Exploring Oktacron: A Unique Cyber Security News Aggregator
Matanbuchus Loader Analysis
Overview of Matanbuchus Loader
Matanbuchus is a Malware-as-a-Service (MaaS) loader that has been available on underground markets since February 2021. It is marketed for a monthly rental price between $3,000 and $4,500. This loader is primarily utilized to download and execute various payloads, including Qbot and Cobalt Strike beacons, often delivered via macro code embedded in Microsoft Office documents. Matanbuchus operates in two stages, with the first stage focused on environment checks and the second stage dedicated to payload execution.
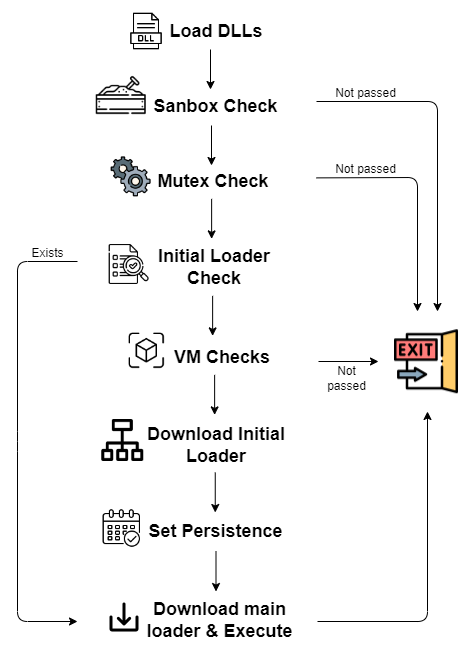
Loader Stages
The initial loader (first stage) performs checks to determine if the environment is being monitored. If it detects a secure environment, it will proceed to load the main loader (second stage), which is responsible for executing the attacker's payload. The second stage employs a variety of sophisticated techniques to bypass security measures.
Capabilities and Features
The Matanbuchus loader supports numerous commands to facilitate payload execution, including:
- Running executables, both with and without parameters
- Executing DLL files using rundll32.exe or regsvr32.exe
- Running CMD and PowerShell commands
- Executing in a fileless manner
- Updating and uninstalling itself
- Sleeping between commands
The loader's architecture allows it to communicate effectively with its Command and Control (C2) server, which directs the payload execution based on information gathered about the victim's machine.
Initial Loader Details
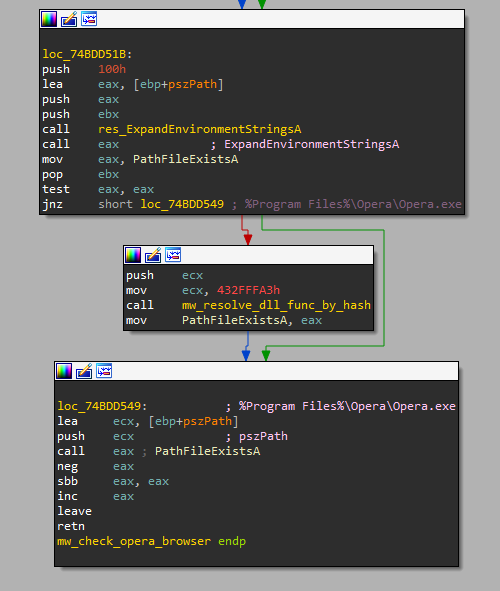
The first stage of Matanbuchus primarily checks for monitoring tools. It creates a working folder to store its binaries, ensuring persistence through scheduled tasks. The loader is designed to exit if specific conditions are met, such as the presence of the Opera web browser, which is often associated with sandbox environments.
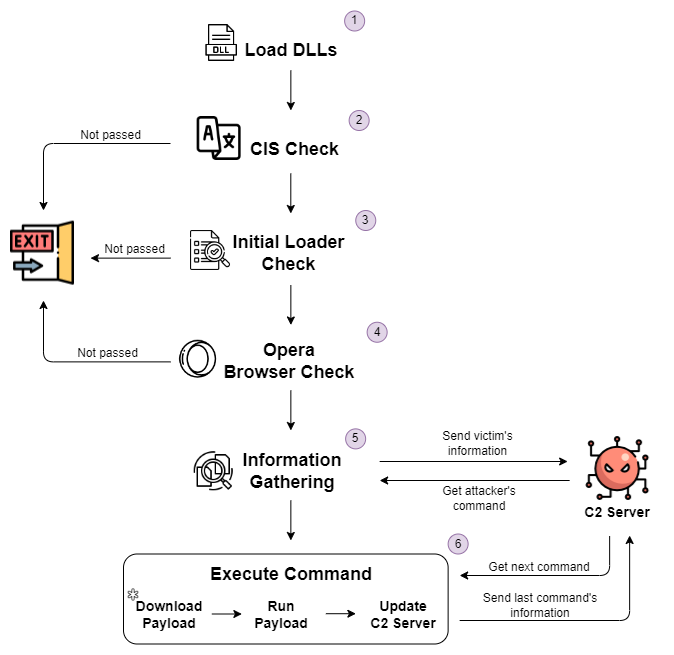
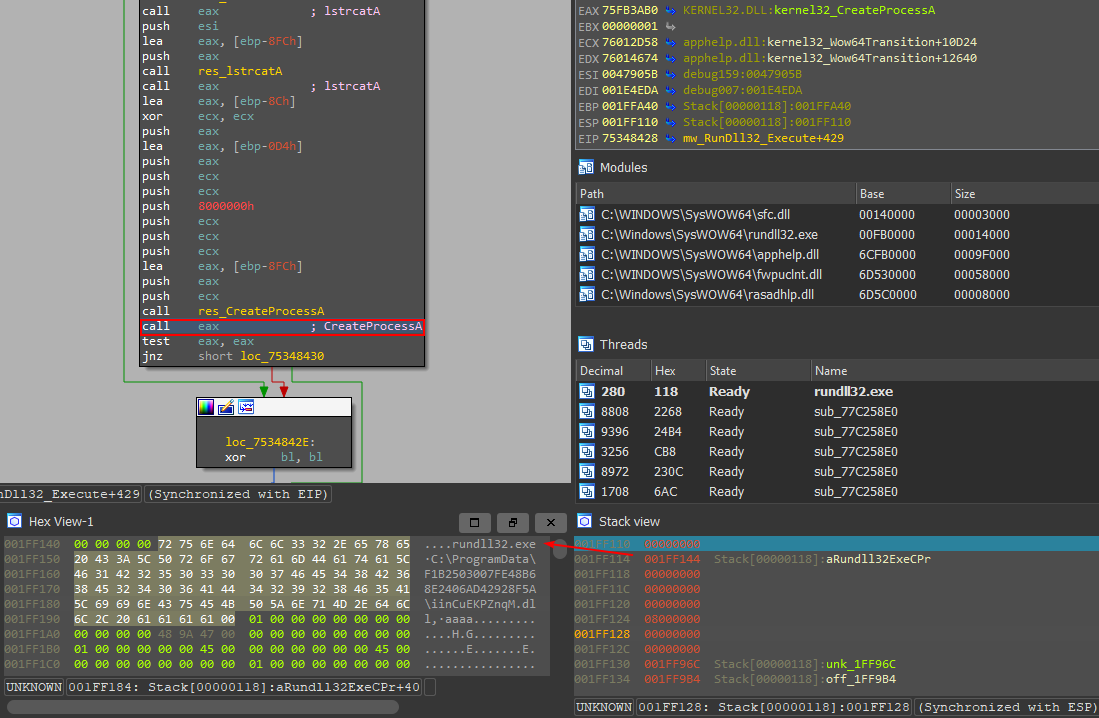
Main Loader Analysis
The second stage of Matanbuchus is where the real activity occurs. It collects system information and communicates with the C2 server using encrypted JSON data. The server responds with instructions on what payload to execute next.
Machine Checks
Matanbuchus performs several checks to determine if the target environment is suitable for an attack, including:
- A CIS check to avoid targeting victims from the Commonwealth of Independent States
- Verifying the existence of its working folder
- Checking for the presence of specific software, such as the Opera browser
Payload Execution Mechanisms
The loader supports multiple methods for executing payloads, including:
- Downloading and executing executables from a specified URL
- Running scripts with administrator privileges
- Executing DLLs via rundll32.exe or regsvr32.exe
- Running commands directly in the command line or PowerShell
- Conducting fileless execution, which avoids writing payloads to disk
Each method is carefully crafted to evade detection and maximize the chances of successful execution.
Communication with C2 Server
Matanbuchus sends encrypted data to the C2 server, which contains information about the victim's machine. The server then sends back commands for further actions, allowing for dynamic control over what the loader does next.
This command-and-control structure is a critical aspect of the loader's functionality, enabling attackers to adapt their approach based on the specifics of the compromised environment.
Conclusion
The Matanbuchus loader exemplifies the sophistication of modern malware. Its dual-stage architecture, combined with a robust set of execution commands and stealth techniques, makes it a formidable tool in the hands of cybercriminals. Understanding its workings can help cybersecurity professionals develop better defenses against such threats.
For those looking to enhance their cybersecurity measures, exploring advanced protection solutions can be vital. Consider contacting undefined at undefined for more information on safeguarding your systems.



