Hackers Use Microsoft Teams to Spread Matanbuchus 3.0 Malware
Matanbuchus 3.0 Malware Loader
Cybersecurity researchers have identified a new variant of the Matanbuchus malware loader that incorporates advanced stealth features to evade detection. Matanbuchus is categorized as a malware-as-a-service (MaaS) offering, capable of facilitating next-stage payloads like Cobalt Strike beacons and ransomware. Initially advertised in February 2021 on Russian-speaking forums for a rental fee of $2,500, Matanbuchus has been utilized through ClickFix-like lures to mislead users visiting legitimate yet compromised sites.

Matanbuchus is primarily spread through hands-on social engineering rather than traditional methods like spam emails or drive-by downloads. Attackers directly manipulate users to deploy the malware, thus making it more targeted. The latest version, Matanbuchus 3.0, features enhanced communication protocols, in-memory capabilities, advanced obfuscation, and supports CMD and PowerShell reverse shells, as noted by Morphisec.
The malware was spotted in incidents where companies were targeted via Microsoft Teams impersonations, tricking employees into launching Quick Assist for remote access and executing a PowerShell script that installed Matanbuchus. This approach has been similarly employed by actors affiliated with the Black Basta ransomware operation.
Morphisec's CTO, Michael Gorelik, stated, "Victims are carefully targeted and persuaded to execute a script that triggers the download of an archive," which contains a disguised Notepad++ updater and a malicious DLL representing the Matanbuchus loader.
Matanbuchus 3.0 is available for $10,000 monthly for the HTTPS version and $15,000 for the DNS version. Once initiated, the malware collects system information and checks for security tools, sending the data to a command-and-control (C2) server to receive additional payloads.
Gorelik elaborated on the complexity of Matanbuchus, noting the advanced scheduling techniques used for task creation through COM object manipulation and shellcode injection. The loader can execute various commands, making it a significant risk for compromised systems. As malware-as-a-service evolves, Matanbuchus 3.0 exemplifies a shift towards stealth-oriented loaders using living-off-the-land binaries and enterprise collaboration tool exploitation.
Ongoing Cyber Threats and Vulnerabilities
In a recent report, the Google Threat Intelligence Group (GTIG) has attributed a campaign targeting fully-patched SonicWall Secure Mobile Access (SMA) 100 series appliances to a threat actor known as UNC6148. They have been deploying a backdoor called OVERSTEP since at least October 2024, exploiting stolen credentials and OTP seeds to regain access even after security updates were applied.

Additionally, researchers have disclosed a critical design flaw in delegated Managed Service Accounts (dMSAs) in Windows Server 2025. This vulnerability can enable cross-domain lateral movement and persistent access to all managed service accounts, posing a severe risk to Active Directory environments.
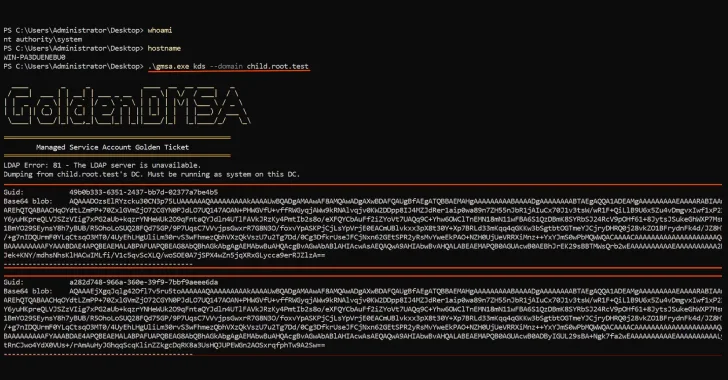
With the rise of AI in cybersecurity, the need for identity-first security has become increasingly vital. AI agents, while offering automation capabilities, often require high-privilege credentials that are not easily monitored, raising concerns about security gaps.

For organizations looking to stay ahead of evolving cyber threats, it's crucial to implement robust security measures that account for these vulnerabilities. Monitoring and managing access can dramatically enhance security postures against sophisticated threats.
Explore our services at undefined or contact us for tailored cybersecurity solutions. We are here to help you navigate the complexities of today’s cyber landscape.



