First Health Advisory: AHA's Preferred Cybersecurity Provider
First Health Advisory Named Preferred Cybersecurity & Risk Provider by the American Hospital Association
First Health Advisory has been designated as a Preferred Cybersecurity & Risk Services Provider by the American Hospital Association (AHA), which represents nearly 5,000 hospitals and health systems. This recognition highlights First Health's commitment to enhancing cybersecurity strategies and risk management within the healthcare sector.
John Riggi, National Advisor for Cybersecurity and Risk at AHA, stated, "First Health Advisory has been selected by the AHA as an excellent solution provider for the Cybersecurity Oversight & Resilience Engagement (CORE) Program." He emphasized the importance of reliable partners in defending against cyberthreats and ransomware attacks.
Carter Groome, CEO of First Health Advisory, noted, "In healthcare, we don't need more people pointing out problems; we need true partners who will solve them and actually reduce risk." This partnership aims to improve operational resilience in hospitals, allowing healthcare professionals to focus on patient care.
As part of this collaboration, First Health will implement its CORE Program, which offers strategic oversight to identify and mitigate cybersecurity risks. The program is designed to enhance hospital defenses and ensure compliance with regulatory standards, thereby safeguarding patient care.

Image courtesy of First Health Advisory
For further details on First Health's services, visit: First Health Advisory and learn more about AHA's program at American Hospital Association Cybersecurity Providers.
AHA Preferred Cybersecurity Provider Program
The AHA has established the Preferred Cybersecurity & Risk Provider Program to assist hospitals and health systems in managing cyber threats. This initiative identifies trusted providers that offer vetted services to help healthcare organizations safeguard their operations.
Ransomware attacks extend beyond data theft; they pose significant risks to patient care and hospital operations. Cybersecurity is crucial for maintaining the integrity of healthcare delivery systems. The AHA aims to connect its members with reputable cybersecurity service providers to fortify defenses against these evolving threats.

The AHA lists various Preferred Cybersecurity Providers that offer a range of services:
- First Health Advisory: CORE Program (Cybersecurity Oversight & Resilience Engagement) and Data Privacy Governance Assessment.
- AON: Cyber Incident Response and Risk Management.
- Censinet: Cyber Firm Risk Management and Information Governance.
- CLEAR: Identity Verification services.
For a complete list, visit Meet our Preferred Cybersecurity Providers.
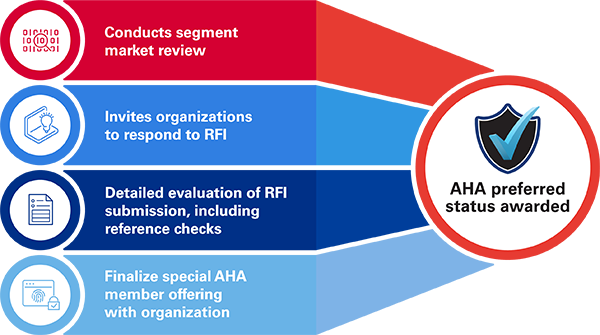
Image courtesy of AHA
For more information on AHA's resources, check Cybersecurity & Risk Advisory Resources.
Updates from First Health Advisory
First Health Advisory continues to bolster its leadership team and expertise in the industry. Recently, CEO Carter Groome was recognized as NACD Directorship Certified®, indicating a commitment to high standards in board leadership. Additionally, Emily Branzell Varga has joined the company as Director of Marketing, bringing her extensive experience in healthcare marketing.
Moreover, David Finn, a digital health expert, has been appointed to the Advisory Board to advance strategic initiatives in digital health technology.
For more updates, visit News – First Health Advisory.
By implementing robust cybersecurity measures, First Health Advisory reinforces its position as a vital partner in protecting healthcare organizations against increasing cyber threats.





