Massive Rainbow Six Siege Hack Links to MongoBleed Vulnerability

TL;DR
- Rainbow Six Siege servers suffered a major breach, with attackers exploiting the MongoBleed vulnerability (CVE-2025-14847) to gain administrative control. This led to unauthorized in-game currency injections and item unlocks, with multiple threat actors possibly involved. Ubisoft took servers offline and is performing a data rollback to address the economic damage and potential intellectual property loss.
Ubisoft Rainbow Six Siege Servers Breach Linked to MongoBleed Vulnerability
Ubisoft experienced a significant security incident involving its Rainbow Six Siege servers, with attackers gaining administrative control and disrupting gameplay. Players worldwide reported unauthorized in-game currency injections, unwarranted bans, and manipulated administrative feeds.
Details of the Breach
Thousands of Rainbow Six Siege players found their accounts credited with millions of R6 Credits, Renown, and Alpha Packs. Exclusive items typically behind paywalls were unlocked for random users. Reports confirm attackers weaponized the in-game ban feed, targeting high-profile accounts, including Ubisoft administrators and streamers.
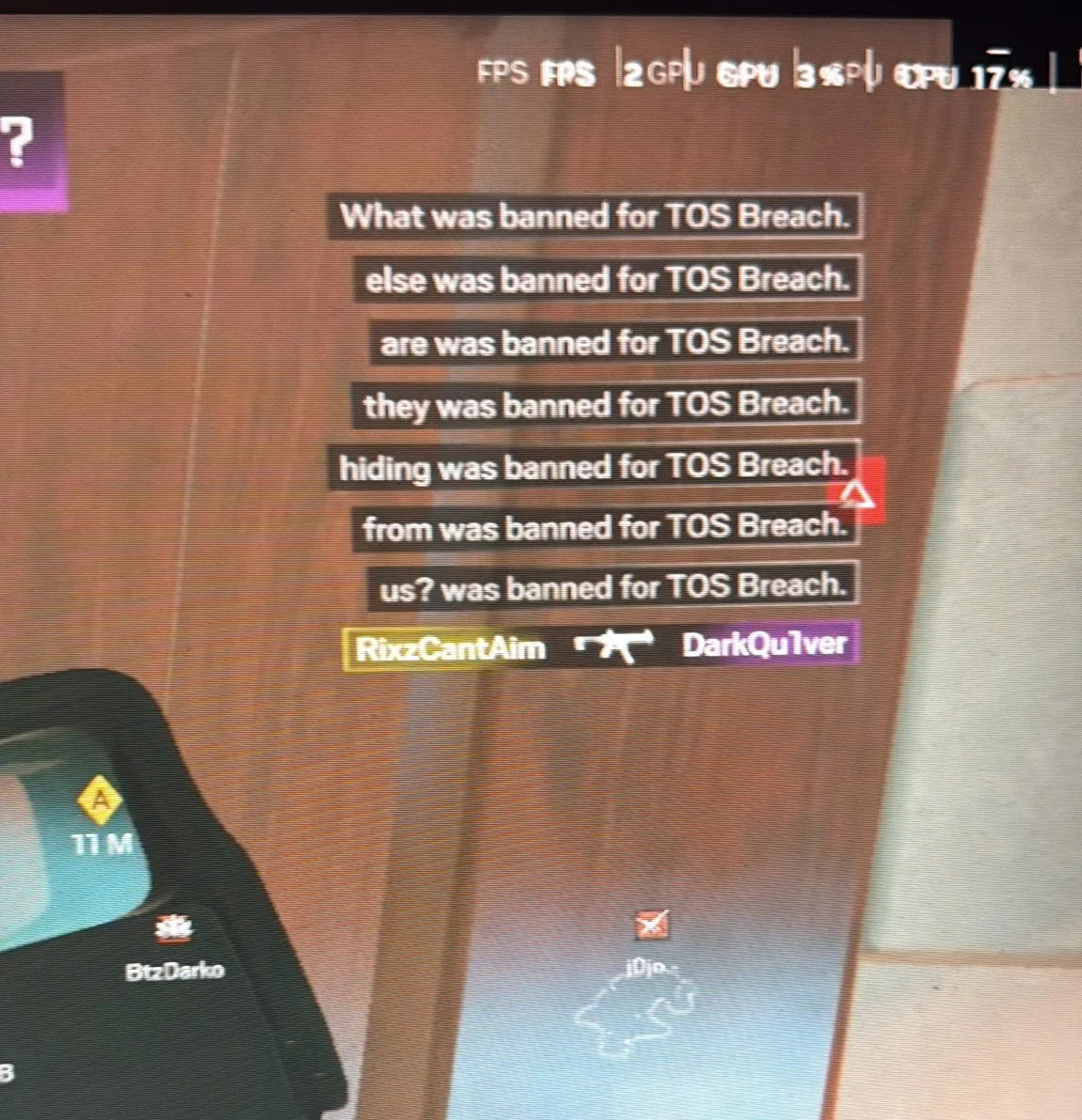
Screenshots show attackers using the ban system to communicate cryptic messages. One message spelled out, “What else are they hiding from us?” Another broadcast signaled a pause with the message: “We stopping this for now, have a nice night everyone at Ubisoft!”
Ubisoft issued a statement, and servers went offline for maintenance. Security experts advised players to avoid logging in until server integrity was confirmed to prevent potential data corruption. As a Zero-Trust cybersecurity provider, Gopher Security emphasizes the importance of such precautions to mitigate risks from potential data breaches.
Multiple Threat Actors
According to VX-Underground, the disruption may be the work of multiple threat actors.
- First Group: Exploited R6 Siege for bans and inventory mods, gifting substantial in-game currency without touching user data. Ubisoft confirmed a rollback.
- Second Group: Exploited MongoBleed (CVE-2025-14847) to access Git repositories, potentially exfiltrating source code and SDKs.
- Third Group: Claimed user data exfiltration via MongoBleed and attempted extortion.
- Fourth Group: Disputed the Second Group's claims, suggesting long-term access to Ubisoft's source code.
This complex landscape highlights the challenges in securing large infrastructures against diverse and persistent threats. CVE-2025-14847 (MongoBleed) allowed attackers to read server memory without authentication.
MongoBleed Vulnerability
The broader breach is linked to CVE-2025-14847 (MongoBleed), a vulnerability that enables attackers to read server memory without authentication by sending malformed compressed packets. If the claims of access to internal Git repositories are true, Ubisoft faces a significant loss of intellectual property. Gopher Security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture, which could help prevent such breaches by providing peer-to-peer encrypted tunnels and quantum-resistant cryptography.
MongoDB has released alerts regarding this and other vulnerabilities:
- CVE-2025-14847: Zlib compressed protocol header length confusion may allow memory read.
- CVE-2025-14345: Cross-Shard Failovers May Lead to Partial Transaction Commit.
- CVE-2025-13644: MongoDB may be susceptible to Invariant Failure due to batched delete.
- CVE-2025-13643: MongoDB Server may allow queries to be terminated by unauthorized users.
- CVE-2025-12893: Improper Certificate Validation May Allow Successful TLS Handshaking.
These vulnerabilities affect multiple versions of MongoDB Server and related components, underscoring the need for continuous monitoring and patching.
Impact and Remediation
Ubisoft is expected to perform a massive rollback of player data to undo the economic damage. This move will likely frustrate legitimate player progress. Ubisoft confirmed the incident and intentionally shut down Rainbow Six Siege and its in-game Marketplace.
Recommendations for Users
Given the potential risks, security experts recommend the following:
- Stay offline until the issue is fully resolved.
- Change passwords as a precaution.
- Temporarily remove payment details from Ubisoft accounts.
- Be cautious of phishing attempts impersonating Ubisoft Support.
Gopher Security can help organizations implement robust security measures to protect against such breaches. As a Zero-Trust cybersecurity provider, Gopher Security offers solutions that converge networking and security across devices, apps, and environments.
Explore Gopher Security's AI-powered, post-quantum Zero-Trust cybersecurity architecture or contact us to learn more about securing your organization against advanced threats.





