January 2026 Patch Tuesday: Key Updates and Critical Fixes

TL;DR
Microsoft January 2026 Patch Tuesday Analysis
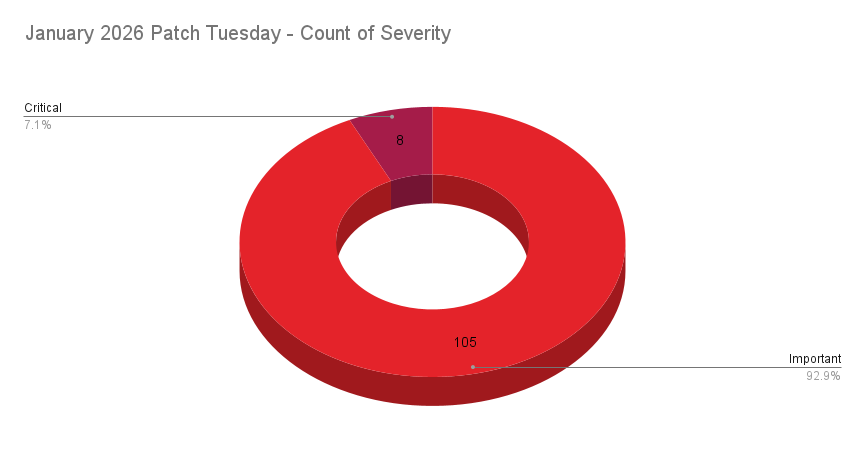
Microsoft has released its January 2026 security update, addressing a total of 114 security flaws. This includes one actively exploited vulnerability and eight rated as critical.
Vulnerability Statistics
- Total CVEs Addressed: 114
- Critical: 8
- Important: 106
- Actively Exploited: 1 (CVE-2026-20805)
- Privilege Escalation: 58
- Information Disclosure: 22
- Remote Code Execution: 21
- Spoofing: 5
Actively Exploited Vulnerability: Desktop Window Manager Information Disclosure
CVE-2026-20805 is an information disclosure vulnerability in the Desktop Window Manager (DWM). It has a CVSS score of 5.5 and is actively being exploited in the wild.
Microsoft stated that the vulnerability allows a local, authenticated attacker to disclose a section address from a remote ALPC (Advanced Local Procedure Call) port, which is user-mode memory. Microsoft Threat Intelligence Center (MTIC) and Microsoft Security Response Center (MSRC) have been credited with identifying and reporting this flaw.
According to Adam Barnett, lead software engineer at Rapid7, DWM's role in drawing everything on a Windows display makes it a frequent target. He noted that exploitation leads to improper disclosure of an ALPC port section address. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the flaw to its Known Exploited Vulnerabilities (KEV) catalog, requiring Federal Civilian Executive Branch (FCEB) agencies to apply fixes by February 3, 2026.
Secure Boot Certificate Expiration
CVE-2026-21265 is a security feature bypass vulnerability affecting Secure Boot Certificate Expiration. It has a CVSS score of 6.4. The vulnerability could allow an attacker to undermine the security mechanism that ensures firmware modules come from a trusted source.
Microsoft announced that three Windows Secure Boot certificates issued in 2011 will expire in June 2026. Customers are urged to update to their 2023 counterparts to avoid disruption. The expiring certificates include:
- Microsoft Corporation KEK CA 2011 (June 2026)
- Microsoft Windows Production PCA 2011 (October 2026)
- Microsoft UEFI CA 2011 (June 2026)
Microsoft Office Remote Code Execution Vulnerabilities
CVE-2026-20952 and CVE-2026-20953 are remote code execution (RCE) vulnerabilities affecting Microsoft Office. They have a CVSSv3 score of 8.4 and are rated as critical. An attacker could exploit these flaws by sending a malicious Microsoft Office document to a target. Successful exploitation would grant code execution privileges.
CVE-2026-20944 is another RCE vulnerability, this time affecting Microsoft Word. A remote threat actor can exploit an out-of-bounds read vulnerability to execute code locally by sending a malicious file and convincing a victim to open it.
The Absolute Security Blog notes that these vulnerabilities can be exploited via the Preview Pane in Outlook, requiring no user interaction beyond previewing the document.
Windows NTFS Remote Code Execution Vulnerabilities
CVE-2026-20840 and CVE-2026-20922 are RCE vulnerabilities affecting Windows New Technology File System (NTFS). Both have CVSSv3 scores of 7.8 and are rated as important. Microsoft assessed both of these flaws as “Exploitation More Likely.” According to Microsoft, both these flaws stem from heap-based buffer overflows which can be exploited to execute arbitrary code on an affected system. Any authenticated attacker can exploit these flaws, regardless of privilege level.
Additional Vendor Updates
Alongside Microsoft, multiple vendors have released security updates:
Gopher Security Recommendations
Given the nature of these vulnerabilities, particularly the actively exploited CVE-2026-20805 and the Office RCEs, it is crucial to apply the relevant patches promptly. Organizations should prioritize patching Office applications and address the scope-changing Windows fixes to prevent privilege escalation.
Consider leveraging Gopher Security's AI-powered, post-quantum Zero-Trust cybersecurity architecture to enhance your defenses. Our platform converges networking and security, offering peer-to-peer encrypted tunnels and quantum-resistant cryptography across all environments to mitigate potential threats.
For more information on how Gopher Security can help protect your organization, please contact us.