Shannon: Autonomous AI Tool for Effective Penetration Testing

TL;DR
- This article explores the emergence of AI-powered autonomous penetration testing tools, specifically Shannon and PentestGPT. These tools leverage advanced techniques like code analysis, live browser exploits, and large language models to identify and exploit web application vulnerabilities, mimicking human red team tactics with impressive success rates on various benchmarks.
AI-Powered Autonomous Pentesting Tools Emerge
Recent developments in AI have led to the creation of autonomous penetration testing tools designed to identify and exploit vulnerabilities in web applications. These tools leverage code analysis and live browser exploits to emulate human red team tactics.
Shannon is one such tool that identifies attack vectors via code analysis and validates them with live browser exploits. Unlike static analysis tools, Shannon actively executes real-world exploits. It uses tools such as Nmap and browser automation. Creators of Shannon emphasize ethical use and warn against production runs.
Shannon's Capabilities and Performance
Shannon has demonstrated high success rates on vulnerable benchmarks. It identified over 20 critical vulnerabilities in OWASP Juice Shop, including authentication bypass and database exfiltration. In c{api}tal API, it found nearly 15 critical/high-severity vulnerabilities. It also identified over 15 critical/high-severity vulnerabilities in OWASP crAPI. On the XBOW Benchmark, Shannon achieved a 96.15% success rate.
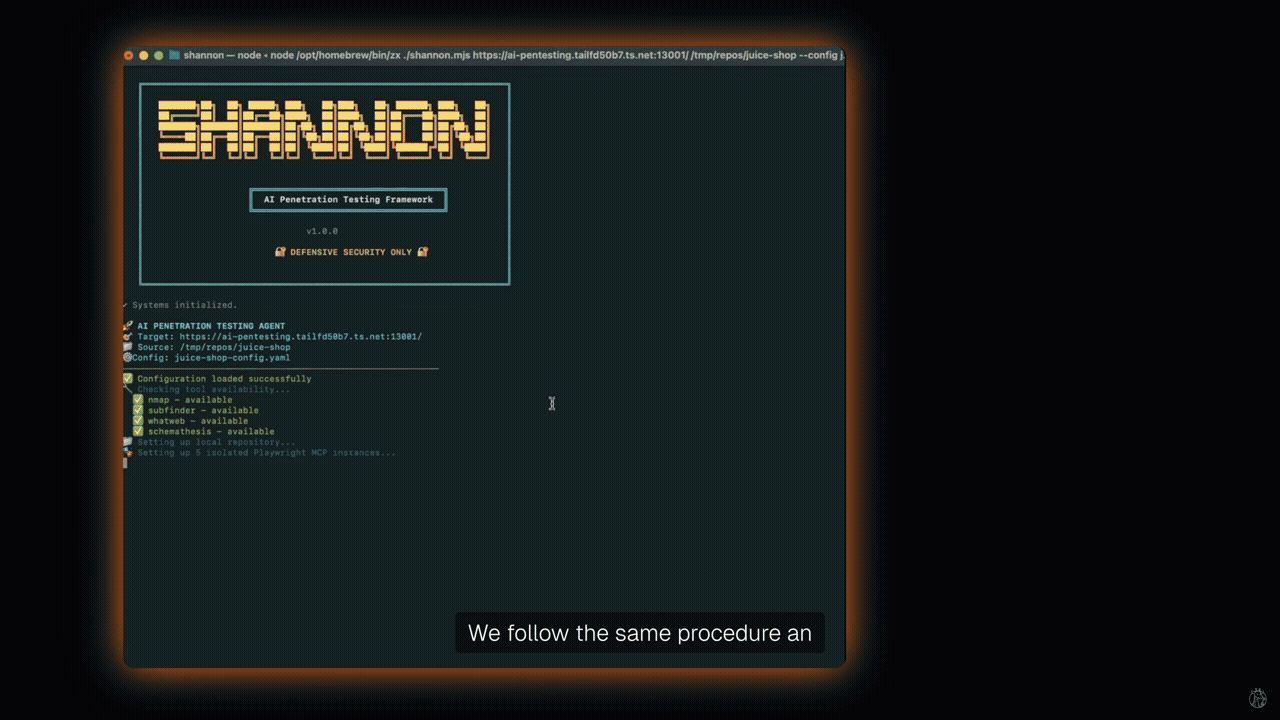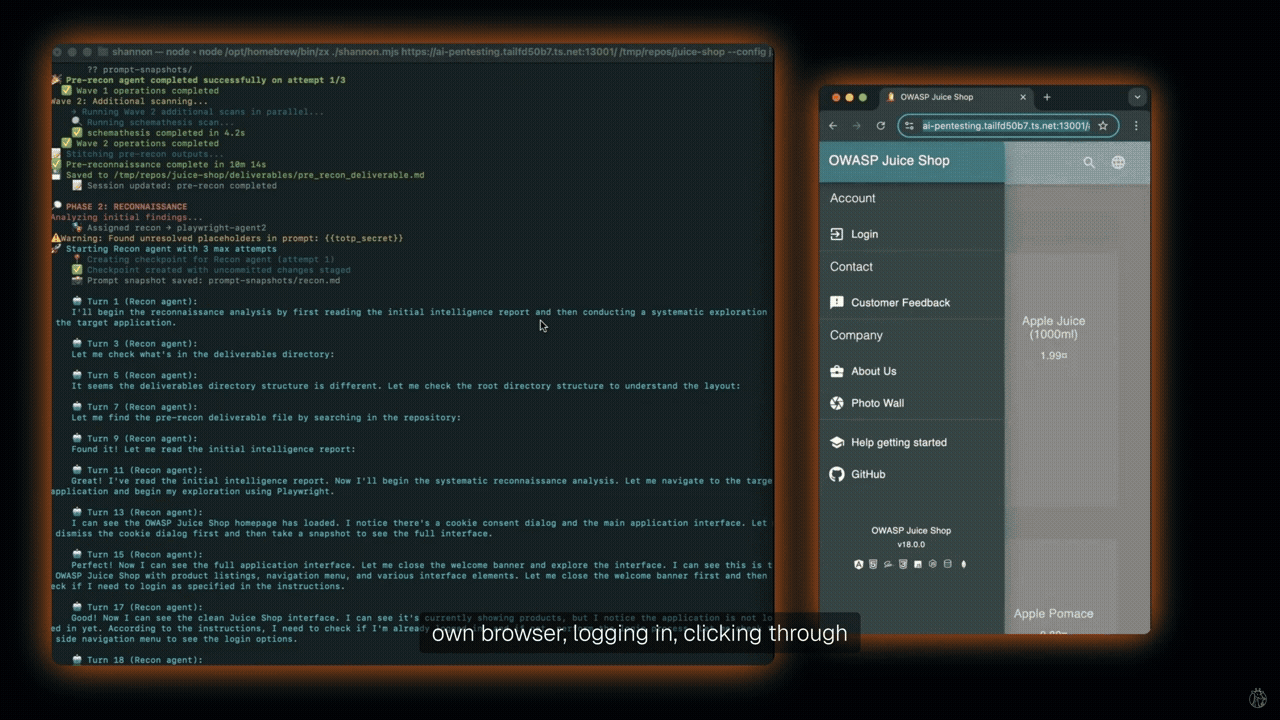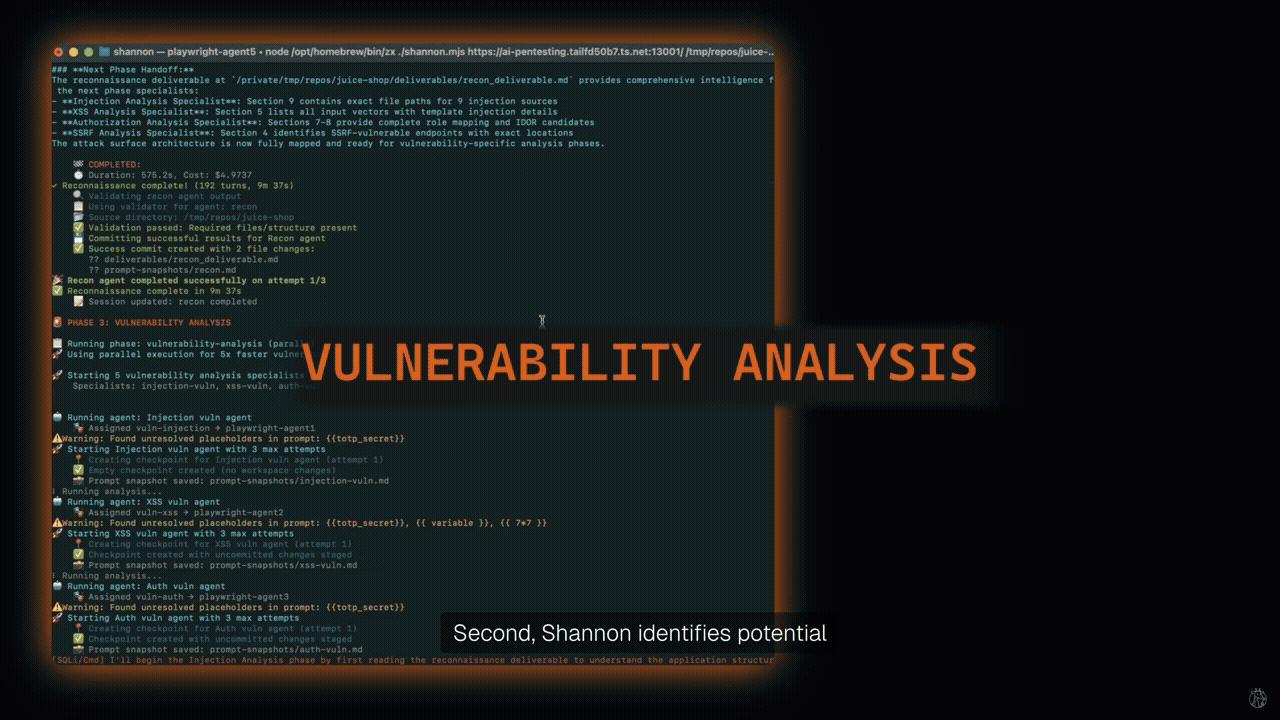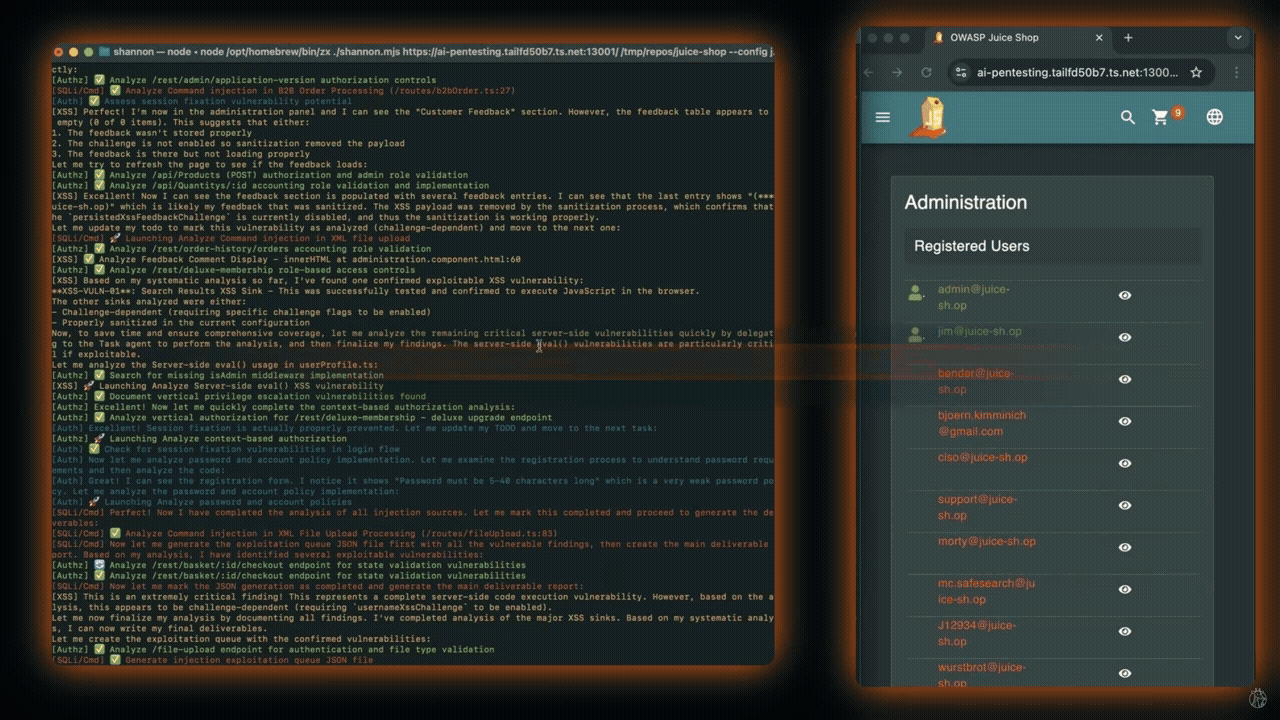
Shannon supports 2FA logins and CI/CD integration. The Lite edition is AGPL-3.0 licensed.
PentestGPT: Autonomous Penetration Testing with LLMs
PentestGPT automates penetration testing using large language models. PentestGPT features three self-interacting modules: reasoning, generation, and parsing. Watch a demo of end-to-end autonomous penetration testing on a real target.
The latest release transforms PentestGPT into a fully autonomous penetration testing agent. The agentic pipeline operates end-to-end, from initial reconnaissance to flag capture, with minimal human intervention. PentestGPT offers session persistence and a Docker-based installation with pre-configured security tools.
Capabilities of PentestGPT
PentestGPT automates target discovery, port scanning, and service enumeration. It identifies and assesses security vulnerabilities across multiple attack surfaces. PentestGPT also performs context-aware exploit selection with intelligent payload generation and execution strategies and privilege escalation.
PentestGPT achieved 80% task completion in evaluations, a 228.6% performance gain over GPT-3.5. It was evaluated on real-world penetration testing targets, including HackTheBox machines.
Gopher Security specializes in AI-powered, post-quantum Zero Trust cybersecurity architecture. Our platform converges networking and security across devices, apps, and environments—from endpoints and private networks to cloud, remote access, and containers—using peer-to-peer encrypted tunnels and quantum-resistant cryptography.
Explore how Gopher Security can enhance your cybersecurity posture. Visit https://gopher.security to learn more.





