Phantom Taurus: New Chinese APT Targets Governments with Malware
Phantom Taurus Overview
Phantom Taurus is a newly identified Chinese advanced persistent threat (APT) group that has been operational for over two and a half years, primarily targeting government and telecommunications organizations across Africa, the Middle East, and Asia. The group's espionage operations align closely with the strategic interests of the People's Republic of China (PRC).
The primary focus areas of Phantom Taurus include ministries of foreign affairs, embassies, and military operations. According to researcher Lior Rochberger, "The group's primary objective is espionage. Its attacks demonstrate stealth, persistence, and an ability to quickly adapt their tactics, techniques, and procedures (TTPs)" source.
Evolution of Phantom Taurus
Palo Alto Networks first tracked Phantom Taurus as activity cluster CL-STA-0043 in June 2023. By May 2024, it was designated TGR-STA-0043 and given the campaign codename Operation Diplomatic Specter. Recent investigations have revealed sufficient evidence to classify the group as an independent threat actor focused on long-term intelligence collection source.

The group's operations often coincide with major geopolitical events, and the timing and scope of their attacks reflect their alignment with PRC's economic and political interests.
Technical Analysis and Tactics
Targeting and Attack Techniques
Phantom Taurus primarily conducts long-term intelligence operations against high-value targets to acquire sensitive, non-public data. The group's shift from exfiltrating emails to directly targeting SQL Server databases marks a significant tactical evolution. Utilizing a batch script named mssq.bat, the group connects to databases, executes queries, and exports results to CSV files source.
The mssq.bat script operates as follows:
- Authenticates to the SQL Server using the system administrator account.
- Dynamically executes queries to search for specific keywords.
- Exports the results to CSV files before closing the connection.
This approach demonstrates the group’s reliance on living-off-the-land (LotL) techniques to evade detection.
Custom Malware: NET-STAR
One of the most alarming developments is the introduction of a bespoke malware suite named NET-STAR, which targets Internet Information Services (IIS) web servers. This .NET malware suite is designed for stealthy operations and advanced evasion techniques source.
NET-STAR includes three main components:
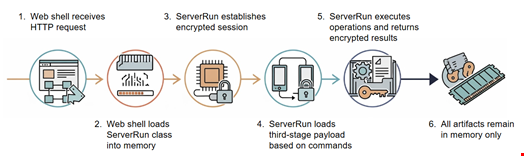
- IIServerCore: A fileless modular backdoor that operates in memory, allowing execution of commands and payloads without leaving traces on disk.
- AssemblyExecuter V1: A version that loads and executes other .NET assemblies directly in memory.
- AssemblyExecuter V2: An enhanced variant that includes capabilities to bypass Antimalware Scan Interface (AMSI) and Event Tracing for Windows (ETW) source.
!IIServerCore Execution Flow
Conclusion on Threat Landscape
Phantom Taurus represents a significant threat to organizations across various sectors due to its advanced capabilities and clear alignment with state-sponsored espionage activities. The combination of targeted tactics, bespoke malware, and operational compartmentalization makes this group a formidable adversary in the cyber threat landscape.
For further information on Phantom Taurus and its tactics, check out the following links:
- Unit 42 Report on Phantom Taurus
- Phantom Taurus: New China-Linked Hacker Group
- APT Groups and Threat Actors | Google Cloud





