Preventing ClickFix Attacks: Safeguarding Against Human Error
ClickFix Technique Overview
ClickFix is an emerging social engineering technique utilized by threat actors to exploit human error. This technique involves misleading users into executing malicious commands under the guise of providing "quick fixes" for common computer issues. Threat actors use familiar platforms and deceptive prompts to encourage victims to paste and run harmful scripts.

Impacted Industries
ClickFix campaigns have targeted a wide range of industries, including healthcare, finance, government, and manufacturing, posing significant security threats. Such campaigns exploit the reputation of legitimate services to hide malicious activities, making detection challenging.
For more information on the impact of ClickFix, visit:
- Threat Actors Exploit ClickFix to Deploy NetSupport RAT
- Hackers Leverage New ClickFix Tactic to Exploit Human Error
ClickFix Campaign Techniques
Initial Access
Attackers often gain entry through phishing links or compromised websites. They use fake CAPTCHA prompts that redirect users to malicious URLs, instructing them to execute harmful PowerShell commands.
Delivery Methods
Clipboard Hijacking: Attackers inject malicious scripts into the victim's clipboard, prompting them to paste and run these commands, often via the Windows Run dialog.
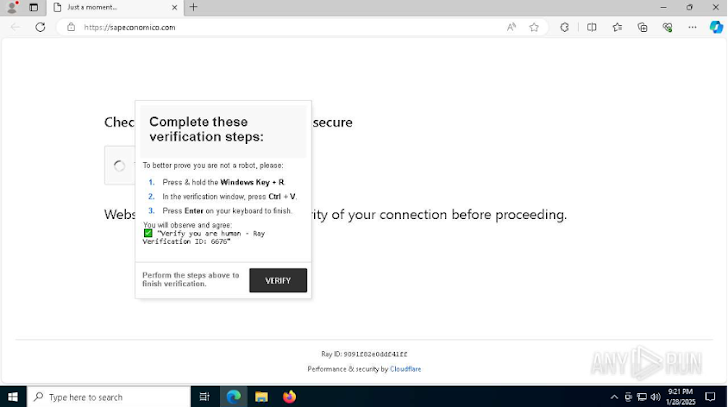
Fake Verification Pages: These pages ask users to verify their identity by running specific commands, which allows malware to be executed.
For detailed strategies, refer to:
- Fix the Click: Preventing the ClickFix Attack Vector
- Threat Actors Exploit ClickFix to Deploy NetSupport RAT
Case Studies of ClickFix Campaigns
NetSupport RAT
One prominent campaign involved the distribution of NetSupport RAT, which allows attackers to gain full control of a victim's device. This campaign used fake verification pages, disguising malicious PowerShell commands as legitimate actions.
Lumma Stealer
The Lumma Stealer campaign also utilized ClickFix, with attackers directing victims to execute encoded PowerShell commands that ultimately led to the theft of sensitive information. This malware is known for targeting cryptocurrency wallets and two-factor authentication extensions.
More details can be found at:
Detection and Prevention Strategies
Monitoring RunMRU Artifacts
Security analysts can detect ClickFix activity by reviewing the Windows registry key for recently executed commands (RunMRU). Indicators of compromise include obfuscated commands or suspicious domain references.
EDR Telemetry and Event Logs
Using endpoint detection and response (EDR) telemetry, analysts should look for abnormal PowerShell executions related to the Win + X command. This method is commonly used by attackers to bypass detection.
For more on detection strategies, see:
- Fix the Click: Preventing the ClickFix Attack Vector
- Hackers Leverage New ClickFix Tactic
Gopher Security Solutions
Gopher Security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture that converges networking and security across devices, applications, and environments. Our platform uses peer-to-peer encrypted tunnels and quantum-resistant cryptography to protect organizations against evolving threats like ClickFix.
Explore our services or contact us at Gopher Security for advanced cybersecurity solutions tailored to your needs.



