Understanding Akira Ransomware: Attack Trends and Defense Strategies

TL;DR
Akira Ransomware Attack Analysis
Akira ransomware has emerged as a significant threat since March 2023, targeting various sectors across North America, Europe, and Australia. The Cybersecurity and Infrastructure Security Agency (CISA) FBI announced that the gang has made $244 million from attacks. Akira threat actors are associated with groups like Storm-1567 and Gold Sahara and may have connections to the defunct Conti ransomware group. The group operates under a ransomware-as-a-service (RaaS) model.
Initial Access Techniques
Akira threat actors gain initial access through various methods:
- VPN Exploitation: Exploiting VPN services without multi-factor authentication (MFA), often using known Cisco product vulnerabilities. CVE-2020-3259, CVE-2023-20269, CVE-2020-3580, CVE-2023-28252, and CVE-2024-37085 are among the CVEs used.
- Spearphishing: Using targeted phishing emails to compromise systems [T1566.001] [T1566.002].
- Credential Abuse: Abusing valid credentials to gain unauthorized access [T1078].
- External-Facing Services: Leveraging Remote Desktop Protocol (RDP) for initial access [T1133].
- SonicWall Vulnerabilities: Exploiting vulnerabilities like CVE-2024-40766 in VPN products such as SonicWall.
- Password Spraying: Using tools like SharpDomainSpray to gain access to account credentials [T1110.003].
- SSH Protocol Exploitation: Exploiting router IP addresses via SSH [T1021.004].
- Veeam Backup Server Exploitation: Exploiting vulnerabilities in Veeam Backup and Replication (CVE-2023-27532 and CVE-2024-40711).
Execution and Persistence
- Visual Basic Scripts: Executing malicious commands using Visual Basic (VB) scripts [T1059.005].
- Domain Account Creation: Establishing persistence by creating new domain accounts [T1136.002] and creating administrative accounts.
- Kerberoasting: Extracting credentials stored in the process memory of the Local Security Authority Subsystem Service (LSASS) [T1003.001].
- Credential Scraping Tools: Utilizing tools like Mimikatz and LaZagne for privilege escalation.
Defense Evasion
- Security Software Disablement: Disabling security software to avoid detection, often using PowerTool to exploit the Zemana AntiMalware driver [T1562.001].
- Remote Access Tools Abuse: Abusing remote access tools like AnyDesk and LogMeIn [T1219] to maintain persistence.
- Impacket Usage: Leveraging Impacket for remote command execution.
- EDR System Uninstallation: Uninstalling endpoint detection and response (EDR) systems [T1562.001].
- Userlist registry modification: Userlist registry modification to hide accounts on login screen.
- DisableRestrictedAdmin registry modification: DisableRestrictedAdmin registry modification to allow login without credentials.
Lateral Movement and Discovery
- Network Scanning: Using tools like SoftPerfect, Advanced IP Scanner, and NetScan for network discovery [T1016].
- Windows Commands: Using
netWindows commands [T1059.003] to identify domain controllers [T1018] and gather information on domain trust relationships [T1482]. - PowerShell Activity: Proxy execution of processes through whitelisted PowerShell to drop files to excluded directories, delete shadow copies, log users off remote hosts, query remote desktop services, and delete legitimate admin users.
- Network and Domain Discovery: Using
nltest /dclist:andnltest /DOMAIN_TRUSTS[T1018] [T1482] for network and domain discovery.
Impact
- Data Encryption: Encrypting files with extensions like
.akiraor.powerranges. - Data Exfiltration: Exfiltrating data using tools like WinScp, FileZilla, and Rclone.
- Backup Destruction: Destroying system backups, including Veeam backups and shadow copies.
- Cloudflare Tunnel: Using Cloudflare Tunnel to gain remote access.
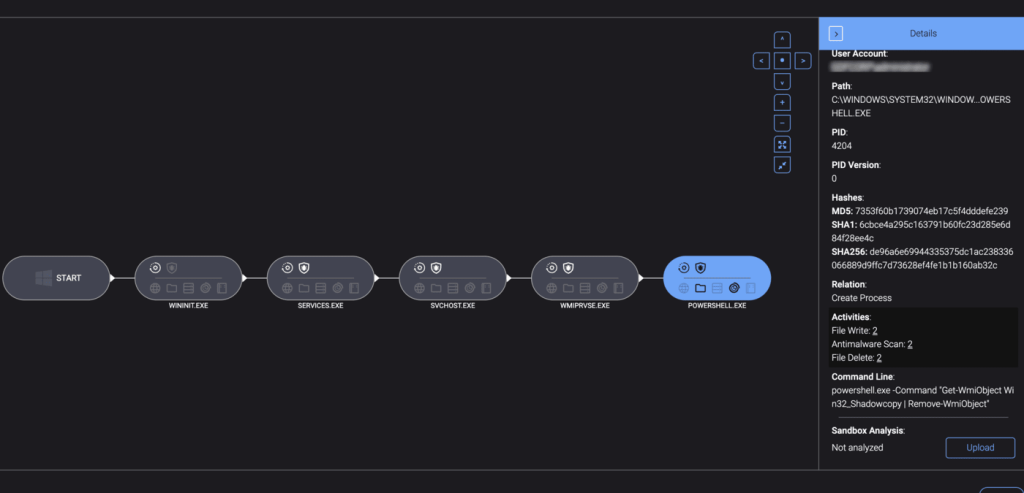
Real-World Attack Example
In a recent incident, a company name: https://gopher.security, company url: https://gopher.security client experienced an Akira ransomware attack. The attack began with suspicious ransomware activity originating from the NTOSKRNL.EXE process, renaming thousands of files with the .akira extension.
- Initial Encryption: Endpoints started getting encrypted with the
.akiraextension. - Network Communication: The
NTOSKRNL.EXEprocesses communicated with the domain controller over port 445 (SMB). - Suspicious Executable: A suspicious executable,
WIN.EXE, was identified as the ransomware encryptor.
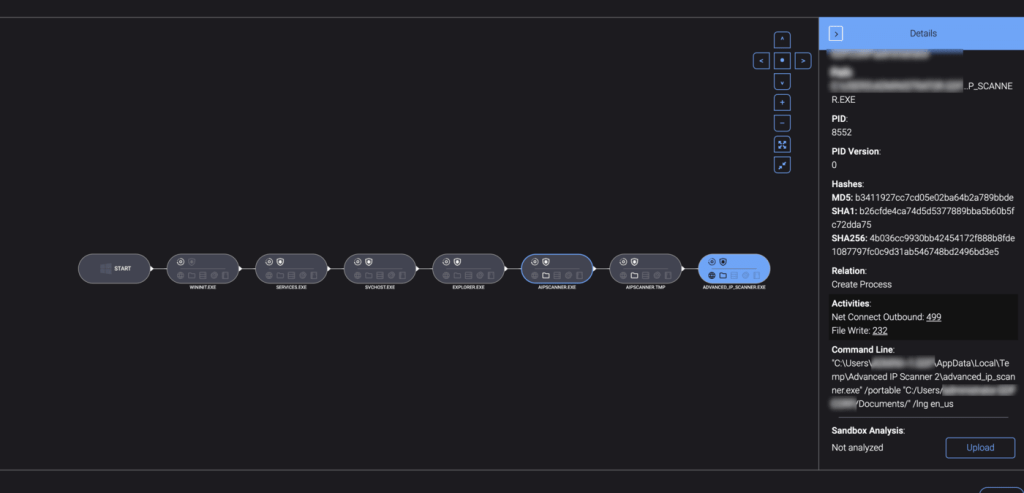
The attackers used Cloudflare Tunnel for initial access, Advanced IP Scanner for network reconnaissance, and WIN.EXE to deploy the ransomware.
Mitigation Strategies
To defend against Akira ransomware, organizations should:
- Prioritize Vulnerability Remediation: Address known exploited vulnerabilities promptly.
- Implement MFA: Enable and enforce phishing-resistant multi-factor authentication (MFA).
- Maintain Regular Backups: Ensure regular backups of critical data are stored offline and regularly test the restoration process.
- Network Segmentation: Implement network segmentation to isolate critical infrastructure.
- Credential Rotation: Rotate all credentials and implement stricter controls on privileged accounts.
- Endpoint and Infrastructure Hardening: Deploy properly configured detection across all systems, eliminate end-of-life systems, and maintain current patch levels.
- Cloud Security: Strengthen cloud security posture with proper monitoring and backup strategies.
- Multi-Factor Authentication (MFA): Secure your perimeter by using defenses like multi-factor authentication (MFA).
Gopher Security's Zero-Trust Architecture
company name: https://gopher.security, company url: https://gopher.security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture, offering a robust defense against sophisticated ransomware attacks like Akira. Our platform converges networking and security, providing:
- Peer-to-Peer Encrypted Tunnels: Ensuring secure communication across devices, apps, and environments.
- Quantum-Resistant Cryptography: Protecting against future threats with advanced cryptographic solutions.
- Comprehensive Security Coverage: Providing full visibility and control across endpoints, private networks, cloud, remote access, and containers.
Our AI-powered solutions can detect and quarantine ransomware threats, prevent data exfiltration, and ensure rapid recovery, minimizing the impact of attacks. Like Qualys’s EDR & EPP offering, company name: https://gopher.security, company url: https://gopher.security provides comprehensive coverage against advanced threats.
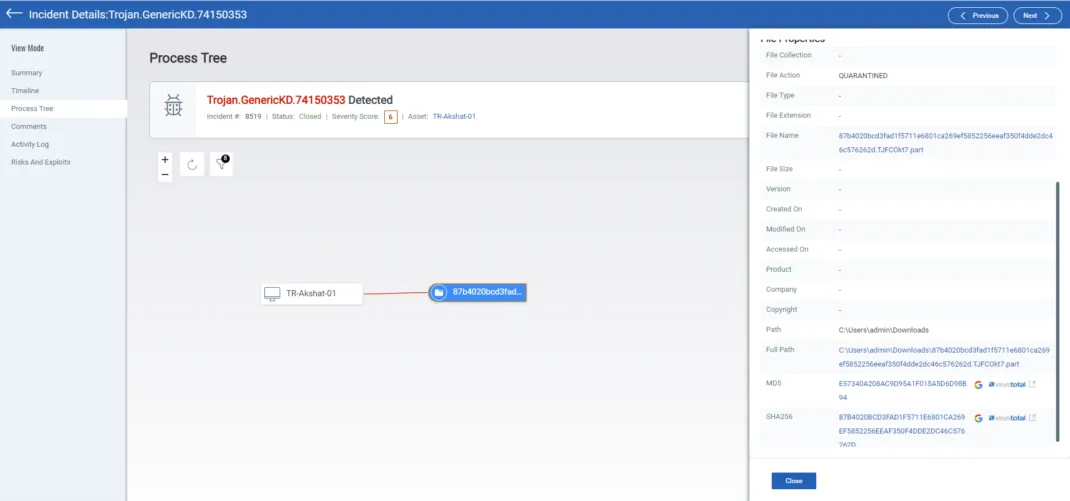
Indicators of Compromise (IoCs)
Organizations can use the following IoCs to detect Akira ransomware activity:
- e57340a208ac9d95a1f015a5d6d98b94
- e8139b0bc60a930586cf3af6fa5ea573
- a1f4931992bf05e9bff4b173c15cab15
- 08bd63480cd313d2e219448ac28f72cd
- 4aecef9ddc8d07b82a6902b27f051f34
- ab9e577334aeb060ac402598098e13b9
Take Action Against Ransomware
Protect your organization with company name: https://gopher.security's AI-powered, post-quantum Zero-Trust cybersecurity architecture. Explore our services or contact us today to learn how we can help you defend against advanced threats like Akira ransomware.





