EY's 4TB SQL Server Backup Exposed Publicly on Azure
TL;DR
EY Data Exposure: 4TB SQL Server Backup Found Publicly Accessible on Azure
Ernst & Young (EY), one of the Big Four accounting firms, inadvertently exposed a 4-terabyte SQL Server backup file on Microsoft Azure. This misconfiguration could have provided attackers with access to sensitive financial records, credentials, and authentication tokens belonging to major corporations. Security researchers from Neo Security discovered the publicly accessible database backup through routine attack surface mapping. The exposure has since been remediated following responsible disclosure protocols.
Discovery and Verification Process
The discovery process began with passive reconnaissance. A Neo Security researcher noticed an unusual HTTP response during routine network traffic analysis. A HEAD request returned metadata indicating a 4-terabyte file accessible from the public internet. The file naming conventions matched SQL Server backup (.BAK) file formats, suggesting a complete database export containing schemas, stored procedures, and potentially sensitive data including API keys, session tokens, user credentials, and authentication tokens.
To verify the file’s authenticity without downloading the entire dataset, researchers examined the file’s header signatures the distinctive “magic bytes” that identify file types. The bytes confirmed an unencrypted SQL Server backup.
The SQL Server BAK file is a complete database backup and contains everything: the schema, all the data, stored procedures, and critically, every secret stored in those tables, including API keys, session tokens, user credentials, cached authentication tokens, and service account passwords.
Responsible Disclosure
Confirming the exposure belonged to EY required meticulous detective work. DNS SOA record lookups ultimately pointed to ey.com, revealing the organization behind the misconfigured Azure storage. Rather than downloading the entire file, which would constitute a felony, the researcher analyzed the first kilobytes to confirm file integrity and format authenticity. Researchers immediately ceased technical investigation and began attempting to contact the security team through LinkedIn and other channels since no formal vulnerability disclosure program was readily available.
EY’s incident response proved exemplary. Security leadership acknowledged the report without defensiveness, initiated rapid triage, and completed full remediation within one week. The firm demonstrated the professionalism and technical competency that should characterize incident response for organizations handling sensitive financial data.
Cloud Misconfigurations
The incident underscores a fundamental vulnerability in modern cloud architecture: the gap between infrastructure complexity and human oversight. Cloud platforms prioritize convenience over security defaults. A single misconfigured Access Control List (ACL) changing permissions from private to public transforms an entire terabyte-scale backup into a publicly accessible goldmine for threat actors.
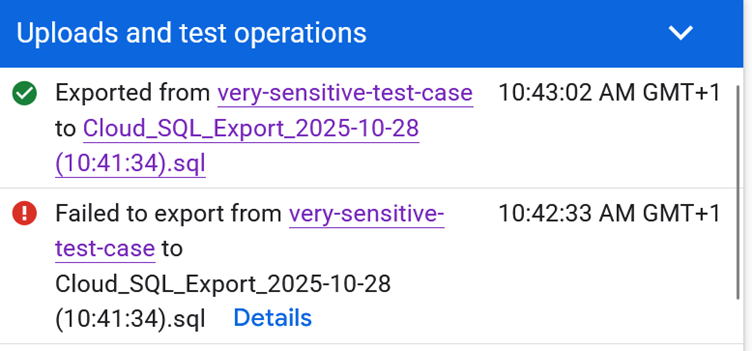
Modern cloud platforms make it trivially easy to export and backup your database. A few clicks, select your database, choose a destination bucket, and you're done. The export happens automatically in the background. But here's where it gets dangerous: one wrong click, one typo in a bucket name, and suddenly your private data is sitting in a public bucket. You meant to export to company-internal-backups but accidentally typed company-public-assets. Or you created a new bucket for the export, forgot to set it to private, and the cloud provider defaults to public.
The real danger isn’t sophisticated attackers specifically targeting organizations; it’s the massive distributed scanning infrastructure that never sleeps, continuously sweeping the internet’s entire IPv4 space to identify exposed data buckets within seconds. Previous incidents illustrate the urgency. A fintech company fell victim to ransomware after an engineer temporarily exposed a backup to public access for five minutes. During that narrow window, distributed scanners identified and exfiltrated the entire database.
Organizations cannot defend what they don’t know they own. Attack Surface Management has evolved from an optional security enhancement to an essential infrastructure necessity. Continuous, automated adversarial visibility matching the scanning capabilities threat actors deploy represents the only viable defense against cloud misconfiguration catastrophes. EY’s experience demonstrates that even the most resourced organizations remain vulnerable without relentless oversight of their expanding attack surface.





