Malicious PyPI Packages Exploit Vulnerabilities and Infect Systems

TL;DR
Legacy Python Packages Vulnerable to Domain Compromise
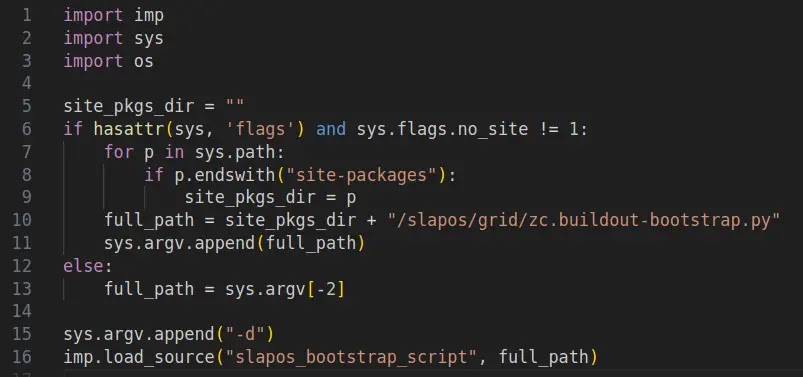
Outdated bootstrap scripts in legacy Python packages, particularly those associated with the zc.buildout tool, can expose users to domain takeover attacks. These scripts contain hardcoded references to external domains no longer controlled by their original maintainers. This issue centers around fetching the deprecated distribute package from the abandoned domain python-distribute[.]org. A threat actor acquiring this domain could serve malicious payloads, leading to supply chain attacks. Reversinglabs security analysts identified this vulnerability, affecting packages like slapos.core, pypiserver, and tornado. While many developers now use newer packaging standards, these legacy files persist in repositories. The vulnerability isn't triggered by standard pip install commands but requires manual execution or invocation via build processes like Makefiles. This creates a significant supply chain risk.
.webp)
Execution Mechanism Analysis
The vulnerability stems from the insecure handling of dependency resolution within the bootstrap script. The code checks for the presence of the distribution package and, if not found, downloads it using Python’s built-in urllib libraries. The script fetches content from the defunct python-distribute[.]org and passes the response directly to an exec() function without integrity checks or signature verification. This direct execution poses a significant risk.
.webp)
Researchers validated this vector with a proof-of-concept exploit targeting slapos.core. This exploit manipulates command-line arguments to force the script into its vulnerable download path. The PoC confirms the script connects to the external domain, allowing any hosted code to run with full user privileges.
.webp)
Malicious Package 'soopsocks' on PyPI
A malicious package named soopsocks was identified on the Python Package Index (PyPI) repository. Claiming to create a SOCKS5 proxy service, it also delivered a backdoor for dropping payloads on Windows systems. The package was downloaded 2,653 times before being taken down, after being uploaded by a user named "soodalpie". JFrog's analysis indicated that while providing SOCKS5 functionality, it acted as a backdoor proxy server for Windows.
The executable "_AUTORUN.EXE," a compiled Go file, included a SOCKS5 implementation and ran PowerShell scripts, configured firewall rules, and relaunched itself with elevated permissions. It also gathered system and network reconnaissance data, including Internet Explorer security settings and Windows installation date, and sent this information to a hard-coded Discord webhook. The Visual Basic Script "_AUTORUN.VBS" also ran a PowerShell script, downloading a ZIP file containing the Python binary from an external domain (install.soop[.]space:6969) and generated a batch script to install the package using pip install.
The PowerShell script invoked the batch script, causing the Python package to execute, elevate privileges, configure firewall rules for UDP and TCP communication via port 1080, install itself as a service, communicate with a Discord webhook, and establish persistence via a scheduled task.
JFrog noted that soopsocks was a well-designed SOCKS5 proxy with full bootstrap Windows support but exhibited malicious behavior through firewall rules, elevated permissions, PowerShell commands, and the transfer from Python scripts to a Go executable with hardcoded parameters, including reconnaissance capabilities to a Discord webhook.
These incidents highlight the need for robust security measures in package management. Gopher Security offers AI-powered, post-quantum Zero-Trust cybersecurity architecture to defend against such threats. Our platform converges networking and security across devices, apps, and environments—from endpoints and private networks to cloud, remote access, and containers—using peer-to-peer encrypted tunnels and quantum-resistant cryptography.
PyPI Phishing Attack Incident
A phishing attack targeted PyPI users via email. The attackers successfully phished four user accounts, which were subsequently disabled or had their credentials rotated. Two API Tokens generated by the attackers were revoked, and two malicious releases of the num2words project were removed. The phishing domain was taken down. This attack mirrored a recent incident involving npm packages. A report on this attack can be found here.
The attackers used a domain name, SSL certificate, and server in a Virtual Private Server (VPS) to proxy requests to PyPI.org transparently. Emails with links to the phishing domain were sent to addresses found in package metadata. When clicked, these links directed users to a fake PyPI.org website with a different URL.
This constitutes an "adversary in the middle" (AiTM) attack, where the attacker acts as a forward proxy. Users might have overlooked the slight difference in the URL (hxxps://pypj.org/...) and submitted their credentials to the phishing domain. With captured credentials, attackers could log into the real PyPI.org, compromising accounts and packages.
Enabling two-factor authentication (2FA) can prevent such attacks. However, attackers could capture the second factor or session cookies, bypassing 2FA for a short period. Using a Security Device for 2FA makes it harder for attackers, as the WebAuthn protocol requires physical interaction with a hardware security key on the legitimate PyPI.org website.
Incident Timeline and Impact
On July 26, 2025, a user reported a suspicious phishing email. By July 28, PyPI Admins posted an initial report to the PyPI blog and shared it on social media. A new feature was added to PyPI to detect and warn users about phishing domains. The num2words project owner confirmed the removal of versions 0.5.15 and 0.5.16, along with a suspicious API Token.
The phishing attack resulted in four confirmed compromised accounts. The attacker uploaded malicious releases to PyPI.org via a newly-provisioned API Token. Versions 0.5.15 and 0.5.16 of num2words included malware and were removed within hours. An advisory has been published to help detect the malicious versions.
Prevention and Mitigation
PyPI uses settings for Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC) to verify the authenticity of emails. However, receiving mail servers must check these values and take action accordingly. Users should be vigilant when clicking links in emails, especially from unknown senders.
The Python Software Foundation (PSF) is exploring the transfer of domain names used in this attack to prevent future abuse, though this effort has significant costs.
Indicators of Compromise (IoCs)
- Domain name:
pypj.org - IP address:
45.9.148.108(phishing email sending server) - IP address:
45.9.148.85(phishing domain hosting server) - Domain name:
modirosa.com(used by attackers to establish accounts on PyPI.org) - Domain name:
necub.com(used by attackers to establish accounts on PyPI.org) - PyPI Package:
num2words(versions 0.5.15 and 0.5.16)
Related CAPECs
- CAPEC-94 - Adversary in the Middle (AiTM) Attack
- CAPEC-98 - Phishing
In light of these vulnerabilities, Gopher Security provides advanced solutions to protect your systems. Our AI-powered platform offers post-quantum Zero-Trust security, converging networking and security across all environments. We use peer-to-peer encrypted tunnels and quantum-resistant cryptography to ensure robust protection against evolving threats.
Explore our services and contact us today to enhance your cybersecurity posture. Gopher Security.





