
Cryptographic Agility for Contextual AI Resource Governance
Master cryptographic agility for AI resource governance. Learn how to secure Model Context Protocol (MCP) with post-quantum security and granular policy control.
Cutting-edge insights on post-quantum cryptography, AI cybersecurity, and zero-trust architectures. The Gopher Security Blog explores advanced security solutions for Model Context Protocol (MCP), homomorphic encryption, and privacy-preserving technologies to future-proof your enterprise against emerging quantum and AI threats.

Master cryptographic agility for AI resource governance. Learn how to secure Model Context Protocol (MCP) with post-quantum security and granular policy control.

Discover how to secure AI infrastructure with post-quantum cryptography and agile transport security for Model Context Protocol (MCP) deployments.

Discover how to secure AI orchestration workflows using post-quantum cryptography and AI-driven anomaly detection for Model Context Protocol (MCP) environments.

Learn how to protect AI agents from quantum threats using post-quantum cryptography, mcp security, and context-aware access control.

Learn how lattice-based PQC secures Model Context Protocol (MCP) transport layers against quantum threats using NIST standards like ML-KEM and ML-DSA.
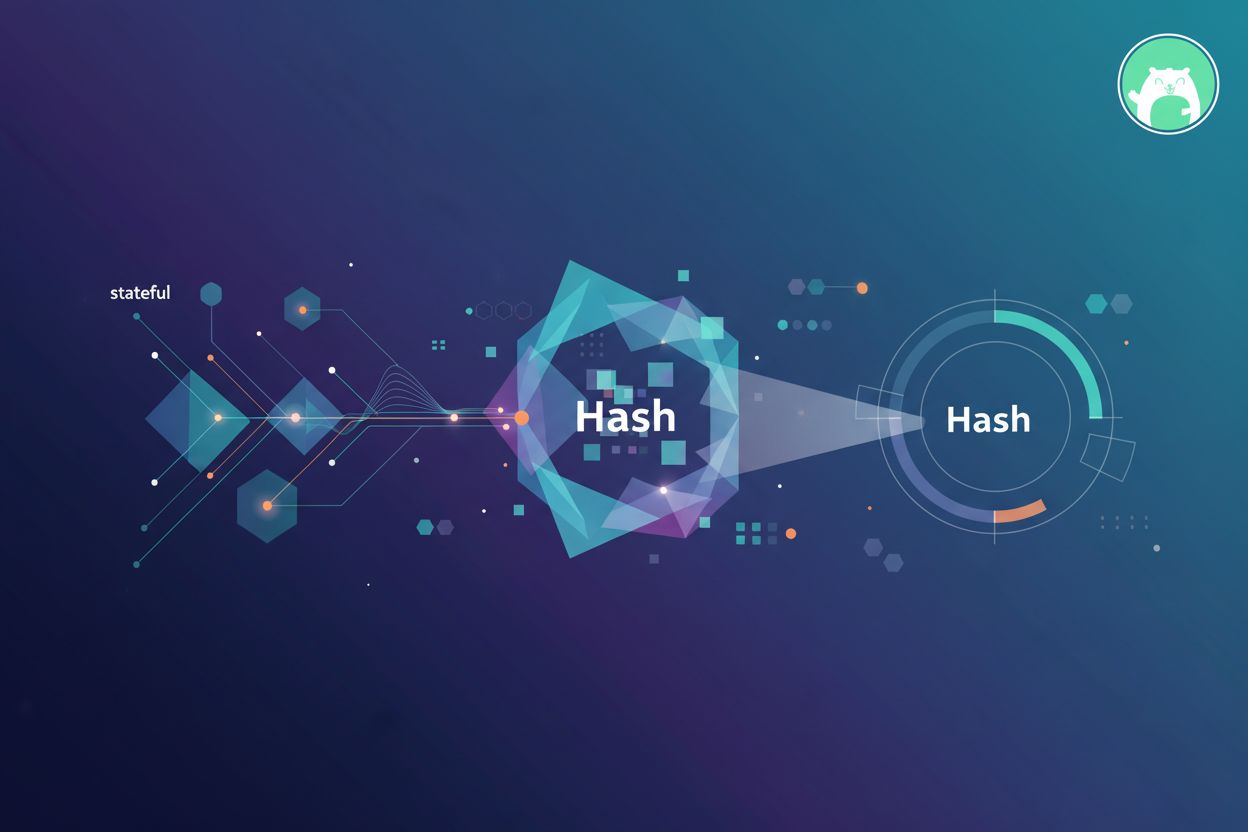
Learn how stateful hash-based signatures like XMSS and LMS provide quantum-resistant security for AI Model Context Protocol deployments and data integrity.
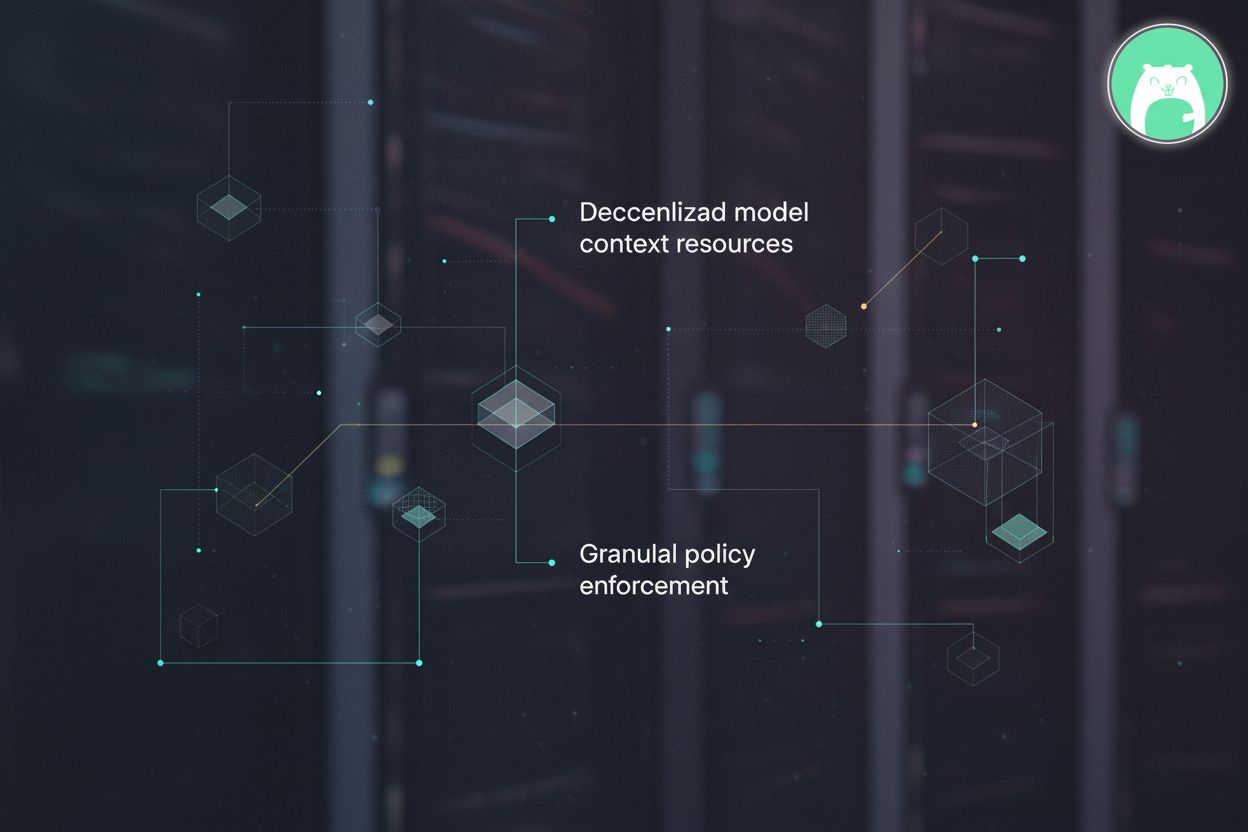
Secure your Model Context Protocol (MCP) deployments with granular policy enforcement and post-quantum cryptography. Prevent tool poisoning and puppet attacks.
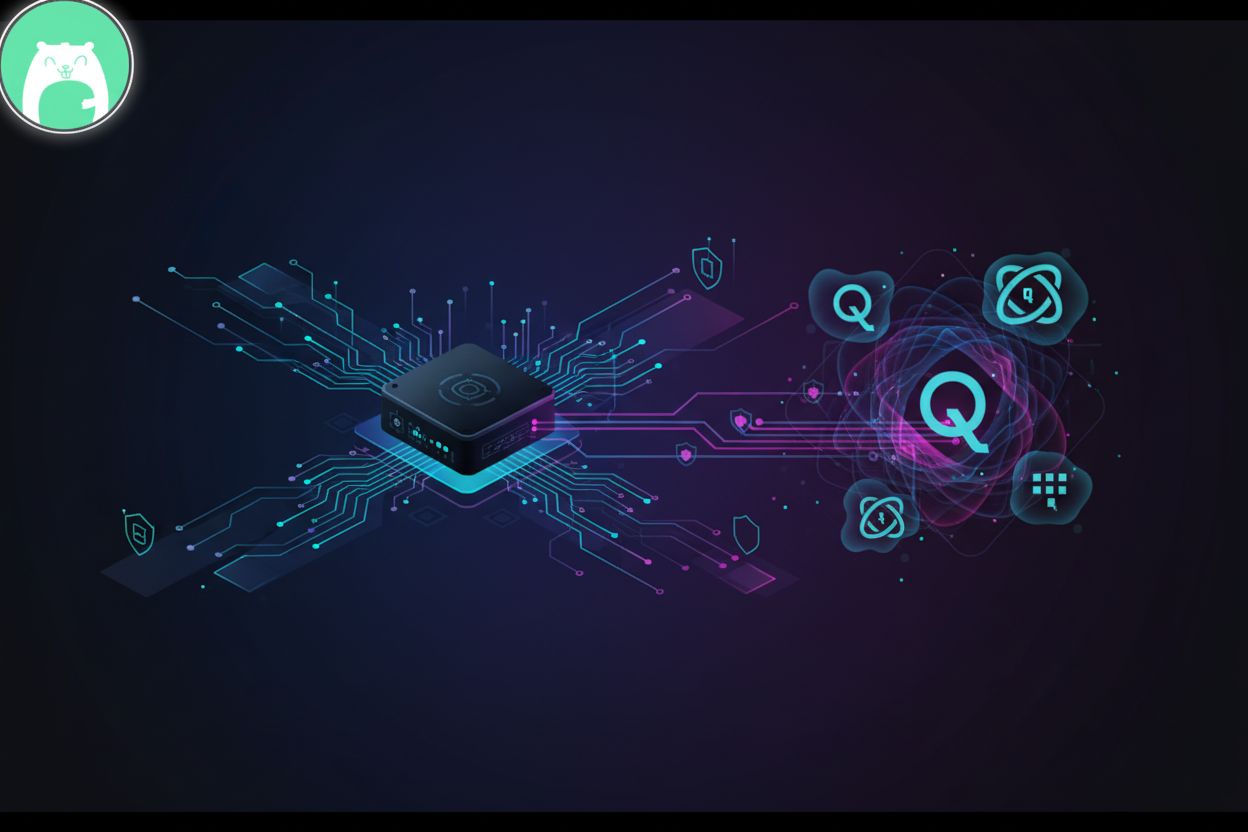
Learn how to integrate Quantum-Safe HSMs with Model Context Protocol (MCP) to secure AI infrastructure against Shor's algorithm and context injection.

Learn how to secure federated AI agents with quantum-resistant IAM, lattice-based cryptography, and context-aware access control for MCP deployments.