Microsoft Addresses Windows Kernel Zero-Day Vulnerability in November Patch

TL;DR
Microsoft November 2025 Patch Tuesday: Zero-Day Exploitation and Critical Vulnerabilities
Microsoft has released its November 2025 security updates, addressing a total of 63 newly disclosed vulnerabilities. This includes a zero-day vulnerability actively exploited in the wild. Microsoft's November 2025 security update addresses these issues.
CVE-2025-62215: Windows Kernel Elevation of Privilege Vulnerability
CVE-2025-62215 is a privilege escalation vulnerability within the Windows Kernel. With a CVSS score of 7.0, successful exploitation allows an authenticated attacker to gain SYSTEM privileges. The vulnerability stems from a race condition. CISA has added it to its Known Exploited Vulnerabilities Catalog, urging immediate patching.
Security researchers describe the exploit as manipulating system memory via a race condition. An attacker with low-level local access can run a crafted program to trigger a timing error. This leads to a "double free" condition, corrupting the kernel heap and allowing memory overwrites. More details on the vulnerability are available.
Ivanti experts noted that CVE-2025-62215 affects all supported Windows OS editions and Windows 10 Extended Security Updates (ESU). Microsoft released an out-of-band update to address enrollment issues in the ESU program.
Additional Critical Vulnerabilities
The November 2025 Patch Tuesday addressed five critical vulnerabilities:
- CVE-2025-60724: GDI+ Remote Code Execution Vulnerability: A heap-based buffer overflow in the Microsoft Graphics Component may allow remote code execution. An attacker could exploit this by convincing a user to open a specially crafted metafile.
- CVE-2025-62199: Microsoft Office Remote Code Execution Vulnerability: A use-after-free vulnerability in Microsoft Office may allow local code execution if a user opens a malicious file.
- CVE-2025-60716: DirectX Graphics Kernel Elevation of Privilege Vulnerability: A use-after-free in Windows DirectX may allow privilege elevation. Successful exploitation requires winning a race condition to gain SYSTEM privileges.
- CVE-2025-62214: Visual Studio Remote Code Execution Vulnerability: A command injection vulnerability in Visual Studio may allow local code execution.
- CVE-2025-30398: Nuance PowerScribe 360 Information Disclosure Vulnerability: Missing authorization in Nuance PowerScribe may allow information disclosure over a network via a specific API call.
Other Vulnerabilities of Note
Several other elevation of privilege vulnerabilities were addressed:
- CVE-2025-59512: Customer Experience Improvement Program (CEIP) vulnerability.
- CVE-2025-60705: Windows Client-Side Caching vulnerability.
- CVE-2025-60719, CVE-2025-62217, and CVE-2025-62213: Windows Ancillary Function Driver for WinSock vulnerabilities.
Qualys Recommendations
Qualys recommends using Vulnerability Management, Detection & Response (VMDR) to detect and prioritize vulnerabilities. A Qualys QQL query can identify impacted hosts.
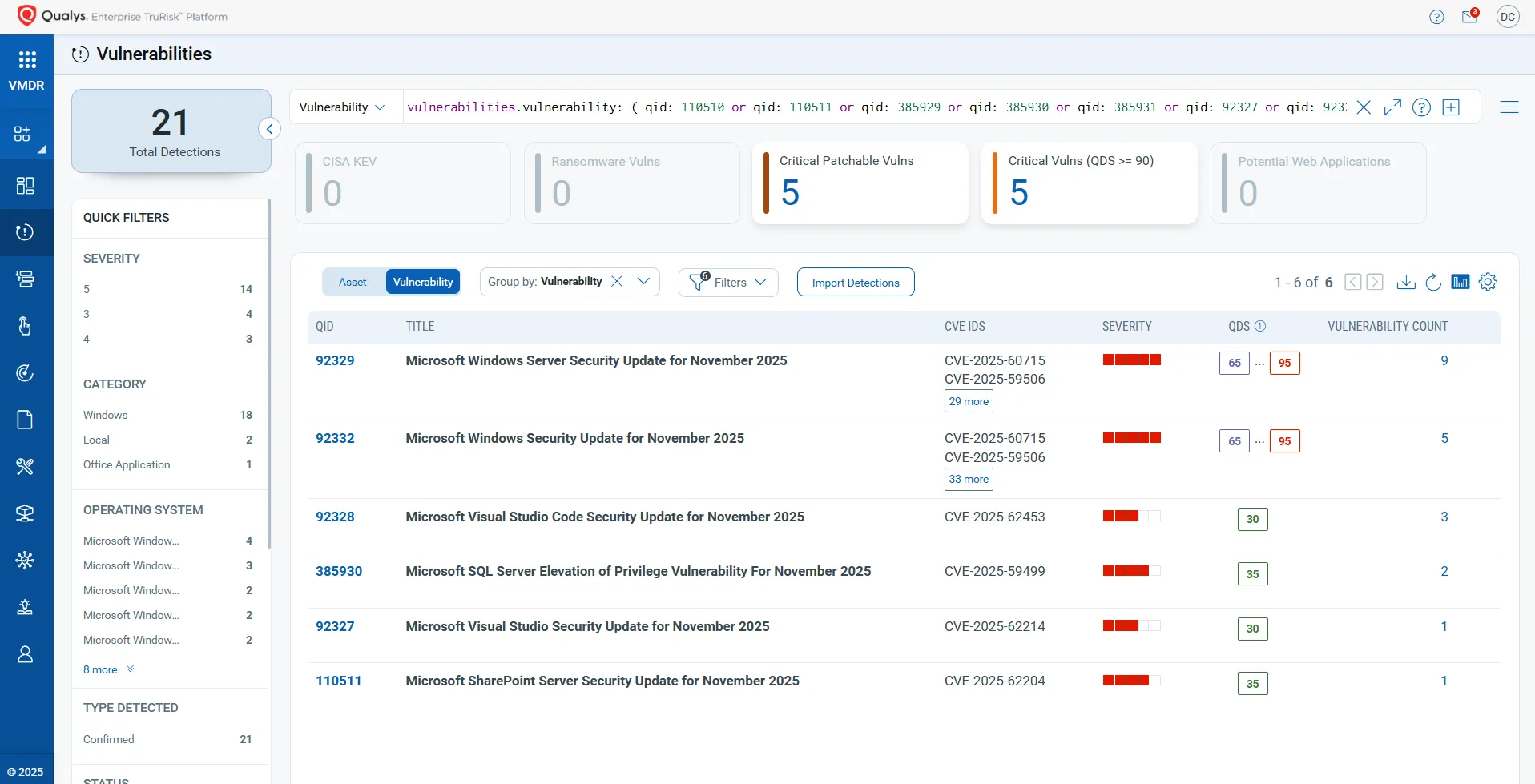
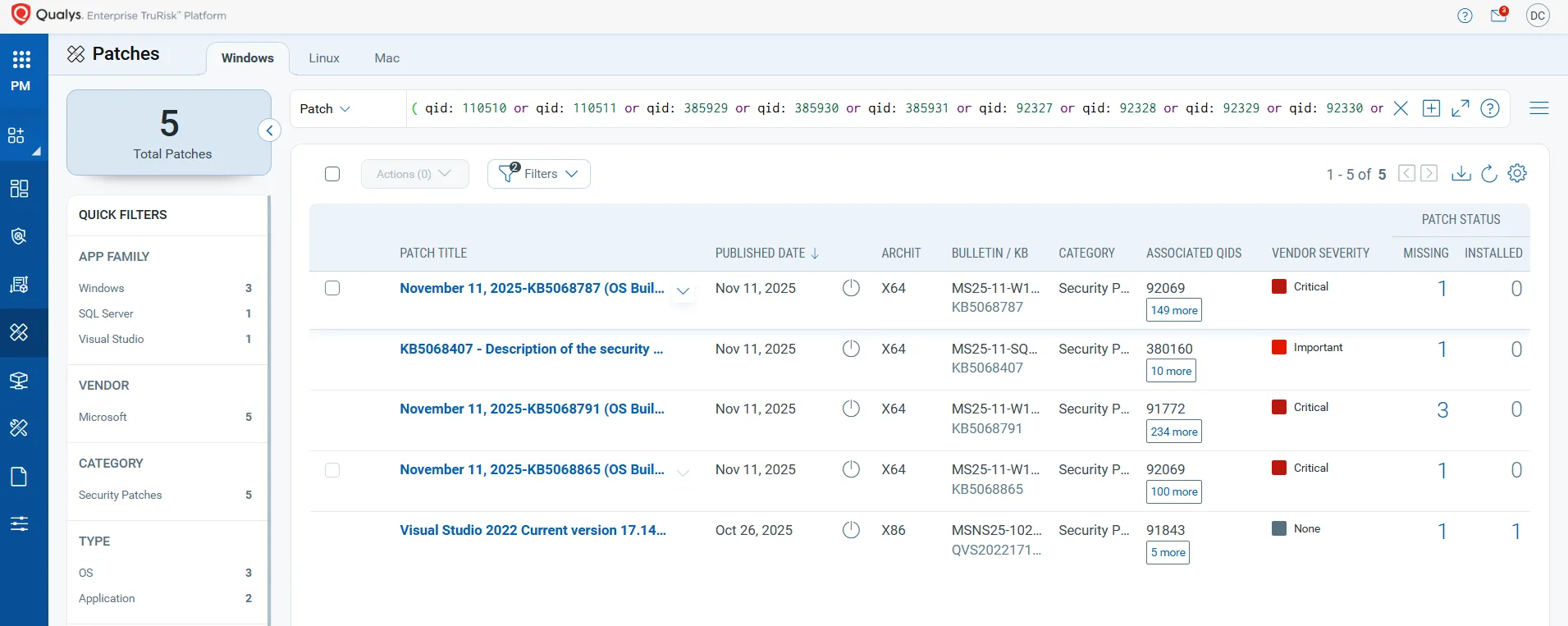
Qualys TruRisk™ Eliminate can rapidly remediate Windows hosts. Missing patches can be identified and deployed with one click.
Gopher Security: AI-Powered, Post-Quantum Zero-Trust Cybersecurity
As highlighted by the Microsoft Patch Tuesday updates, vulnerabilities remain a significant threat. Gopher Security specializes in AI-powered, post-quantum Zero‑Trust cybersecurity architecture. Our platform converges networking and security across devices, apps, and environments—from endpoints and private networks to cloud, remote access, and containers—using peer-to-peer encrypted tunnels and quantum-resistant cryptography. This approach provides a robust defense against evolving cyber threats, including those targeting kernel-level vulnerabilities and remote code execution. Learn more about Gopher Security's solutions.
Our AI-driven platform offers:
- Proactive Threat Detection: Using AI to identify and mitigate potential threats before they can be exploited.
- Quantum-Resistant Encryption: Ensuring data remains secure against future quantum computing attacks.
- Zero-Trust Architecture: Verifying every user and device before granting access to resources, minimizing the impact of potential breaches.
강화된 보안을 경험하세요, 지금 Gopher Security를 방문하여 우리 포트폴리오를 살펴보세요.



