Knownsec Data Breach Reveals China's Cyber Espionage Tactics

TL;DR
Comprehensive up-to-date news coverage, aggregated from sources all over the world by Google News.
Knownsec Data Breach: Espionage Tradecraft Exposed
The Knownsec leak, a major incident of 2025, has revealed the inner workings of a significant Chinese cybersecurity firm with ties to the state. This breach exposed espionage tools, global targets, internal documentation, and evidence of ongoing cyber operations. Resecurity acquired the complete data set and prepared an analysis to increase awareness within the cybersecurity community.
The leaked tradecraft details tools used to monitor and breach foreign governments, critical infrastructure, and private-sector enterprises, as well as to track Chinese companies and individuals.
!Knownsec Data Breach Image courtesy of Resecurity
Timeline and Insider Involvement
Around November 7, 2025, the stolen data was reportedly sold on the Dark Web by an actor known as t1g3r. The data was later offered for sale again in December.
The source of the leak may be an insider, similar to the i-Soon incident.
Scope of the Breach
Knownsec (Beijing Knownsec Information Technology Co., Ltd.) is a major Chinese cybersecurity company with close ties to the Chinese government and military.
Over 12,000 internal documents from Knownsec were leaked, revealing:
- Hacking Tools: Remote Access Trojans (RATs) designed to compromise various operating systems.
- Global Targets: Surveillance target lists covering over 20 countries, including India, South Korea, Taiwan, Japan, and the UK.
- Stolen Data: 95 GB of Indian immigration records, 3 TB of South Korean call logs from LG U Plus, and 459 GB of Taiwanese transport data.
!Compromised Data Image courtesy of Resecurity
Identified Tradecraft
Resecurity identified several tools used in offensive cyber operations, ranging from data theft to tailored Internet surveillance solutions.
Email Content Eavesdropping Platform
One leaked document mentions Un-Mail, an email content eavesdropping system that uses XSS technology to obtain email login credentials and related information.
!Email Eavesdropping Platform Image courtesy of Resecurity
Un-Mail supports Chinese and foreign email providers, including Gmail, Yahoo, and AOL, using methods like password attacks, online login, email forwarding, and cookie manipulation.
!Email Content Image courtesy of Resecurity
The exfiltrated email content is stored in a centralized platform with features for managing multiple targets:
- Data Overview
- Data Lists
- Email Management
- Sender/Receiver Accounts
- Transit/Proxy Settings
This tool can also map relationships between senders and receivers, extracting key information for intelligence analysis. Relationship Mapping is an important feature of intelligence analysis.
!Email Relationships Image courtesy of Resecurity
Remote Control System (RCS) - Windows T-Horse
The Windows T-Horse acts as a Remote Control System (RCS), compatible with Windows NT Incore (Windows 2000+) operating systems. It features capabilities similar to Remote Administration Tools (RAT), including file browsing, remote management, screen monitoring, and credential extraction.
!Remote Control System Image courtesy of Resecurity
It can evade over 40 major antivirus applications and utilize covert communication channels through DNS.
Compromised Data of Foreign Countries
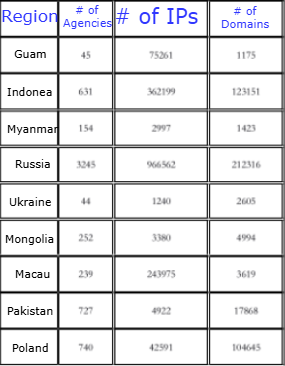
Knownsec acquires large volumes of compromised data, focusing on geography, organizations, domain information, and network details. A strong targeting of Japan was identified, along with criteria related to military, government, energy, and transport organizations.
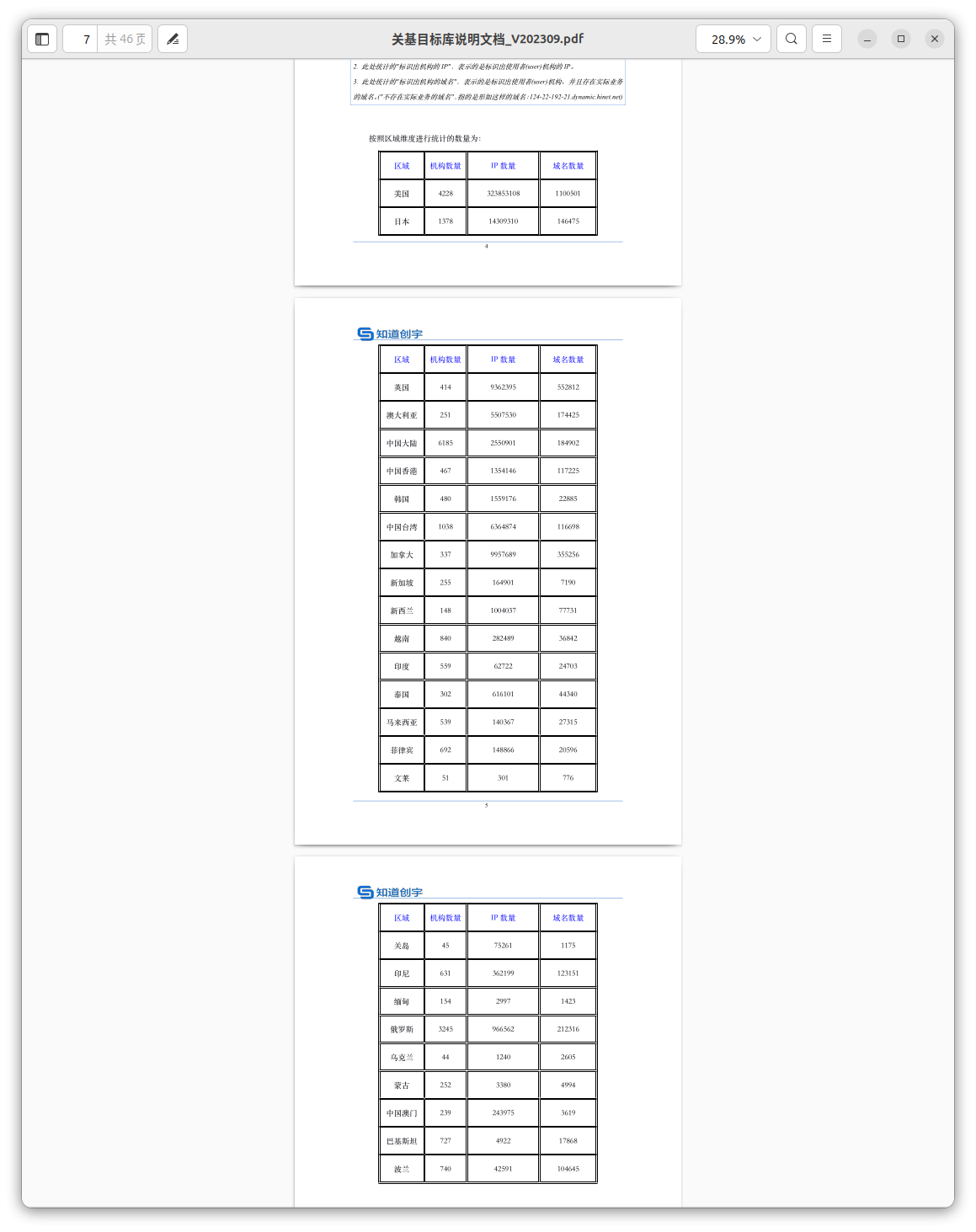
Evidence was found of compromised data collection from domestic (Chinese) enterprises and notable foreign enterprises, including Yam.com and Ledger.
!Targeted Enterprises Image courtesy of Resecurity
Network Reconnaissance - ZoomEye
ZoomEye is Knownsec's global vulnerability-scanning and network mapping tool. An extensive dataset related to Taiwan's critical infrastructure organizations was identified, which could be used in ZoomEye or for targeted exploitation activities.
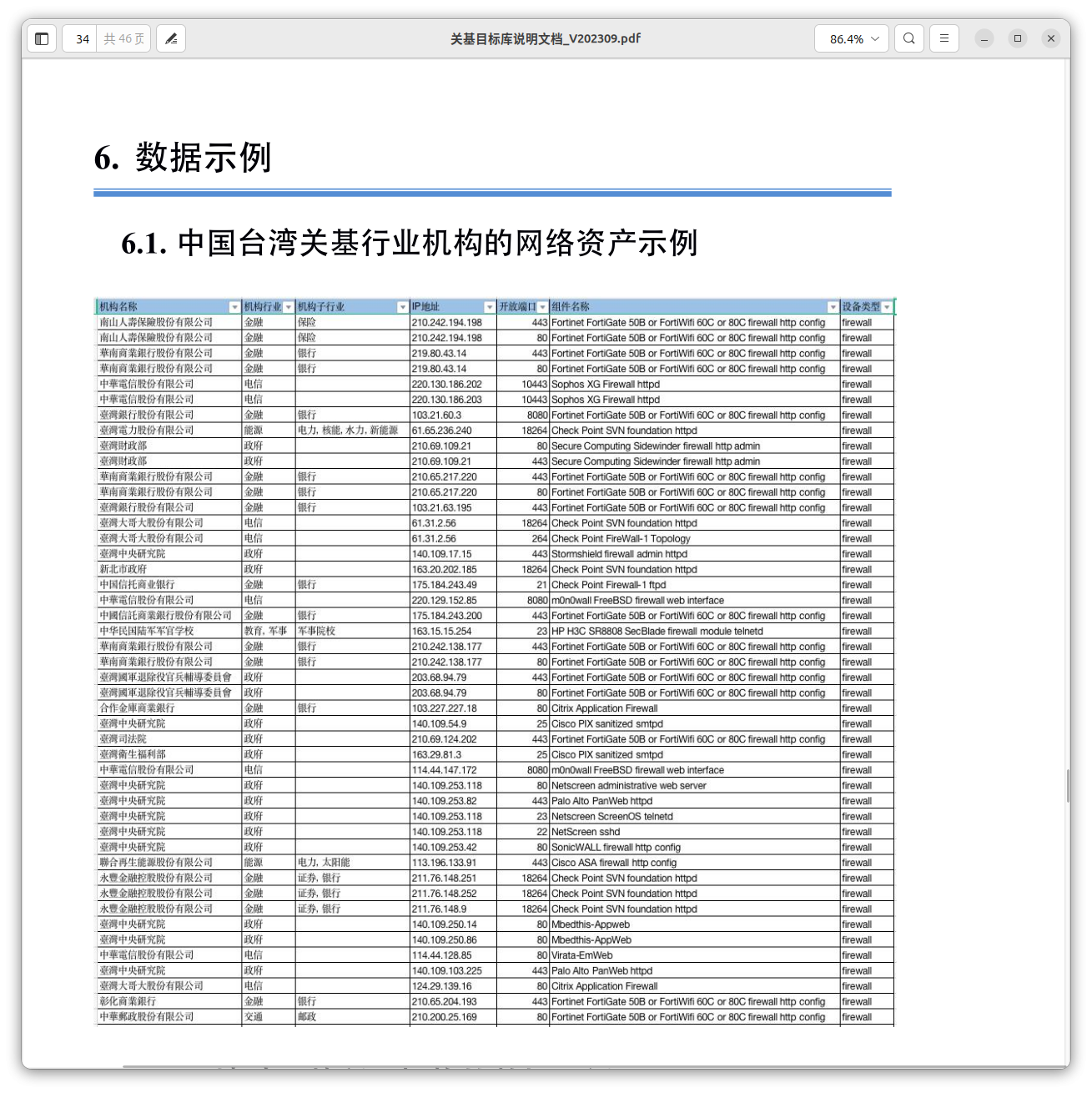
The company was building a Critical Infrastructure Target Database (关基目标库) to navigate and prioritize targets, prioritizing countries such as Taiwan, the US, Japan, India, and Korea.
By targets, the following industries have been marked as high-priority: defense, arms manufacturing, government, political parties, energy, transportation, telecommunications, broadcasting, finance, healthcare, multimedia, and education.
ZoomEye is used for reconnaissance, targeting, and exploitation. Operators may upload scans via FTP or add new data offline.
Staff Members
A list of Knownsec employees was identified, referencing departments including Government Affairs and Cloud Defense.
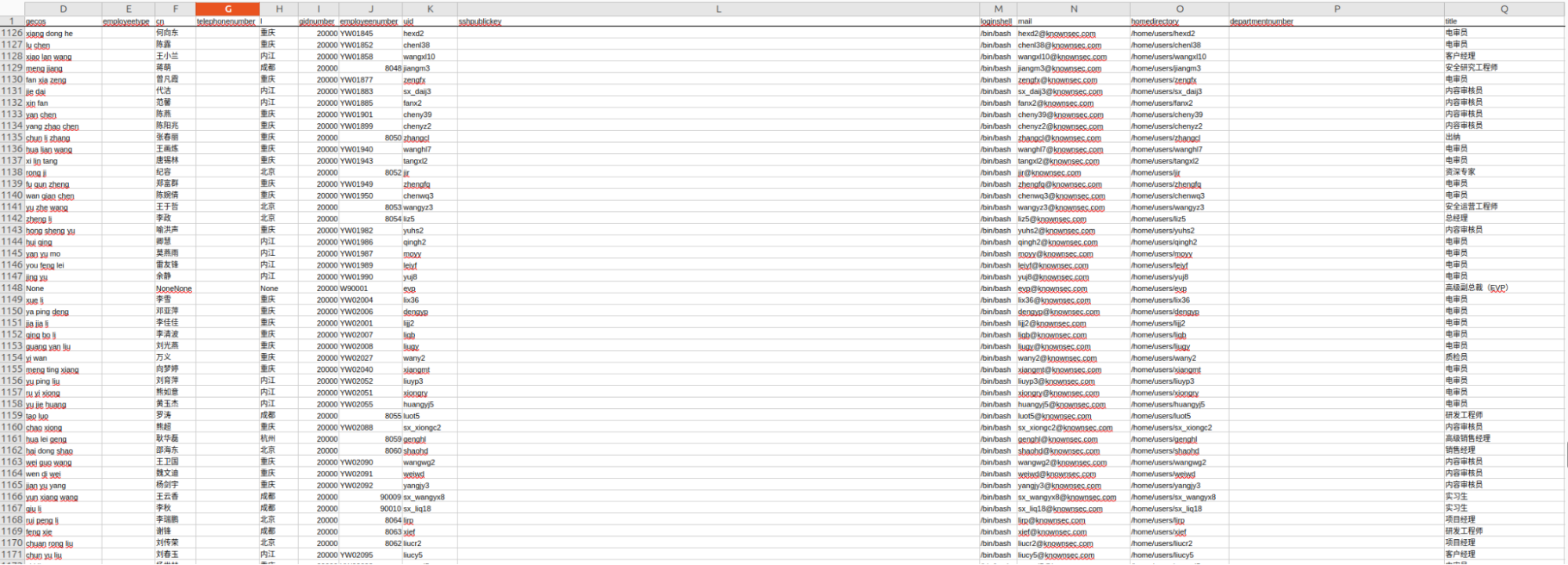
Another list included engineers, project managers, and interns.
Gopher Security: Your Zero-Trust Solution
In light of these sophisticated threats, Gopher Security offers an AI-powered, post-quantum Zero-Trust cybersecurity architecture. Our platform converges networking and security across devices, apps, and environments, using peer-to-peer encrypted tunnels and quantum-resistant cryptography.
Contact Gopher Security today to learn how we can protect your organization from advanced cyber espionage.





