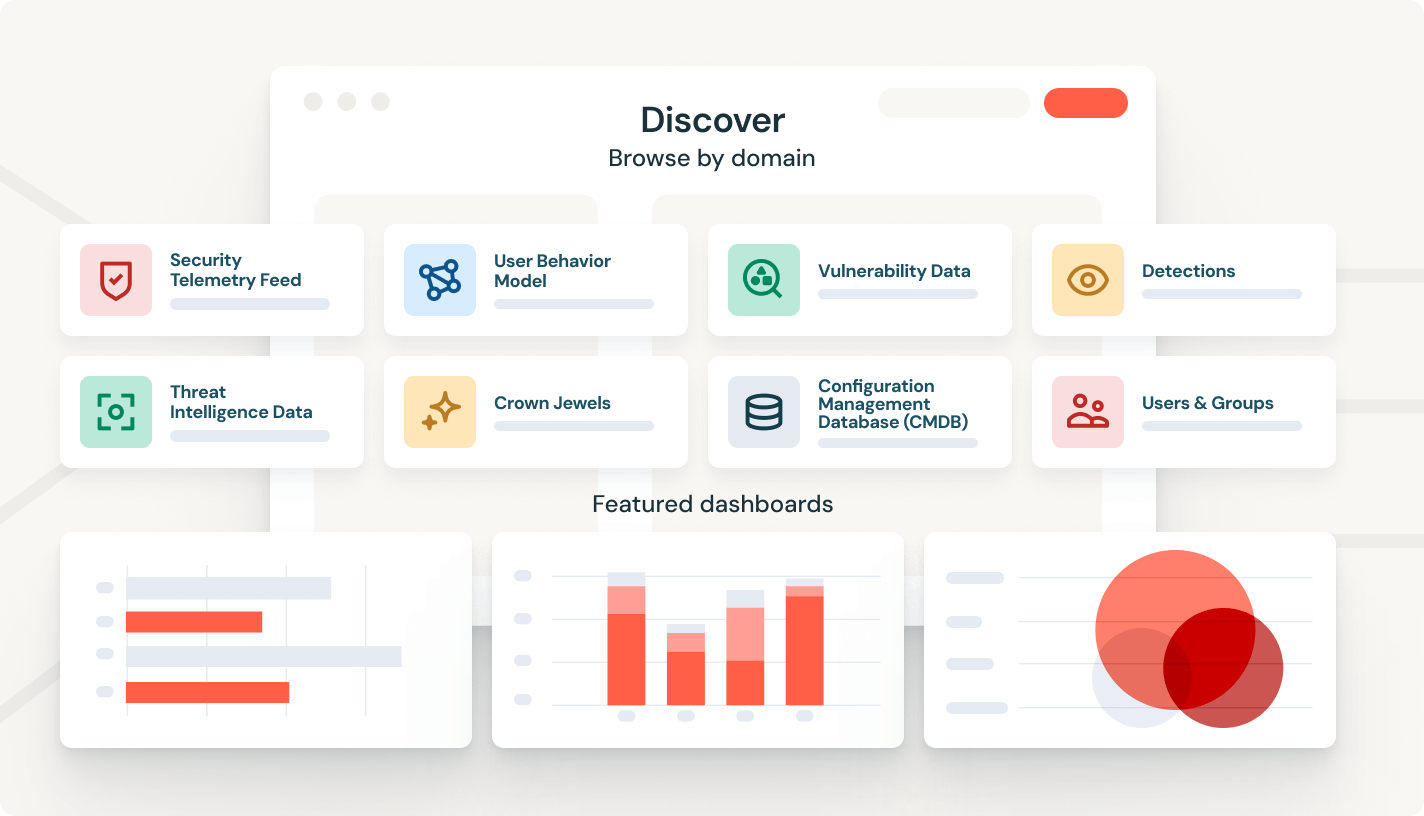
Real-Time Security Insights
The platform equips users with AI-powered dashboards and analytics tools to convert siloed data into strategic security advantages.

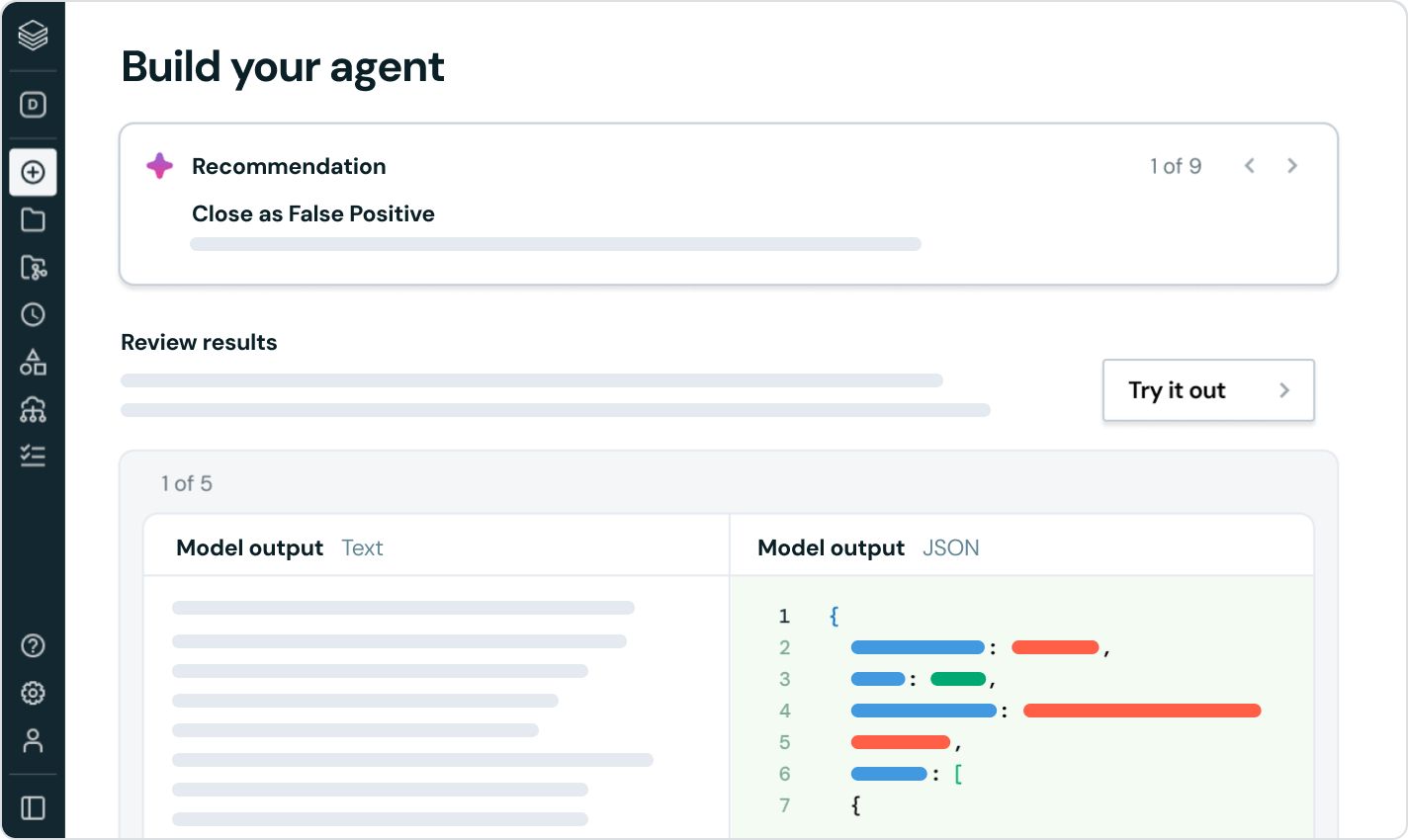
Secure Agents with Agent Bricks
Agent Bricks allows teams to create production-ready AI agents for cyber defense, enhancing response speed and accuracy.
Governance, Risk, and Compliance
Unity Catalog ensures strong data governance, tracking lineage and permissions to meet security and regulatory requirements.
For more information on how Databricks is transforming cybersecurity, check out the Solution Accelerators and available resources on AI-driven defense.





