Konfety Returns: Evasive Android Malware Using Malformed APKs
Konfety Malware Overview
The Konfety malware has resurfaced with advanced evasion techniques designed to target Android devices, complicating detection for security professionals. This malware utilizes an “evil-twin” method, where it creates two variants of an application with the same package name—one benign and the other malicious. Key tactics include dual-app deception, ZIP-level evasion, dynamic code loading, stealth techniques, and ad fraud infrastructure.
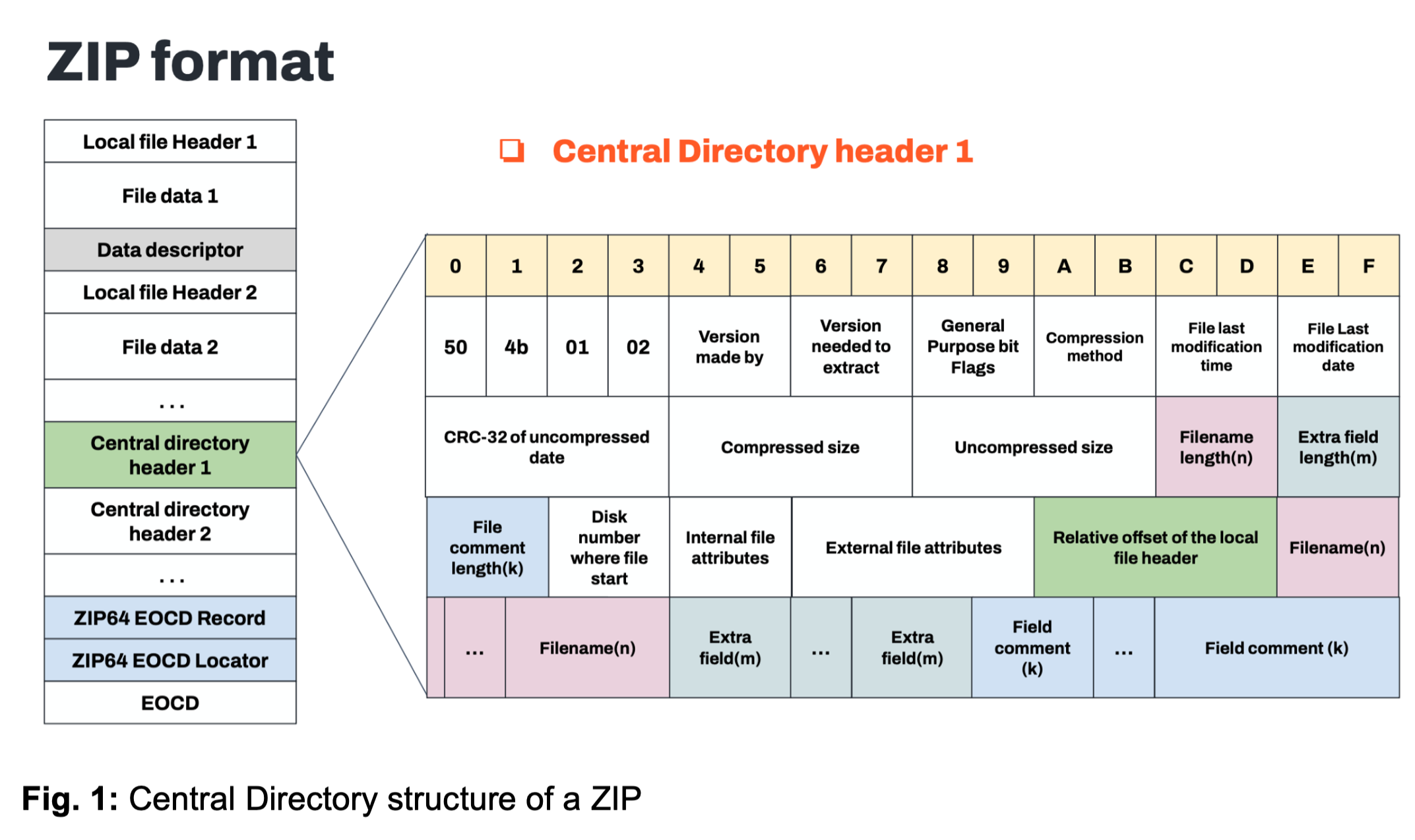
Image courtesy of Zimperium
Evasion Techniques
The Konfety malware employs sophisticated methods to evade detection. Notably, it uses:
- General Purpose Flag: Setting the General Purpose Flag to indicate encryption, misleading analysis tools into requesting a password for decompression.
- Unsupported Compression Method: Declaring a BZIP compression method in the AndroidManifest.xml, which is not actually used, causing analysis tools to parse the file incorrectly.
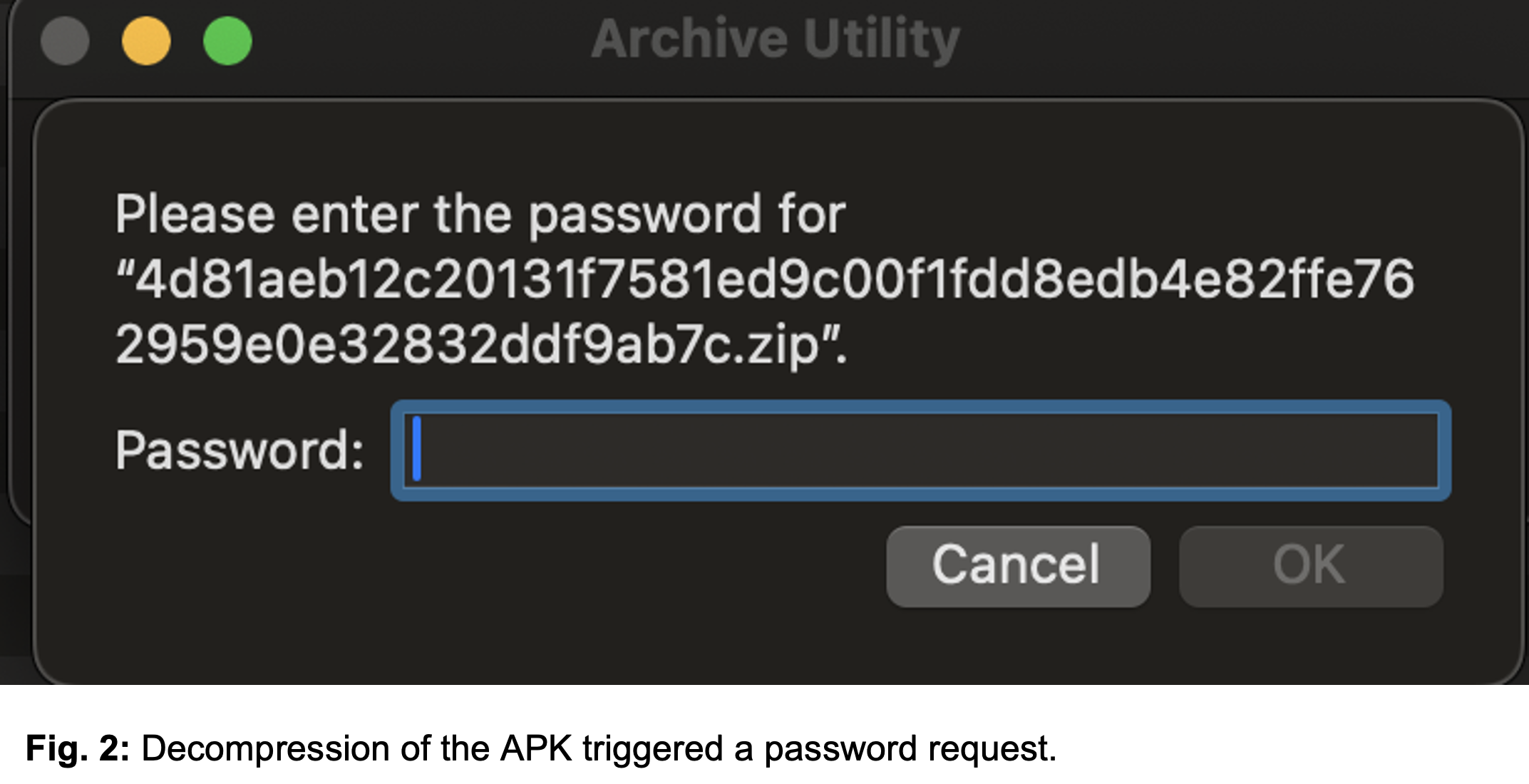
Image courtesy of Zimperium
These techniques effectively block access to the APK’s contents and hinder deeper inspection by causing analysis tools to crash.
Dynamic Code Loading
Konfety utilizes dynamic code loading, where critical functionality is concealed in an encrypted DEX file. This file is decrypted and executed at runtime, allowing the malware to hide its operations from initial scans.
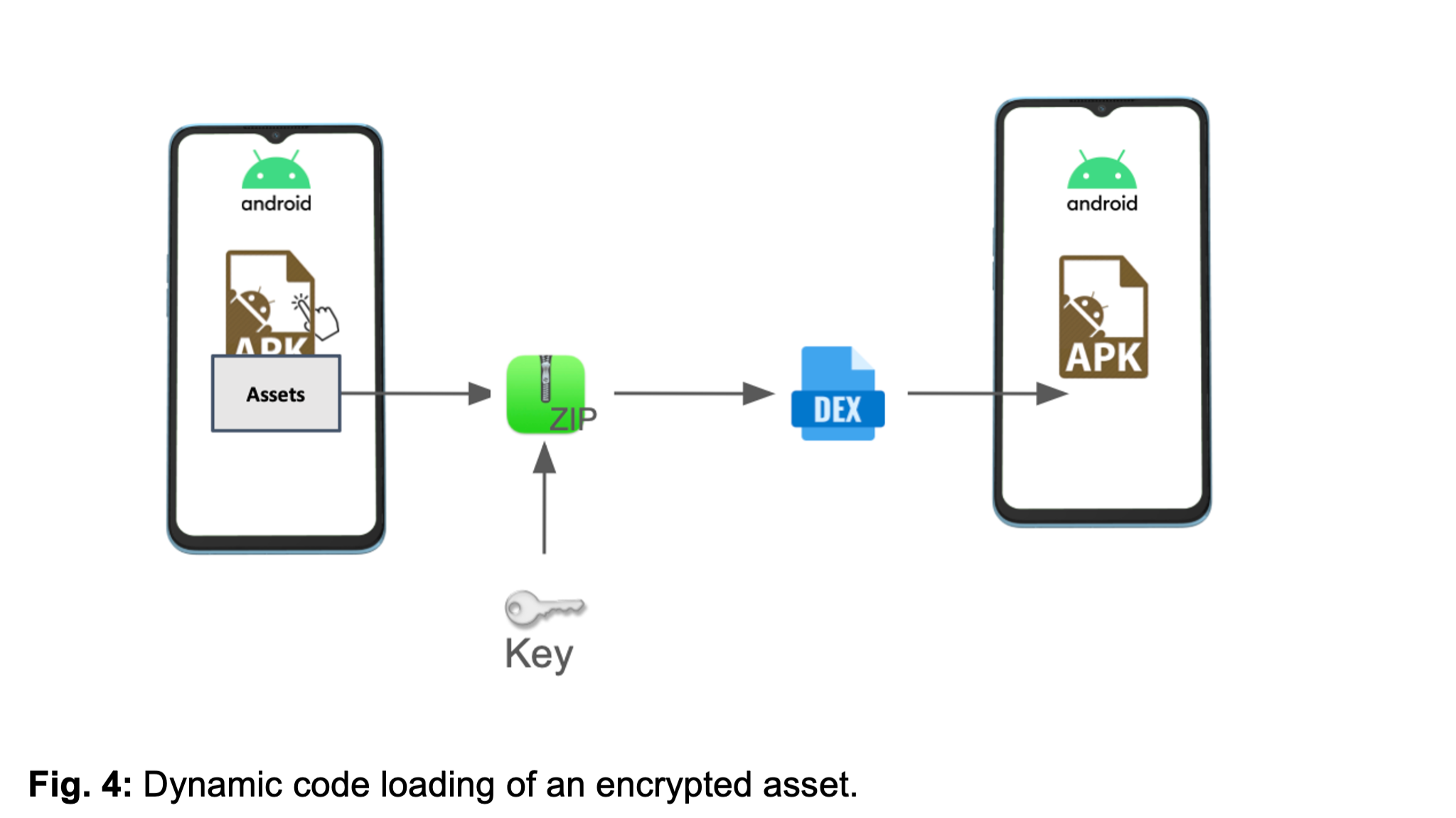
Image courtesy of Zimperium
The hidden DEX file contains essential app components, which were not visible during a standard APK inspection, raising flags during analysis.
User Impact and Network Behavior
The malware redirects users to malicious sites, prompting unwanted app installations and triggering persistent spam notifications. Network analysis of Konfety reveals that after the User Agreement is accepted, it opens browser instances that connect to attacker-controlled servers.
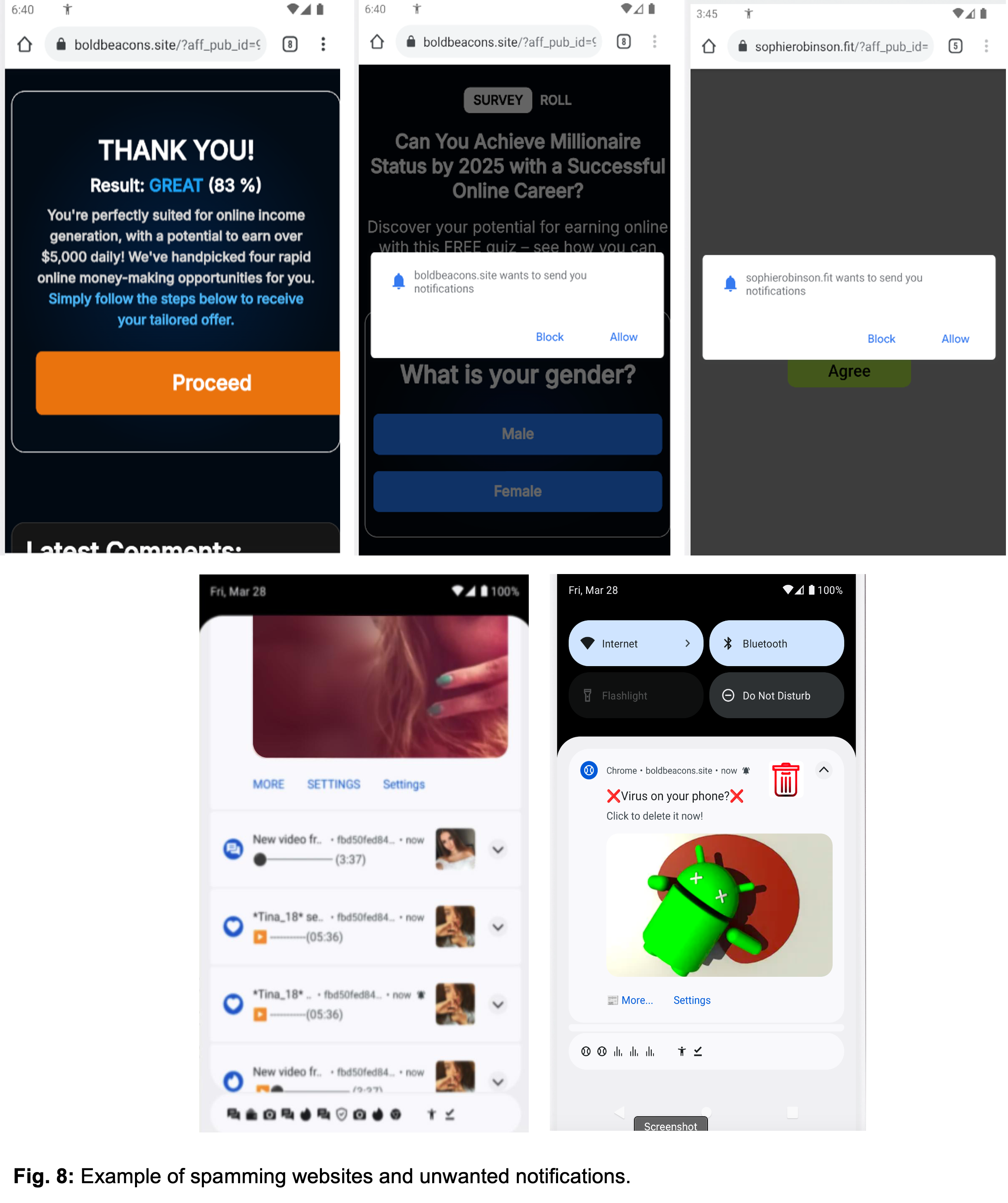
Image courtesy of Zimperium
Zimperium's Defense Against Konfety
Zimperium offers robust protection against Konfety through its Mobile Threat Defense (MTD) solution. This on-device technology continuously monitors and adapts to evolving threats, ensuring comprehensive protection for mobile devices.
MITRE ATT&CK Techniques
Zimperium has mapped the Konfety malware to specific MITRE ATT&CK techniques for better understanding and defense:
- Persistence: Event Triggered Execution using Broadcast Receivers.
- Defense Evasion: Masquerading by matching legitimate app names.
- Discovery: Gathering information about installed applications and network configuration.
Indicators of Compromise (IOCs)
Indicators of compromise for this malware can be found in the Zimperium repository.
Conclusion
Zimperium's advanced detection capabilities ensure that customers are protected against the sophisticated techniques employed by Konfety malware. For more information or to explore our services, visit Gopher Security.




