Russia-Linked Malware Targets Email Accounts for Espionage
Russia Linked to New Malware Targeting Email Accounts for Espionage
Russian military intelligence (GRU)-linked hackers are employing a new malware called “Authentic Antics” to target Microsoft cloud email accounts, according to the UK’s National Cyber Security Centre (NCSC). This malware is designed for persistent endpoint access by mimicking legitimate Microsoft Outlook activity.
The malware prompts users with a login window, capturing credentials and OAuth authentication tokens. Moreover, it exfiltrates data by sending emails from the victim’s account to a controlled email address, leaving no trace in the “sent” folder. Notably, there is no traditional command-and-control structure, reducing detection likelihood.
Paul Chichester, NCSC Director of Operations, remarked, “The use of Authentic Antics malware demonstrates the persistence and sophistication of the cyber threat posed by Russia’s GRU.” The malware was revealed following an incident investigated by Microsoft and NCC Group.
For further details, read more about APT28's activities and the UK's sanctions against Russian GRU officers.
Google Links New LostKeys Data Theft Malware to Russian Cyberspies
The ColdRiver hacking group, backed by the Russian state, has been using a new malware, LostKeys, for espionage targeting Western governments and organizations. This malware was first observed by Google Threat Intelligence Group in January as part of social engineering attacks known as ClickFix, which mislead victims into executing harmful PowerShell scripts.
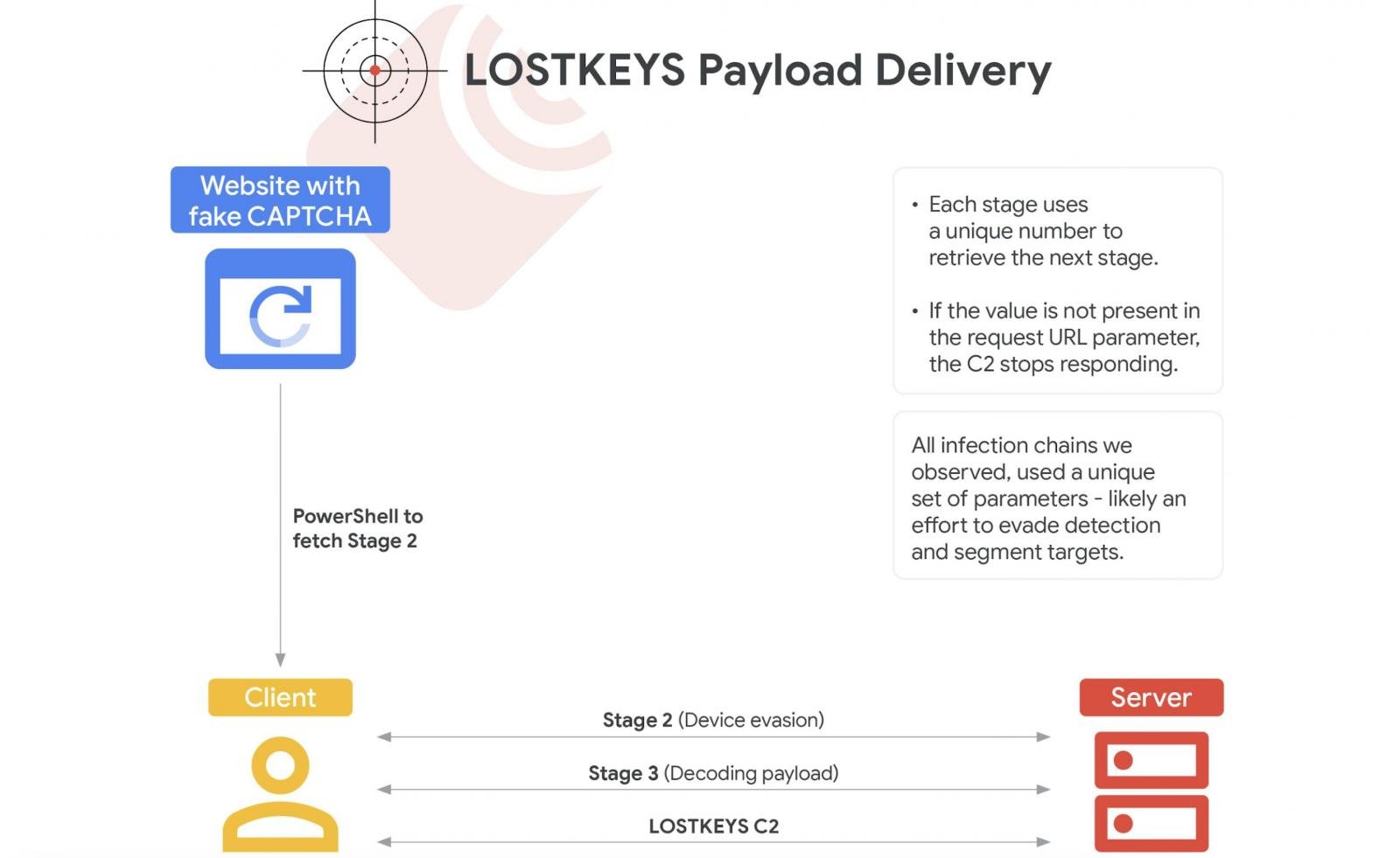
LostKeys is capable of stealing files from predefined extensions and directories, sending system information to attackers, and executing processes. ColdRiver has also been linked to prior campaigns against NATO and U.S. facilities. In December 2023, the U.S. State Department sanctioned two ColdRiver operators, highlighting the ongoing threat posed by state-sponsored cyber activity.
Read more about ColdRiver's tactics and the U.S. sanctions on Russian hackers.
UK Sanctions Russian Intelligence Officers Linked to Mariupol Theater Bombing
The UK has imposed sanctions on 18 GRU officers and three military intelligence units for their involvement in a 2022 bombing that resulted in civilian casualties in Ukraine. The Foreign, Commonwealth and Development Office highlighted that these units have been linked to various destabilization activities across Europe.

The GRU's cyber operations include accessing CCTV cameras and conducting online reconnaissance on civilian locations. U.K. Foreign Secretary David Lammy stated, “GRU spies are running a campaign to destabilize Europe.” The sanctions aim to raise awareness about Russia’s ongoing cyber threat and to impose consequences on individuals associated with its intelligence services.
Learn more about the Mariupol theater bombing investigation.
New “LameHug” Malware Deploys AI-Generated Commands
CERT-UA has identified a new malware, "LameHug," that utilizes AI-generated commands to target Windows systems in Ukraine. This malware is believed to be linked to APT28 and has been disseminated through emails masquerading as official communications from government entities.
LameHug leverages the Hugging Face API along with an open-source AI model to generate execution commands, making it adaptable and potentially harder to detect. The malware is designed to execute commands without needing new payloads, which poses a severe security risk.
APT28 has a history of targeting Ukraine since at least 2004, and its operations have included cyber-attacks against critical infrastructure. For more insights into APT28's activities, read about APT28’s cyber-espionage campaigns.
Gopher Security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture. Our platform converges networking and security across various environments, employing advanced technologies like peer-to-peer encrypted tunnels and quantum-resistant cryptography. Explore our services or contact us at Gopher Security here.



