Ransomware Threats Rise: Challenges in Modeling Systemic Events
Ransomware Dominance and Cyber Risk Insights

Image courtesy of Reinsurance Business
Cyber risk analytics firm CyberCube and global reinsurer Munich Re report significant findings regarding ransomware and systemic cyber events. A joint study reveals that a major malware event could impact 25% of global systems, with a complete compromise expected in approximately 15% of cases. Notably, no scenario was foreseen where over 50% of global systems would be fully compromised. Effective defenses such as patch management, network segmentation, and comprehensive data backup can reduce risks by 50% to 80%.
The study also highlights cloud service risks, indicating that outages across major providers could last from a few hours to several days. The impact of outages varies based on financial exposure, with a one-day disruption costing about 1% of annual revenue, contingent on the organization's cloud reliance and sector.
Ransomware Trends and Resilience
Ransomware attacks have increased by 3% in 2024 compared to 2023, underscoring the resilience of this cyber threat. Noteworthy operations like LockBit and Noberus faced disruptions, but activity rebounded later in the year. Tactics employed by ransomware actors have shifted towards using dual-use tools for data exfiltration and disabling security software.
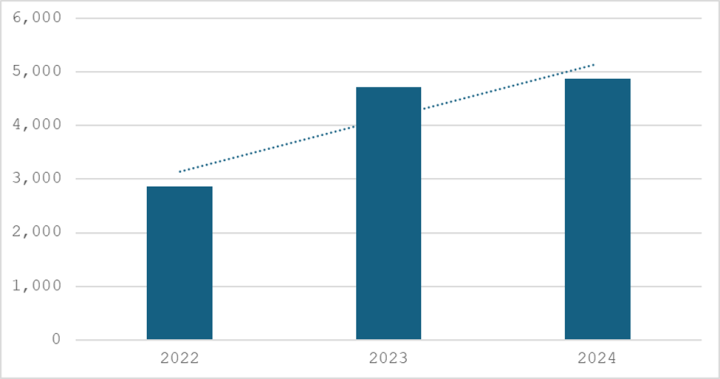
The emergence of RansomHub, a ransomware-as-a-service (RaaS) operation, has marked a significant trend in 2024, replacing declining operations like LockBit. RansomHub offers generous affiliate terms, attracting numerous partners. Attackers often exploit known vulnerabilities such as Zerologon (CVE-2020-1472) and CitrixBleed (CVE-2023-3519) to gain initial network access.
Tactics and Tools Used by Ransomware Actors
Ransomware actors increasingly rely on living-off-the-land techniques, utilizing legitimate software in their attacks. Common tools include PowerShell, RDP, and Rclone, with remote access software like AnyDesk and Atera being frequently exploited.

Disabling security software has become a key tactic, often achieved through the Bring Your Own Vulnerable Driver (BYOVD) method, where attackers exploit signed vulnerable drivers to terminate security processes. Tools like TrueSightKiller and Gmer are frequently utilized in these efforts.
Future Outlook on Ransomware Threats
The ransomware landscape is expected to continue evolving, with attackers adapting to evade detection and law enforcement pressures. Companies must remain vigilant, leveraging proper mitigation strategies to protect against ransomware threats. Effective measures include regular patch management, network segmentation, and utilizing comprehensive cloud services.
For organizations looking to bolster their defenses against evolving cyber threats, exploring the services offered by Gopher Security , can be a crucial step toward enhanced security. Visit Gopher Security for more information or to contact us for support in fortifying your cybersecurity posture.




