Top Cloud Security Vulnerabilities and Fixes for Confidential Data
TL;DR
- Researchers have discovered RMPocalypse, a hardware vulnerability affecting AMD's confidential computing technology used by major cloud providers. This flaw can bypass security mechanisms, potentially exposing sensitive data. The vulnerability targets the Reverse Map Table (RMP) during virtual machine startup, allowing for attacks like attestation forgeries and code injection, highlighting a critical gap in current cloud data protection.
Vulnerability in Confidential Cloud Environments
ETH Zurich researchers have uncovered a vulnerability, named RMPocalypse, that could allow attackers to bypass the protection mechanisms of confidential computing environments. This would enable them to access secure data areas and potentially read or steal confidential information. This vulnerability affects areas of the cloud specifically secured for handling confidential data.

RMPocalypse is a hardware issue exploitable through straightforward attack methods with potentially serious impact. The Common Vulnerability Scoring System (CVSS) gives RMPocalypse a score of 6.0. More details can be found in the Proceedings of the 2025 ACM SIGSAC Conference on Computer and Communications Security (DOI: 10.1145/3719027.3765233, rmpocalypse.github.io/rmpocalypse-CCS2025.pdf).
AMD Security Technology Affected
The discovered security vulnerability specifically impacts areas and workloads protected by specialized security technology from AMD. Their technology is frequently used in the confidential computing environments of major cloud providers such as Microsoft Azure, Google Cloud, and Amazon Web Services. This widespread use increases the significance of RMPocalypse because the vulnerability could undermine trust in the security of cloud services.
Technical Details of RMPocalypse
The ETH researchers found they could regularly bypass the protective mechanisms of confidential computing environments. They succeeded in gaining access to all tested workloads with a success rate of 100%. RMPocalypse exploits a vulnerability in the memory management of modern processors—specifically, in Reverse Map Table (RMP). This mechanism is intended to ensure that only authorized programs can use confidential data.
The technology used by AMD to protect highly confidential data in the cloud is called SEV-SNP—short for Secure Encrypted Virtualization with Secure Nested Paging. It forms the technical foundation of confidential computing environments, ensuring that sensitive information remains protected even while it is being processed. SEV-SNP automatically protects data—during storage, transmission and processing—and ensures that even cloud providers cannot access it. The technology provides robust protection for virtual machines (VM), which serve as digital workspaces in the cloud, shielding them from unauthorized access.
Vulnerability During Virtual Machine Start-Up
The ETH Zurich researchers discovered that part of the security mechanism—the so-called Reverse Map Table (RMP)—is not fully protected when a virtual machine is started. This gap could allow attackers with remote access to bypass certain protective functions and manipulate the virtual machine environment.
The researchers showed that this vulnerability can be exploited to activate hidden functions (such as a debug mode), simulate security checks (so-called attestation forgeries) and restore previous states (replay attacks)—and even to inject foreign code. By theoretically analyzing and documenting the attack, they helped to identify and fix the vulnerability before third parties could actually exploit it.
Top Cloud Security Vulnerabilities
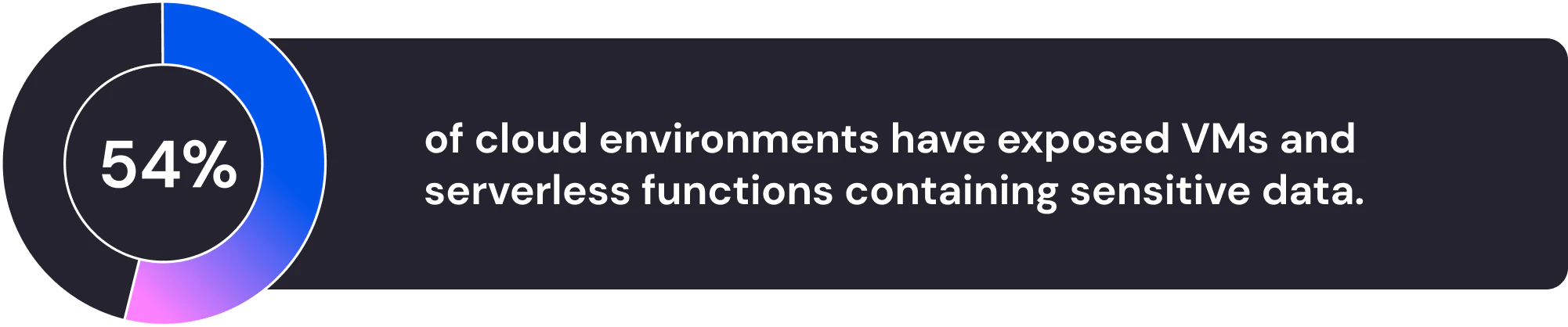
Cloud security vulnerabilities are weaknesses in a cloud computing environment that attackers exploit to gain unauthorized access, steal data, or disrupt services. According to Wiz Research’s 2025 findings, 54% of cloud environments face vulnerabilities due to serverless functions and exposed virtual machines (VMs) that contain critical data. Verizon's 2025 Data Breach Investigations Report indicates that the exploitation of vulnerabilities has seen another year of growth as an initial access vector for breaches, reaching 20%.
The most common cloud security vulnerabilities include:
- Misconfigurations
- Lack of visibility
- Poor access management
- Insider threats
- Unsecured APIs
- Zero-days
- Shadow IT
- Lack of encryption
- Inadequate segmentation
- Vulnerable dependencies
- Deficient logging and monitoring
Misconfigurations
Misconfigurations are errors in the security settings of cloud applications and systems. Common ones include open ports for outbound server traffic, overprivileged identities, a lack of monitoring, unsecured storage (like open S3 buckets), the use of default passwords and credentials, and third-party misconfigurations.
Wiz Research found a cryptojacking campaign in June 2025 that a group called JINX-0132 was conducting, exploiting misconfigurations in DevOps tooling, such as Docker API and Gitea, to deploy its software. Mitigation steps include using a cloud security posture management tool, implementing least privilege access, and incorporating IaC.
Lack of Visibility
Enterprises often mix and match technologies from various cloud service providers, resulting in a lack of visibility that can be detrimental to identifying, contextualizing, prioritizing, and mitigating vulnerabilities.
Toyota Japan unknowingly exposed the personal and vehicle data of 2.15 million customers for almost 10 years due to a cloud misconfiguration. Mitigation steps include implementing centralized logging and monitoring solutions, employing a cloud native application protection platform, and setting up alerts for unusual activities.
Poor Access Management
Digital identities vastly outnumber human identities in cloud environments, making them alluring targets for threat actors. Access management vulnerabilities include a lack of MFA, poor password and credential hygiene, misconfigured policies, and a lack of standardized, automated identity lifecycles.
In 2024, attackers accessed email addresses, hashed passwords, and other credentials from Dropbox Sign using an access vulnerability within an automated system configuration tool. Mitigation steps include implementing least privilege access, using role-based access control, and adopting MFA and single sign-on solutions.
Insider Threats
Insider threats are vulnerabilities that are due to individuals or entities that already have some degree of access to an enterprise’s IT environment. These threats result from accidental errors, negligence, or malicious intent.
The 2019 Capital One breach, which compromised the data of over 100 million Americans and Canadians, was a result of actions that a former Amazon engineer took. Mitigation steps include monitoring employee activity, implementing strict access controls, and conducting background checks.
Unsecured APIs
Cloud APIs facilitate communication and data exchange between cloud software and applications. API vulnerabilities are a prominent attack vector for threat actors.
The attack vector for the Optus data breach in 2022 was an unsecured, publicly available API that didn’t require authentication protocols to access. Mitigation steps include implementing strong authentication and authorization mechanisms and using rate limiting and other controls to prevent API abuse.
Zero-Days
Zero-day vulnerabilities are those that your team hasn’t yet patched. They occur when threat actors exploit unidentified and unknown security vulnerabilities.
In 2023, [glitches in Microsoft Windows and Office products](https





