Police Dismantle DiskStation Ransomware Targeting NAS Devices
Police disrupt “Diskstation” ransomware gang attacking NAS devices

An international law enforcement operation dismantled a Romanian ransomware gang known as 'Diskstation,' which encrypted the systems of several companies in the Lombardy region, paralyzing their businesses. The operation, codenamed 'Operation Elicius,' was coordinated by Europol and involved police forces in France and Romania.
Diskstation is a ransomware operation targeting Synology Network-Attached Storage (NAS) devices, commonly used by companies for centralized file storage, data backup, and content hosting. Since 2021, this gang has used various names, including "DiskStation Security" and "Quick Security." Their attacks primarily targeted internet-exposed NAS devices, encrypting files and demanding ransom payments ranging from $10,000 to hundreds of thousands of dollars.
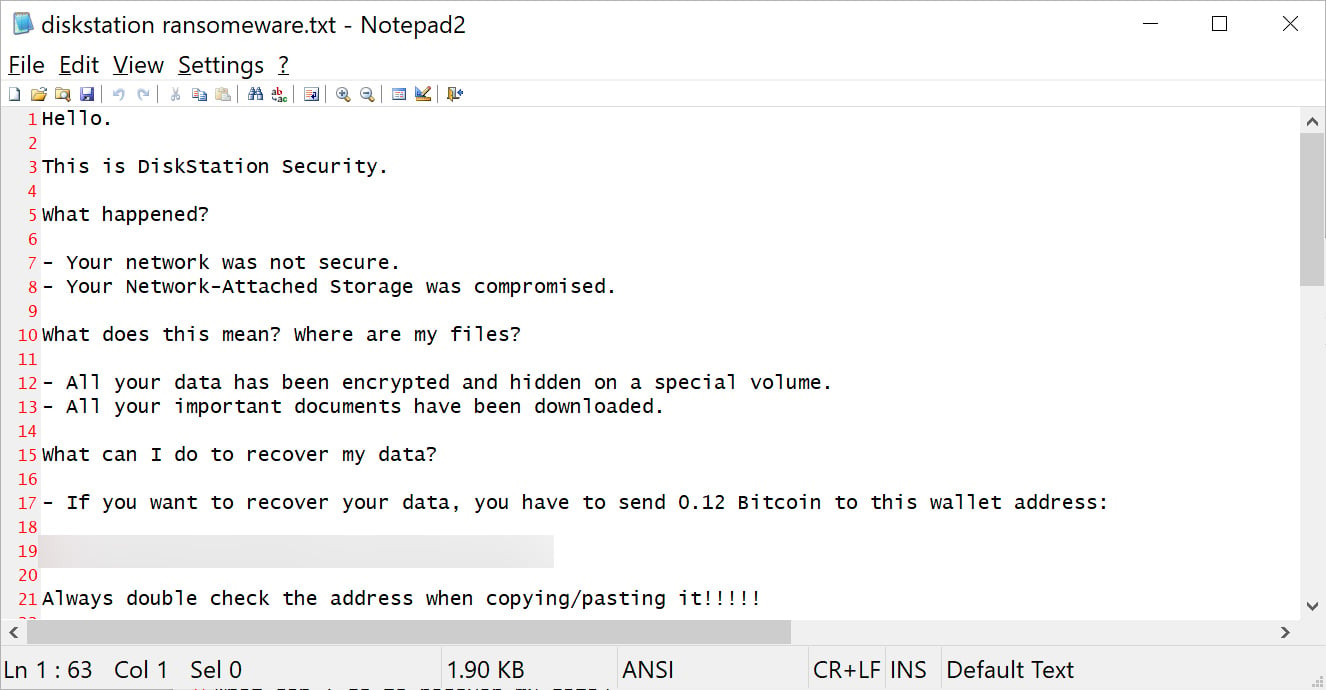
An announcement from the Postal and Cybersecurity Police Service indicated that the victims faced severe operational disruptions due to data encryption. "These companies had experienced encryption of data on their IT systems, resulting in the complete 'paralysis' of their production processes," reads the announcement. To regain access, victims were required to pay substantial ransoms in cryptocurrency.
The investigation, led by the Milan Prosecutor's Office, involved forensic analysis of compromised systems and blockchain analysis to trace ransom payments. Within months, investigators identified several suspects, leading to raids in Bucharest in June 2024, resulting in arrests, including a 44-year-old Romanian man suspected of being the primary operator behind the attacks.
To protect NAS devices from unauthorized access or ransomware attacks, ensure they run the latest available firmware, disable unnecessary services, do not expose them to the internet, and restrict access to VPNs.
Authorities Dismantled “Diskstation” Ransomware Attacking Synology NAS Devices Worldwide

The Italian State Police, in collaboration with French and Romanian law enforcement, dismantled the Diskstation ransomware group targeting Synology NAS devices globally. The operation resulted in multiple arrests and exposed a sophisticated cybercriminal network that encrypted systems and demanded cryptocurrency for data recovery.
The investigation initiated after complaints from Lombardy-based companies whose IT infrastructures were compromised. The criminals employed advanced encryption algorithms, rendering critical data inaccessible and paralyzing production across various sectors, including graphic design and film production.
The Cybersecurity Operations Center in Milan conducted comprehensive forensic analysis of attacked systems and performed detailed blockchain analysis to trace cryptocurrency transactions. This dual approach was crucial in identifying attack vectors and establishing the operational structure of the criminal network.
The ransomware group exhibited expertise in exploiting vulnerabilities within Synology NAS devices, leveraging zero-day exploits and credential stuffing techniques for unauthorized access before deploying encryption payloads.
Ransomware Ring Shut Down
The complexity of the cybercriminal operation necessitated expanded international cooperation, leading to a specialized task force coordinated by Europol. The collaborative effort included cyber crime units from Italy, France, and Romania, contributing expertise in digital forensics and cross-border legal procedures.
During searches in Bucharest in June 2024, investigators from the Milan COSC, alongside Romanian authorities, apprehended several suspects committing cybercrime. The operation yielded substantial digital evidence confirming the investigative hypotheses.
The primary suspect, a 44-year-old Romanian citizen, has been placed in pre-trial detention facing charges of “Unauthorized Access to a Computer or Telematic System” and “Extortion.” These charges reflect the serious nature of the crimes affecting numerous victims.
Synology has been advising users on how to protect their NAS devices from ransomware attacks for years. Recommendations include minimizing internet exposure, hardening password security, and ensuring regular backups.
To further enhance security, users should enable two-step verification (2FA) and disable or rename default “admin” accounts. Disabling remote services like QuickConnect, WebDAV, and SSH can also mitigate risks, while utilizing Synology’s firewall to restrict access is advisable. Keeping NAS devices updated with the latest security patches is essential for ongoing protection.
For more information on securing NAS devices from ransomware, visit Synology's website.



