Interlock Ransomware Targets Industries with New PHP-Based RAT
Interlock Ransomware and FileFix Delivery Mechanism
Overview of FileFix Technique
FileFix is a new malware deployment technique that has emerged as a significant threat in ransomware attacks. Building on the previously known ClickFix technique, FileFix tricks users into executing commands via Windows File Explorer. Initially, victims are led to believe they are solving a legitimate problem, such as a CAPTCHA or a virus alert, prompting them to paste a seemingly harmless string into the File Explorer address bar.

The command that users paste is designed to download and execute malware, specifically a PHP-based variant of the Interlock Remote Access Trojan (RAT). This technique has been noted for its ability to evade traditional antivirus solutions and Windows’ built-in protections.
Interlock Ransomware Evolution
The Interlock ransomware has evolved rapidly, with its new PHP variant being observed in widespread campaigns since May 2025. This new variant, dubbed the Interlock RAT (PHP edition), was deployed using the FileFix technique and has been linked to various industries, including healthcare and local government.
Research from The DFIR Report indicates that the Interlock RAT can gather extensive system information, enumerate Active Directory, and check for backups. The RAT's capabilities enable it to deploy the Interlock ransomware encryptor after gaining initial access.
The first detection of Interlock occurred in late September 2024, and it has since gained notoriety for employing double-extortion tactics, where sensitive data is exfiltrated before encryption. Victims of this ransomware have included notable organizations such as Wayne County, Michigan, and Texas Tech University Health Sciences Center.
Technical Details of the Interlock RAT
Upon execution, the PHP variant of the Interlock RAT immediately begins automated reconnaissance on the compromised system. It uses PowerShell commands to collect data, including:
- System specifications
- Running processes and services
- Mounted drives and network details
This data is exfiltrated in JSON format back to the attackers, who can then leverage the information to understand the context of the compromise. The malware establishes a command-and-control (C2) channel using Cloudflare Tunnel, which masks the true location of the C2 server. Hard-coded IP addresses serve as fallback mechanisms to ensure continuous communication with the attackers.
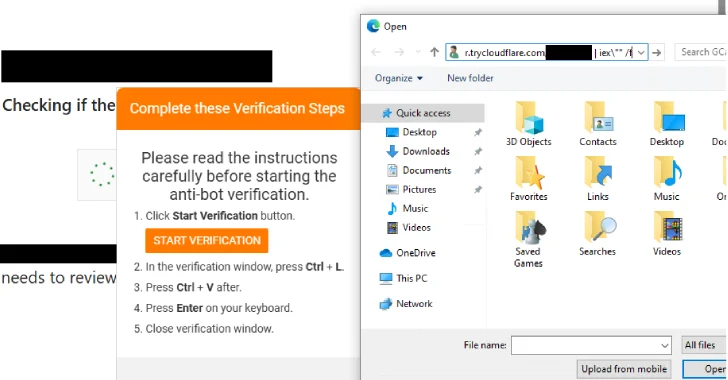
Delivery Mechanism and Social Engineering
The FileFix technique is a sophisticated evolution of ClickFix, which previously relied on misleading users into pasting commands into the Windows Run dialog. FileFix uses a subtle approach where users are prompted to interact with a fake CAPTCHA, after which they are instructed to paste a command that executes a PowerShell script leading to the deployment of the Interlock RAT.
This method relies heavily on social engineering, making it accessible even to less experienced cybercriminals. The attackers compromise legitimate websites, injecting malicious scripts that redirect users to the fake verification pages.
Researchers warn that the simplicity and effectiveness of the FileFix method may lead to its adoption by other threat actors, emphasizing the need for increased user awareness and security training.
Summary of Interlock's Capabilities
The Interlock RAT's functionality includes:
- Executing malicious files
- Establishing persistence through Windows Registry modifications
- Remote execution of commands
- Lateral movement via Remote Desktop Protocol (RDP)
The continued evolution of the Interlock group’s tactics highlights the importance of vigilance in cybersecurity practices. Organizations are encouraged to implement user training focused on recognizing social engineering tactics and to monitor for unusual PowerShell activity.
For more information on ransomware protection strategies, visit TechRadar or Infosecurity Magazine.



