Microsegmentation and Zero Trust: Enhancing Cyber Resilience
TL;DR
Reducing Risk: Microsegmentation and Cyber Insurance
Microsegmentation's Impact on Incident Response
Organizations implementing microsegmentation have reported significant reductions in ransomware containment times. According to Akamai Technologies, ransomware containment time was reduced by 33% among security organizations with over $1 billion in annual revenue that adopted microsegmentation. This rapid incident response is crucial as 79% of organizations experienced at least one ransomware attack in the past 24 months. The key drivers for adopting microsegmentation include the need for faster incident responses (56%) and the desire to contain ransomware attacks (63%). For more details, refer to the Segmentation Impact Study.
.png)
Cyber insurance is becoming increasingly important as organizations face rising threats. Seventy-five percent of organizations report that insurers now assess segmentation posture during underwriting. Microsegmentation leads to lower insurance premiums, faster claims processing, and improved audit readiness. As organizations adopt microsegmentation, they can simplify their audit reporting, with 85% finding it easier, which helps reduce costs associated with attestation and assurance. More information about this can be found in the full report.
Challenges in Microsegmentation Adoption
Despite the benefits, organizations face several challenges in adopting microsegmentation. The most common hurdles include network complexity (44%), visibility gaps (39%), and operational resistance (32%). Organizations that have successfully implemented microsegmentation report fewer compromised systems, lower recovery costs, and stronger business continuity. For strategies addressing these challenges, visit the Akamai blog.
Ransomware Prevention Through Microsegmentation
The healthcare sector is particularly vulnerable to ransomware attacks, with 67% of healthcare organizations reporting such incidents in 2024. Traditional perimeter-based security models have proven inadequate against these evolving threats. Microsegmentation offers a solution by isolating critical assets and preventing lateral movement, crucial in environments with numerous connected medical devices.
Organizations adopting microsegmentation can achieve a 90% reduction in potential breach impact and contain ransomware within minutes rather than months. This contrasts sharply with traditional security methods that often leave devices unprotected. For more on this topic, see the 2025 Guide to Zero Trust Network Defense.
Zero Trust Architecture and Cyber Resilience
Zero Trust Architecture reinforces microsegmentation by enforcing the principle of "never trust, always verify." This approach enhances visibility and control, helping organizations adapt to the evolving threat landscape. Continuous verification and adaptive security postures enable firms to respond dynamically to emerging risks.
The integration of microsegmentation with Zero Trust strategies limits the attack surface and enhances operational resilience. Organizations can implement strict access controls between segments, thereby improving automated security policy enforcement. For more insights on this, check out the Zero Trust Architecture Playbook.
Cyber Insurance and Risk Management
As cyber insurance markets tighten, organizations must prove their resilience against cyber threats. Insurers are increasingly looking for evidence of active risk management. Illumio emphasizes that organizations can lower their insurance risk by implementing segmentation and AI-powered observability. This helps meet the expectations of modern cyber insurance policies.
Through Illumio Segmentation, organizations limit lateral movement and reduce the attack surface, which is crucial when responding to cyber incidents. Illumio Insights offers real-time visibility and allows companies to prove their security posture to insurers, auditors, and stakeholders. For a free trial, visit Illumio Insights.
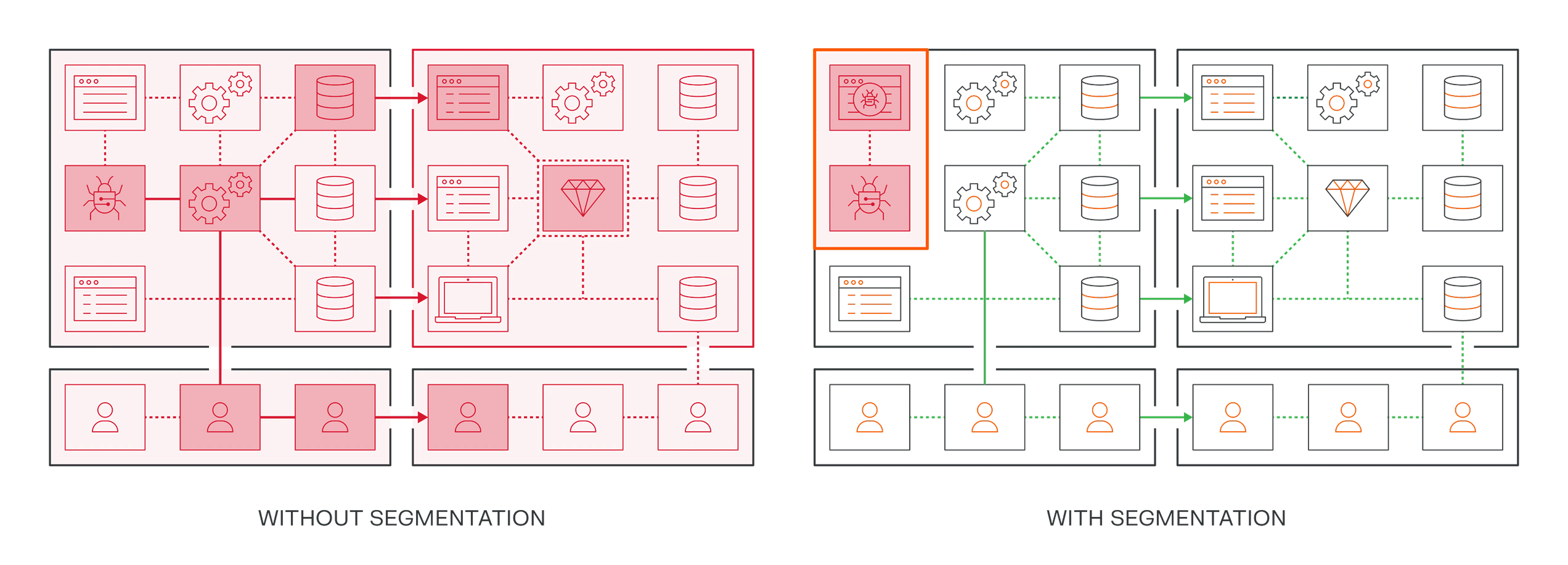
Conclusion
The combination of microsegmentation and a Zero Trust framework significantly enhances an organization's resilience against cyber threats, streamlining compliance with regulatory requirements and improving incident response. By adopting these strategies, organizations can navigate the evolving landscape of cyber insurance and risk management effectively.





