Massive Leak Exposes 273,000 Indian Bank Transfer Records Online
Data Breach Exposes 2.73 Lakh Bank Records
An unsecured cloud server exposed hundreds of thousands of bank transfer records, revealing names, bank account details, and contact information. Cybersecurity firm UpGuard discovered over 2.73 lakh files on the Amazon server on August 26, each showing unmasked account numbers, transaction amounts, and personal contact details.

Image courtesy of The Economic Times
The exposed data included sensitive information from 38 banks and non-bank lenders. Notably, over half the records were attributed to IPO-bound non-banking finance company Aye Finance (59.63%). Other affected lenders included State Bank of India (24.22%) and Muthoot Capital (13.31%).
The data was formatted according to the requirements of the National Automated Clearing House (NACH), a service created by the National Payments Corporation of India (NPCI) to streamline electronic transactions. NPCI confirmed that the leak did not originate from their systems.
Timeline of Events
- August 26: UpGuard discovered the publicly accessible Amazon S3 cloud storage bucket containing approximately 273,000 PDF documents.
- August 27: Notifications sent to Aye Finance regarding the breach.
- August 29: UpGuard escalated the issue to NPCI.
- September 4: The exposed bucket was secured after UpGuard notified CERT-In, the government’s cyber incident response team.
Data Statistics
- Total files: 273,160
- Size of data: 210GB
- Sample size analyzed: 55,000 files
- Affected banks: 38
- Average new files added daily: ~3,000
Researchers found that the transaction forms contained critical financial data, including transaction dates and bank account numbers, with many also displaying individuals' names, phone numbers, and email addresses.
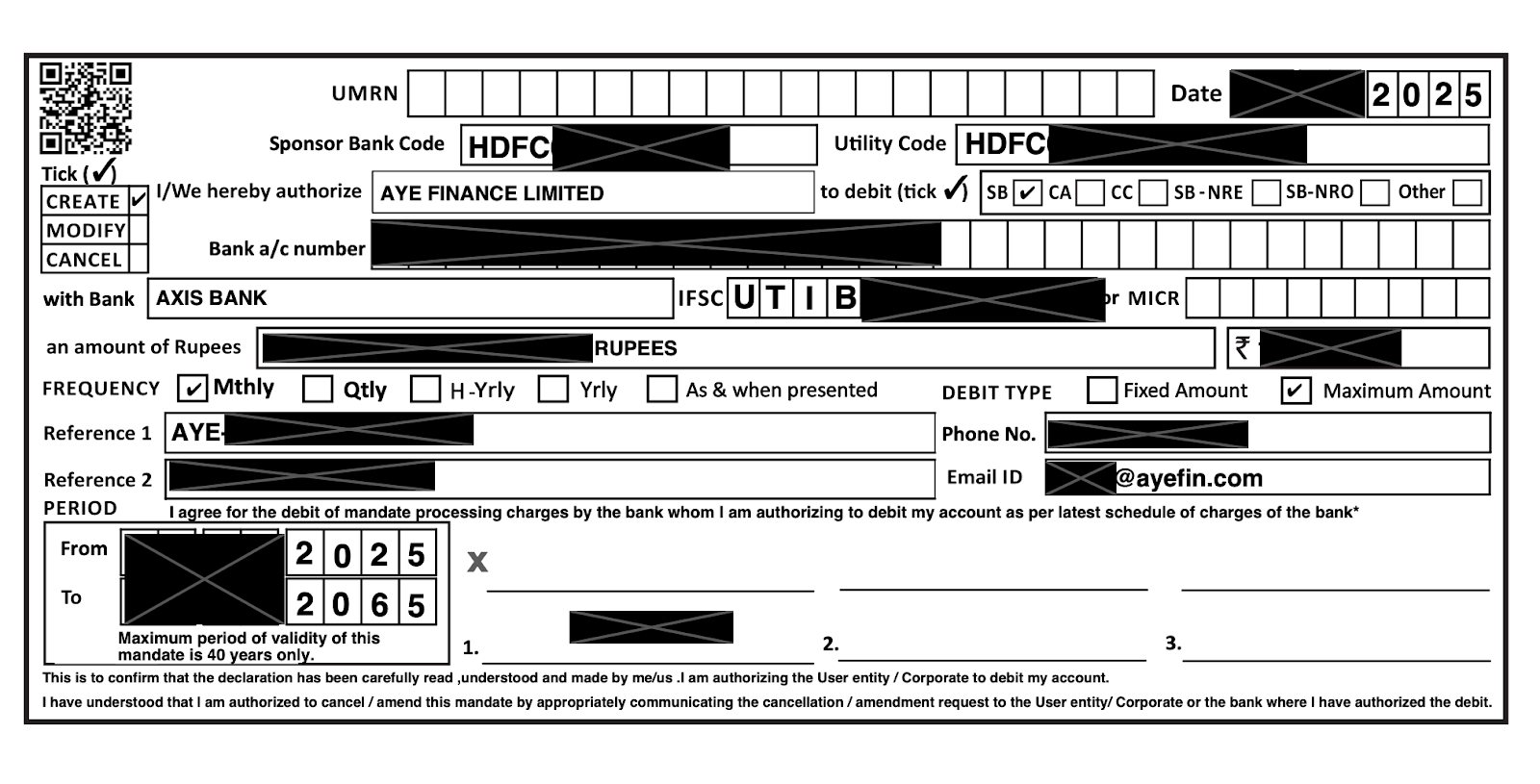
Image courtesy of UpGuard
Affected Organizations
Among the banks, Aye Finance was the most frequently mentioned institution, appearing in nearly 60% of the documents sampled. Despite this, it is dwarfed by larger banks such as the State Bank of India and Punjab National Bank.
| Bank | Mentions | Percentage |
|---|---|---|
| Aye Finance | 32,798 | 59.63% |
| State Bank of India | 13,319 | 24.22% |
| Muthoot Capital | 7,320 | 13.31% |
| Bank of Baroda | 6,124 | 11.13% |
| Punjab National Bank | 5,831 | 10.60% |
NPCI confirmed that all documents were related to NACH transactions, indicating that the source of the leak was not linked to their systems.
Misconfiguration and Security Response
Nupay, a fintech company, took responsibility for the data exposure, attributing it to a configuration error in an Amazon S3 storage bucket. The company stated that the bucket contained a limited set of records, with many being dummy or test files. However, UpGuard disputed this claim, asserting that a significant portion of the documents contained sensitive information.
UpGuard's analysis indicated that the risk of fraud was heightened due to the exposure of bank account numbers and transaction details, emphasizing the need for stringent data security measures across all institutions involved in NACH.

Image courtesy of UpGuard
Implications of the Data Leak
The exposed data poses significant risks, including potential for fraud and identity theft. The nature of the NACH system, which aggregates data from multiple institutions, amplifies the impact of such breaches. As UpGuard noted, the configuration issue could have occurred at any point in the chain involving NPCI, banks, and other integration partners.
In a rapidly evolving digital landscape, organizations must prioritize robust data security protocols to prevent similar incidents in the future.





